Subsections of email client settings
Outlook


Tools > Options > Accounts
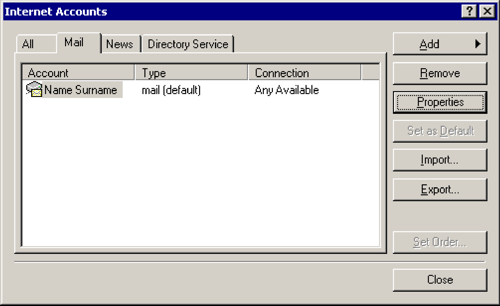
Mail > [Properties]
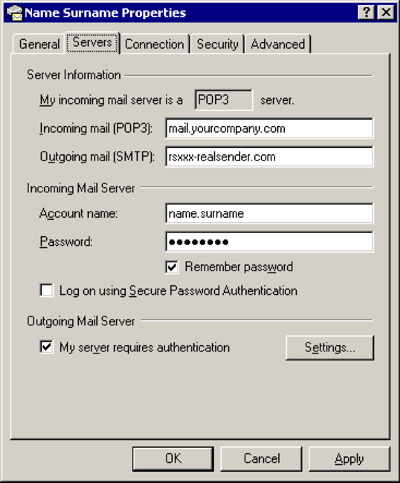
Servers
Outgoing mail (SMTP): rsxxx.realsender.com
Outgoing Mail Server
[x] My server requires authentication
[Settings…]
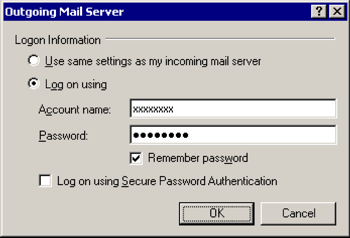
Outgoing Mail Server
[x] Log on using
Account name: (the one we sent you)
Password: (the one we sent you)
[x] Remember password
[OK]
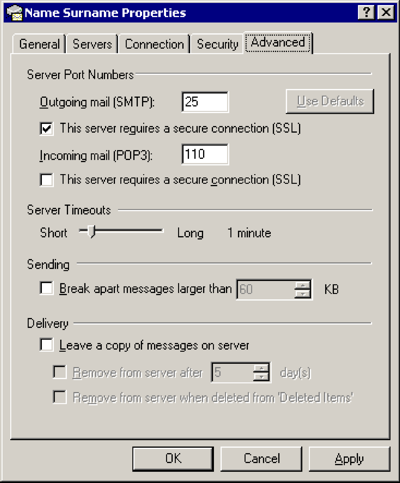
Advanced
Outgoing mail (SMTP): 25
[x] This server requires a secure connection (SSL)
[OK]
Outlook 2007

Tools > Options…
Mail Setup > [E-mail Accounts…]
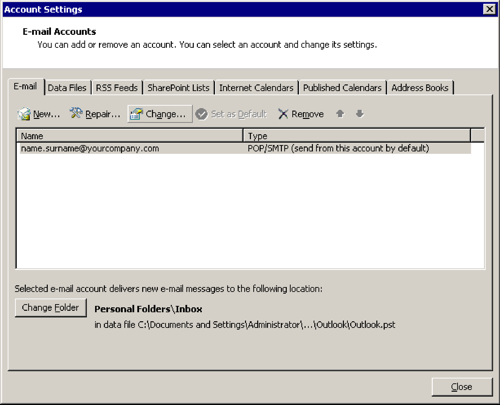
[Change…]
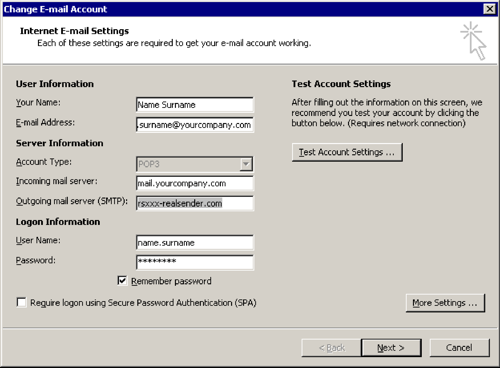
Change E-mail Account
Outgoing mail server (SMTP): rsxxx.realsender.com
[More Settings…]
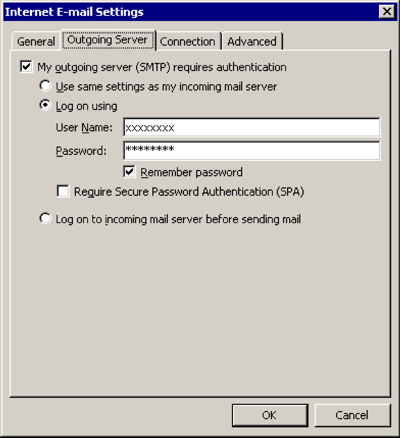
