Subsections of email authentication advanced
<spf> alignment for dmarc

spf domain alignment for dmarc
DMARC is an email authentication standard, developed to combat spoofed domain mail.
For domain alignment it requires that:
when a sender authenticates their email using SPF and/or DKIM,
at least one of the domains must align with the sending From domain
To get it within SPF (Sender Policy Framework), you deal with two domains:
- the sending From address, that is visible to the recipients
- the Mail-From address (also called “envelope sender” or “return-path”), that is hidden
DMARC allows two types of SPF alignment: relaxed alignment and strict alignment.
If you do not specify strict alignment, relaxed alignment is assumed as the default.
relaxed alignment
With relaxed alignment, only the root domain of the Mail-From address must match the root domain of the From address.
Relaxed alignment allows any subdomain to be used and still meet the domain alignment requirement.
example:
-
if your Mail-From domain is mail.abc.com and your From domain is abc.com,
your email will pass SPF alignment (the root domains “abc.com” match)
-
if your Mail-From domain is abc.mail.com and your From domain is abc.com,
your email will NOT pass SPF alignment (the root domains “mail.com” and “abc.com” do not match)
strict alignment
With strict alignment, the domain of the Mail-From address must match exactly the domain of the From address.
example:
-
if your Mail-From domain is mail.abc.com and your From domain is mail.abc.com,
your email will pass SPF alignment (the domains “mail.abc.com” match)
-
if your Mail-From domain is mail.abc.com and your From domain is abc.com,
your email will NOT pass SPF alignment (the domains “mail.abc.com” and “abc.com” do not match)
<spf> check online
<dkim> alignment for dmarc

dkim domain alignment for dmarc
DMARC is an email authentication standard, developed to combat spoofed domain mail.
On domain alignment it requires that:
when a sender authenticates their email using SPF and/or DKIM,
at least one of the domains must align with the sending From domain
To get it within DKIM (DomainKeys Identified Mail),
the dkim signing domain (DKIM-Signature: d=…) must match the sending From domain.
DMARC allows two types of DKIM alignment: relaxed alignment and strict alignment.
If you do not specify strict alignment, relaxed alignment is assumed as the default.
relaxed alignment
With relaxed alignment, only the root of the dkim signing domain must match the sending From domain.
Relaxed alignment allows any subdomain to be used and still meet the domain alignment requirement.
example:
-
if your dkim sigining domain is mail.abc.com and your From domain is abc.com,
your email will pass DKIM alignment (the root domains “abc.com” match)
-
if your dkim sigining is abc.mail.com and your From domain is abc.com,
your email will NOT pass DKIM alignment (the root domains “mail.com” and “abc.com” do not match)
strict alignment
With strict alignment, the dkim signing domain must match exactly the domain of the sending From address.
example:
-
if your dkim sigining domain is mail.abc.com and your From domain is mail.abc.com,
your email will pass DKIM alignment (the domains “mail.abc.com” match)
-
if your dkim sigining domain is mail.abc.com and your From domain is abc.com,
your email will NOT pass DKIM alignment (the domains “mail.abc.com” and “abc.com” do not match)
<dkim> check online
<dmarc> detects fake emails

dmarc explained
DMARC stands for: Domain-based Message Authentication, Reporting and Conformance.
It is an email authentication standard, developed to combat spoofed domain mail.
Senders:
- authenticate their emails with spf and dkim
- publish a “dmarc policy” for how to handle unauthenticated mail
Receivers:
- take action on unauthenticated mail, based on the sender “dmarc policy”
- report on the outcome to the sender
With some mailbox providers, it influences deliverability in a meaningful way, see:
How dmarc works with Google Mail and Office 365 in 2020 *
“Office 365 is generally responsive to spf and dkim authentication.
The only way to get consistent results, reaching the inbox, is to associate them with dmarc”
* = external website link, will open in a new page
how to make dmarc work
DMARC uses SPF (Sender Policy Framework) and DKIM (Domain Keys Identified Emails)
to control the situation when email fails authentication tests.
SPF requires that you declare which servers you use to send out email messages.
Check how to configure spf to know more and set it correctly.
RealSender smtp servers sign all outgoing email messages with the DKIM signature.
A setup is needed if you want to sign with the same domain of the sender.
Check how to configure dkim to know more.
RealSender provides you a mailbox that collects the dmarc reports generated by the receivers.
- At the beginning you should set the policy tag to “none” (p=none),
which means that the Mailbox Provider won’t do anything with the spoofed/phished emails.
You should add a TXT record on your domain (example.com), that should look like this:
_dmarc.example.com. IN TXT "v=DMARC1; p=none; rua=mailto:dmarc.example@rsbox.com"
-
Starting from the next day, you will begin to receive the dmarc rua reports online.
You might discover that you forgot to authenticate an email campaign that’s being deployed from a third party.
If something like that happens, simply authenticate it and check that the next mailing passes the dmarc tests.
-
When the reports are correct for a few weeks, tell the Mailbox Providers to reject/block those spoofed/phished emails.
The _dmarc TXT record of your domain should be changed to look like this:
"v=DMARC1; p=reject; rua=mailto:dmarc.example@rsbox.com"
dmarc downsides
If your organization implements dmarc, you will need to check carefully
before you introduce any new method of sending email.
Dmarc applies strict policies on how spf and dkim are tested
this can cause emails which would otherwise pass those tests
to be rejected by mailbox providers.
Even if everything is set correctly, the verification may fail:
- the spf check, if the email has been redirected (forwarded) or sent through a mailing list
- the dkim check, if the message has been altered, breaking the dkim signature
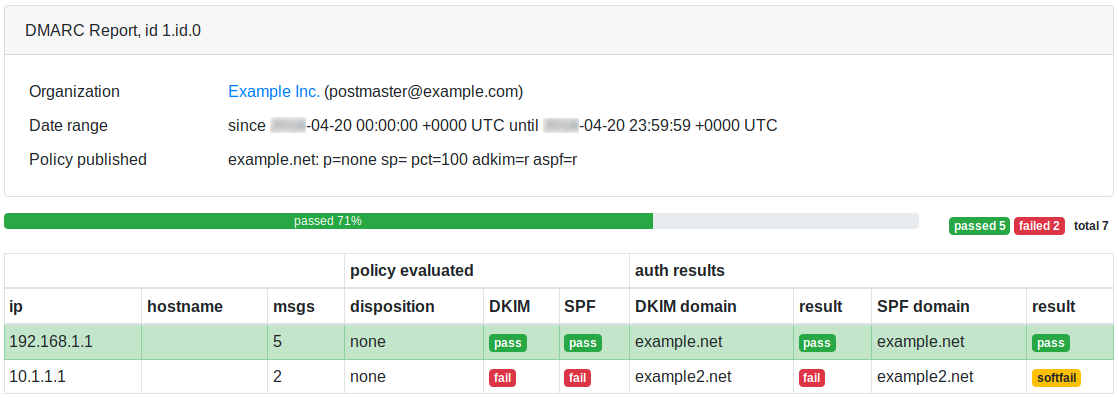
<dmarc> rua reports online
<dmarc> rua reports online

RealSender collects and analyses the dmarc rua(*) reports for you.
* = rua meaning:
Reporting URI(s) for aggregate data.
In RealSender, the “rua” is the email address provided to the customers,
to which aggregate reports are sent by domains
that have received mail claiming to be from your domain.
The reports are generated every day at 13:00 (CET) and contain the data of the last seven days.
This is a dmarc online report, sample page: