how to check if my SMTP is safe
With the increasing number of ransomware attacks in the 2020s
email, our main communication channel on the Internet, is it safe?
The SMTP servers are a particularly sensitive infrastructure.
They can spread email messages on our behalf,
that our counterparts accept as coming from trusted senders
because they are correctly authenticated by the sending server.
SMTP servers are a particularly sensitive infrastructure.
They spread email messages on our behalf,
that our counterparts accept as coming from trusted senders
because they are properly authenticated by the sender’s SMTP server.
What happens if someone else uses your SMTP server?
How to check if my SMTP server is safe?
The use of sensitive infrastructures on the Internet
requires a high level of protection to prevent abuse.
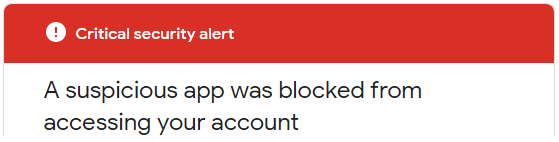
If you try to send messages via smtp.gmail.com
you’ll be blocked and receive this “Critical security alert”:
Less secure app blocked
Google blocked the app that you were trying to use
because it doesn't meet our security standards. [...]The only alternative is to use OAuth2, a protocol that doesn’t share password data
but instead uses authorization tokens to prove identity.
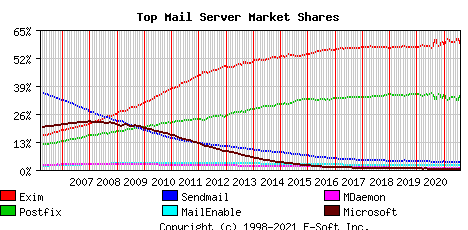
The most used mailservers on the Internet (August 2021 data) are:
Exim (58%), Postfix (35%), Sendmail (4%)
To continue using your own mailserver
reducing the risk of being hacked,
the minimum requirements to check are:
-
accept only secure authentication
username and password must be transmitted via secure connections,
typically port 587+TLS or port 25+TLS or port 465+SSL
plain text sensitive data communications are disabled -
there must be a check on the “Mail-From” address (the sender),
only those you have authorized will be able to pass -
configure Fail2ban to block all external attacks
to prevent attempts to force your protections.
In particular Fail2ban should block all repeated attempts:
- to log in with the wrong username or password
- to send emails with an unauthorized sender
- to interrupt the smtp connection during the authentication process
(multiple broken connections make the smtp service unavailable for legitimate users)
The block usually occurs between three and ten attempts
and bans the source IP for three to twenty-four hours.
It is quite easy to test these points and decide whether or not
your smtp infrastructure requires a security upgrade.
Fail2ban protects your server against BruteForce/DDOS attacks.
It works as if when a stranger knocks on the door,
after a certain number of strokes, the door disappears.

A testimony from Hacker News:
I manage my own mailserver since several years and I think many others here
use solutions like Mail-in-a-box, mailcow, Mailu, etc
Until Corona I never had big problems with my mailserver but in the last weeks
I got very big incoming Traffic - that was too much for my server and i had to manually reboot it every time ...
[...] Edit: I changed my fail2ban settings and found out I was primarily targeted
by brute force attacks which I should be able to protect against with tools like fail2banFail2ban is a log-parsing application that monitors system logs
looking for the symptoms of an automated attack.
When an abuse attempt is located, using the defined parameters,
Fail2ban adds a new rule to the firewall (iptables or firewalld)
to block the IP address of the attacker, either for a set amount of time, or permanently.
Fail2ban can also alert you through email that an attack is occurring.
Fail2ban is primarily focused on SSH attacks, although it can be further configured
to work for any service that uses log files and can be subject to a compromise.
It is widely used. Searching for it on Google, it’s easy to find
configuration examples for protecting mail servers.