Outgoing Server
[x] My outgoing server (SMTP) requires authentication
[x] Log on using
User Name: (the one we sent you)
Password: (the one we sent you)
[x] Remember password
[OK]
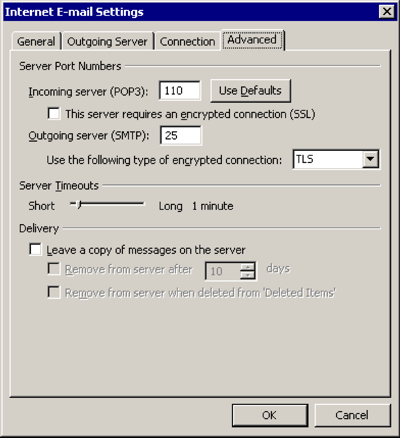
Advanced
Use the following type of encrypted connection: TLS
[OK]
Outlook 2013 2016

File > [Info]
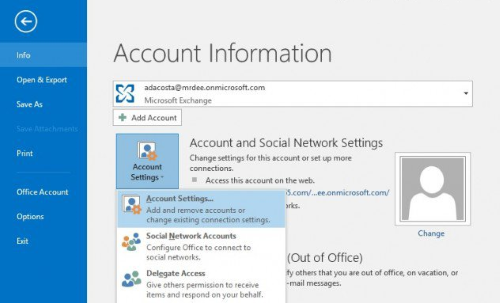
[Account and Social Network Settings]
[Account Settings…]
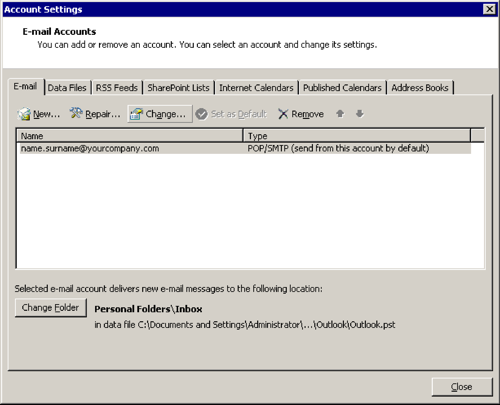
[Change…]
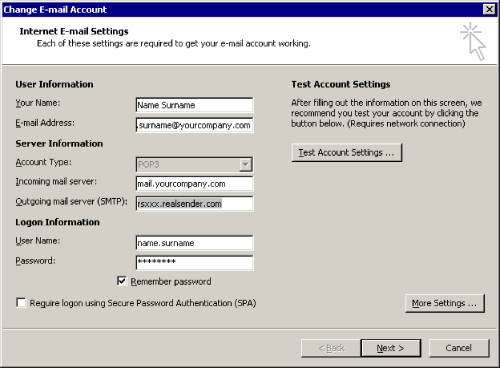
Change E-mail Account
Outgoing mail server (SMTP): rsxxx.realsender.com
[More Settings…]
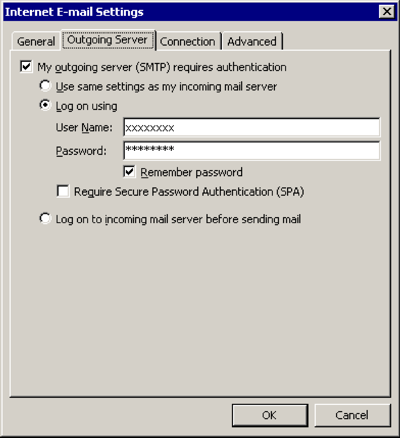
Outgoing Server
[x] My outgoing server (SMTP) requires authentication
[x] Log on using
User Name: (the one we sent you)
Password: (the one we sent you)
[x] Remember password
[OK]
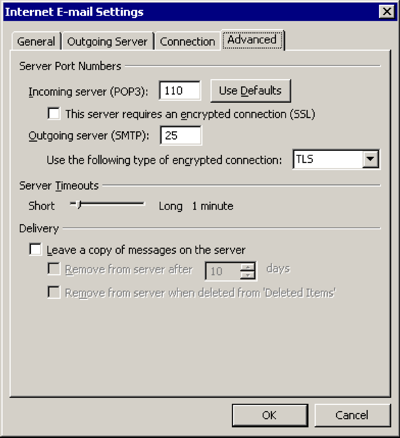
Advanced
Use the following type of encrypted connection: TLS
