DKIM domain for DMARC
How DKIM domain alignment affects DMARC authentication ?
DMARC (Domain-based Message Authentication, Reporting and Conformance),
is an email authentication standard, developed to combat spoofed domain mail.
In the chapter “3.1. Identifier Alignment” it says:
Email authentication technologies authenticate various (and
disparate) aspects of an individual message. For example, [DKIM]
authenticates the domain that affixed a signature to the message,
while [SPF] can authenticate either the domain that appears in the
RFC5321.MailFrom (Mail-From) portion of [SMTP] or the RFC5321.EHLO/
HELO domain, or both. These may be different domains, and they are
typically not visible to the end user.
DMARC authenticates use of the RFC5322.From domain by requiring that
it match (be aligned with) an Authenticated Identifier.
-- https://tools.ietf.org/html/rfc7489#section-3.1It simply means:
when a sender authenticates their email using SPF and/or DKIM,
at least one of the domains must align with the sending From domainIt was not clear to us if a message could fail SPF or DKIM check
and still pass the DMARC authentication.
We tested it using a tool available to everyone: a Gmail mailbox.
To see the outcome, open the message and select “Show original”:
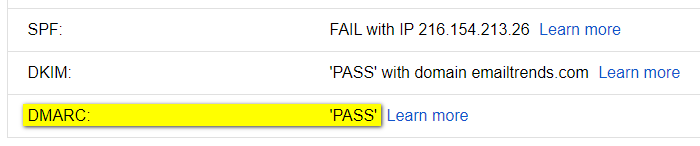
Test 1 - forwarded message: spf-fail, dkim-pass (aligned)
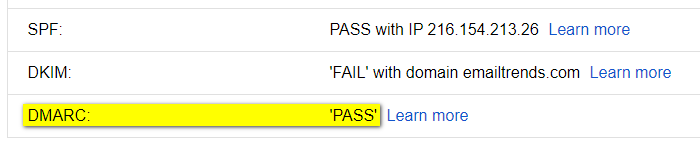
Test 2 - broken dkim key: dkim-fail, spf-pass (aligned)
The result is evident, the message passes DMARC authentication if it occurs:
SPF and domain alignment <OR> DKIM and domain alignment
To pass the DMARC check, in some cases it is therefore important to validate the DKIM signature:
the signing domain (d=example.com) must be aligned with the From domain.
Examples of “DMARC-PASS” results that otherwise would not have worked:
Case 1 - forwarding breaks the SPF authentication
-
SPF-FAIL: SPF Authentication checks will mostly fail,
because a new entity, not included in the original sender’s SPF Record, sends the forwarded email -
DKIM-PASS (aligned): Email forwarding does not affect the DKIM signature
Result: DKIM alignment allows the message to pass the DMARC check.
Case 2 - the SPF domain provided by the ESP (Email Service Provider)
CANNOT be aligned with the From domain
-
SPF~PASS (NOT aligned): SPF Authentication fails domain alignment,
since the domain used by the ESP within the Mail-From address is different by the one in the From sender -
DKIM-PASS (aligned): DKIM signature uses the same domain of the From sender
Result: DKIM alignment allows the message to pass the DMARC check.