[OK]
Mac OS/X Mail
Mail > Preferences… > Server Settings
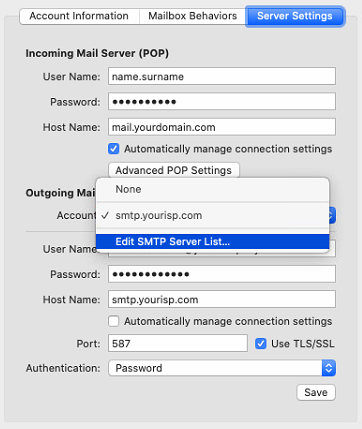
Outgoing Mail Server (SMTP) > Edit SMTP Server List …
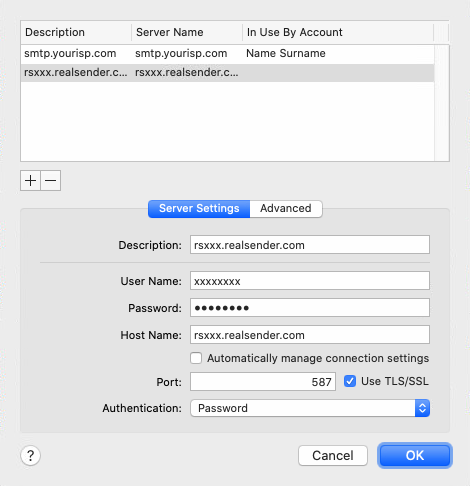
[+] Create an account
Description: rsxxx.realsender.com
User name: (the one we sent you)
Password: (the one we sent you)
Host Name: rsxxx.realsender.com
[ ] Automatically detect and maintain account settings
Port: 587 [x] Use TLS/SSL
Authentication: Password
[OK]
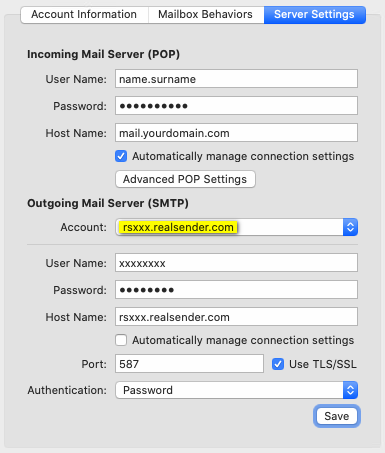
Outgoing Mail Server (SMTP)
Account: rsxxx.realsender.com
[Save]
Thunderbird

Tools > Account Settings
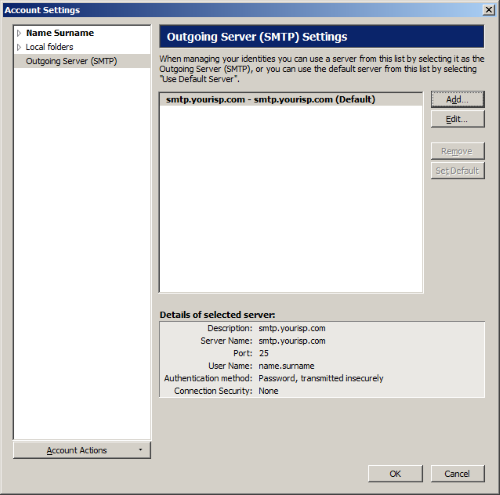
Outgoing Server (SMTP) > [Add…]
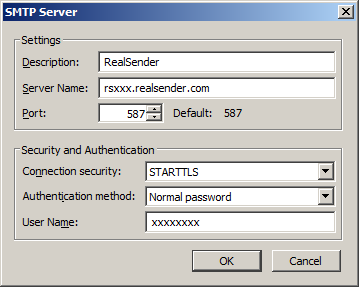
Settings
Description: RealSender
Server Name: rsxxx.realsender.com
Port: 587
Security and Authentication
Connection security: STARTTLS
Authentication method: Normal password
User Name: (the one we sent you)
[OK]
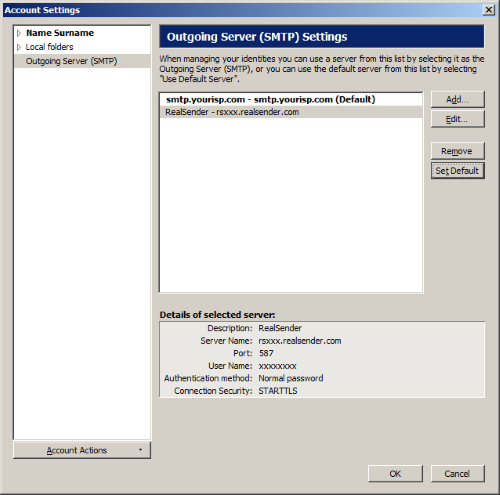
RealSender > [Set Default]
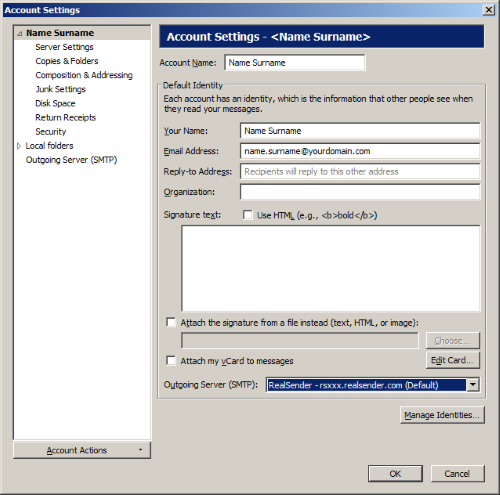
Account settings
(select you email account on the tree at the left side)
Outgoing Server (SMTP): RealSender
[OK]
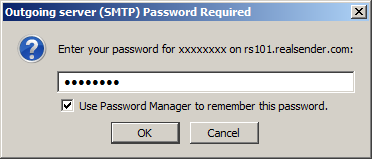
The first time you send a message
Outgoing Server (SMTP) Password Required
Enter your password for…: (the one we sent you)
[x] Use Password Manager to remember this password
[OK]
Zimbra Desktop

Launch Desktop > Setup (top right)
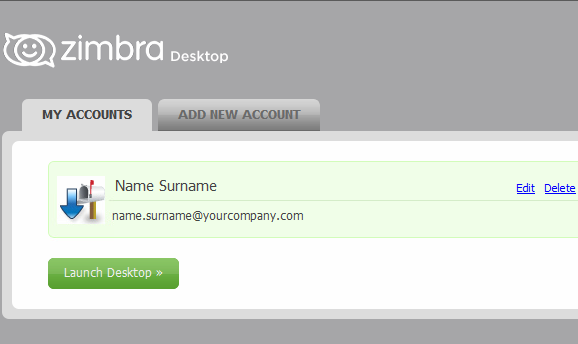
MY ACCOUNTS > [Edit]
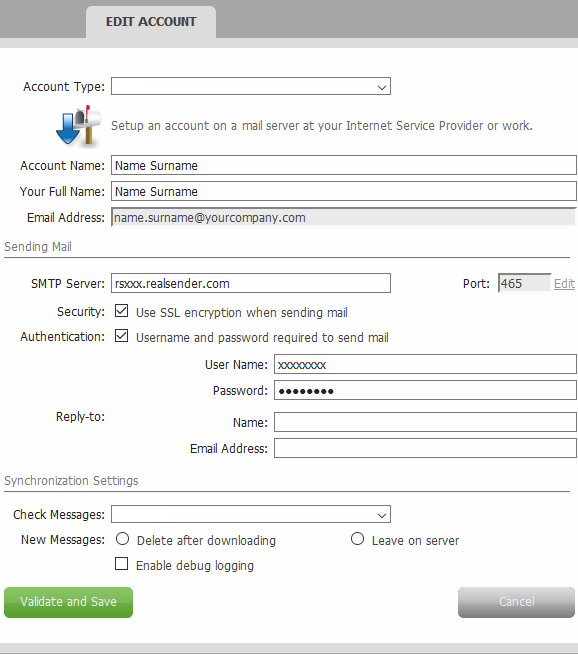
EDIT ACCOUNT
Sending Mail
SMTP Server: rsxxx.realsender.com
Security: [x] Use SSL encryption when sending mail
Authentication: [x] Username and password required to send mail
User Name: (the one we sent you)
Password: (the one we sent you)
[Validate and Save]
Subsections of email server settings
Exchange Server

EAC
(Exchange Admin Center)
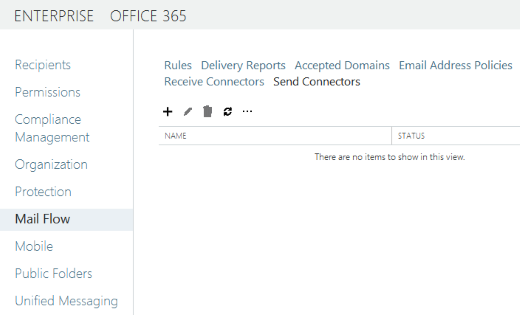
Mail Flow > Send Connectors
[+] New send connector
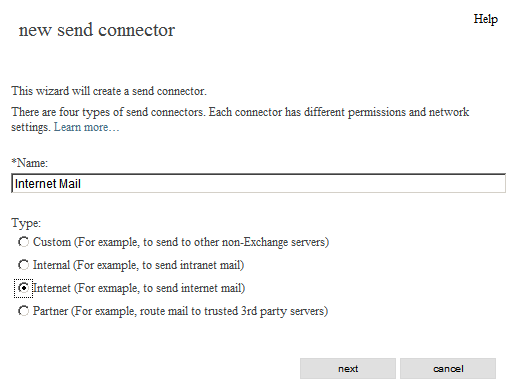
new send connector
*Name:
Internet Mail
Type:
[x] Internet (For example, to send internet mail)
[next]
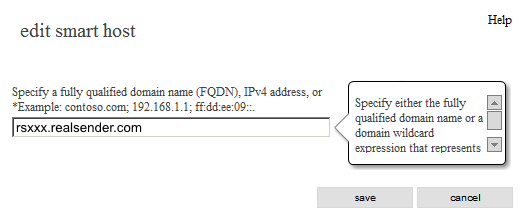
edit smart host
Specify a fully qualified domain name (FQDN), IPv4 address, or IPv6 address:
rsxxx.realsender.com
[save]
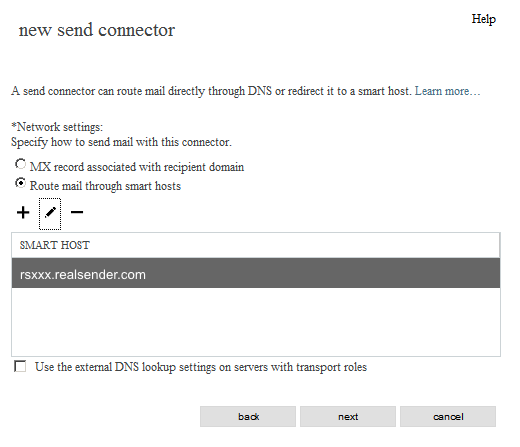
new send connector
*Network settings:
[x] Route mail through smart hosts
(unchanged)
[next]
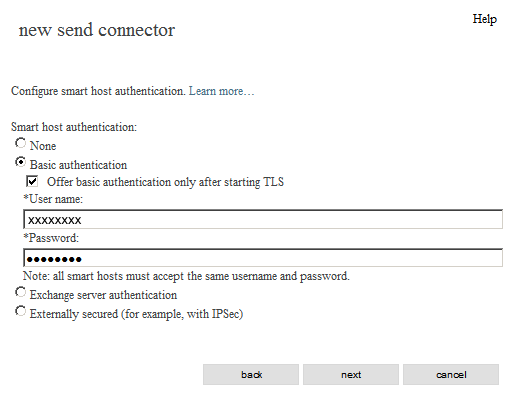
new send connector - authentication
Smart host authentication:
[x] Basic authentication
[x] Offer basic authentication only after starting TLS
*User name:
(the one we sent you)
*Password:
(the one we sent you)
[next]
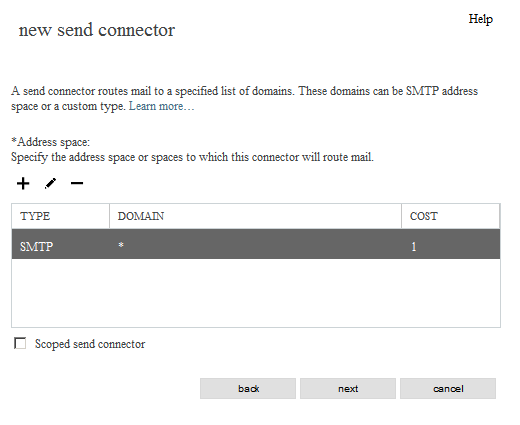
new send connector - routing
*Address space:
TYPE: SMTP
DOMAIN: *
COST: 1
[next]
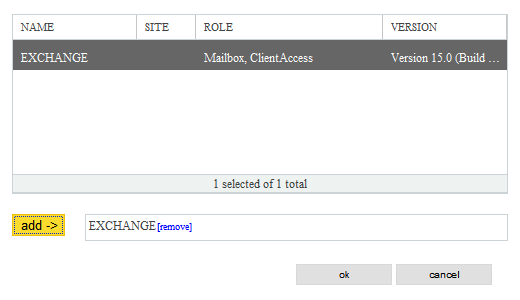
new send connector - which exchange server
[EXCHANGE]
[add ->] EXCHANGE
[ok]
[finish]
Office 365

Microsoft Office 365 Admin center
Left-menu > Admin
Microsoft 365 admin center > … Show all
Microsoft 365 admin center > Admin centers > Exchange
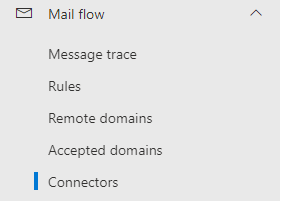
Exchange admin center > Mail flow > Connectors
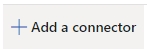
Connectors > Add a connector
New connector
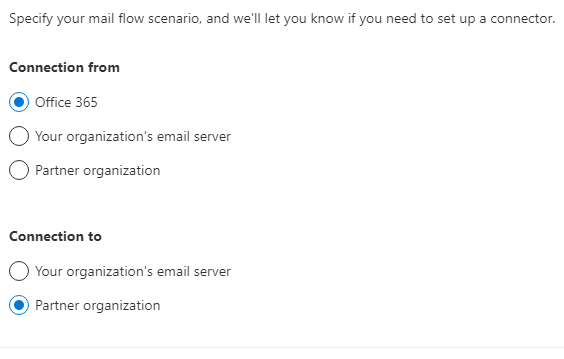
Connection from: [x] Office 365
Connection to: [x] Partner organization
[Next]
Connector name
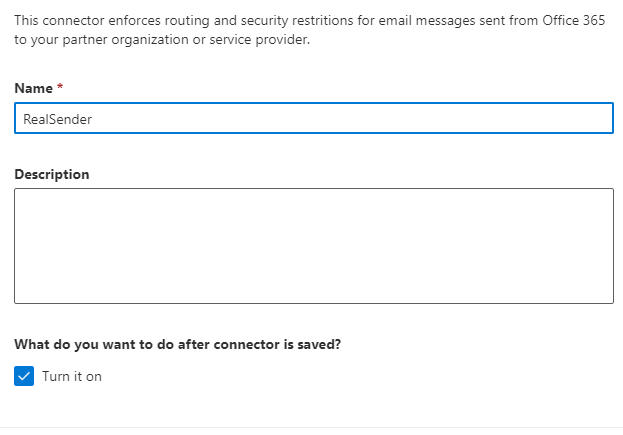
This connector enforces routing and security restritions for email messages sent
from Office 365 to your partner organization or service provider.
Name: RealSender
What do you want to do after connector is saved?
[x] Turn it on
[Next]
Use of connector
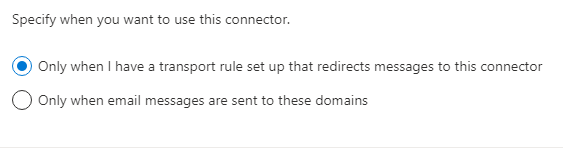
Specify when you want to use this connector.
[x] Only when I have a transport rule set up that redirects messages to this connector
[Next]
Routing
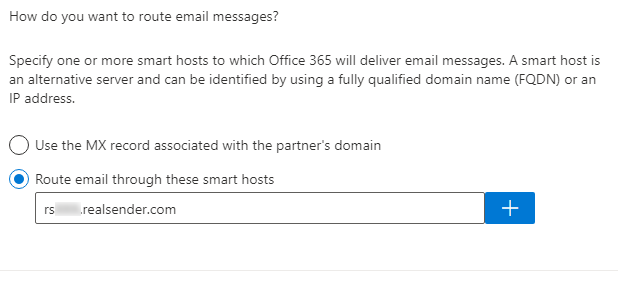
How do you want to route email messages?
Specify one or more smart hosts to which Office 365 will deliver email messages.
A smart host is an alternative server and can be identified by using a fully qualified domain name (FQDN) or an IP address.
[x] Route email through these smart host
rsxxx.realsender.com [+]
[Next]
Security restrictions
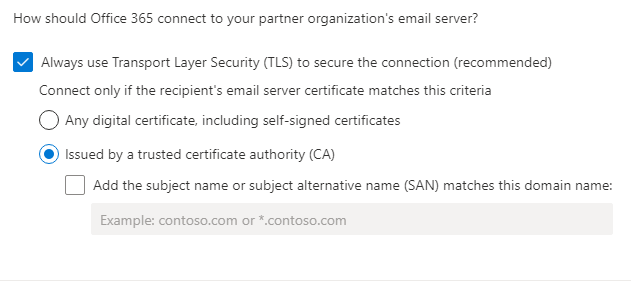
How should Office 365 connect to your partner organization's email server?
[x] Always use Transport Layer Security (TLS) to secure the connection (recommended)
Connect only if the recipient's email server certificate matches this criteria
[x] Issued by a trusted certificate authority (CA)
[Next]
Validation email
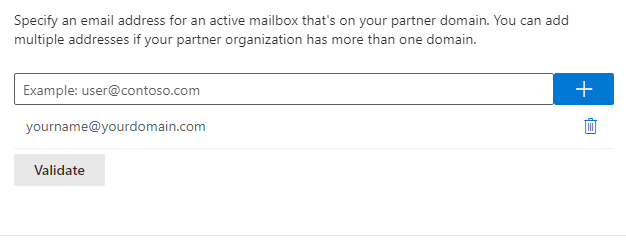
Specify an email address for an active mailbox that's on your partner domain.
You can add multiple addresses if your partner organization has more than one domain.
yourname@yourdomain.com [+]
[Validate]
Validation successful
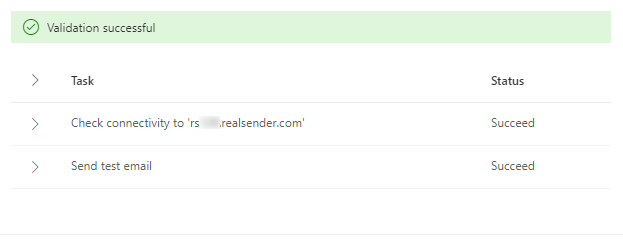
[Validate]
Validation in progress...
Validation successful
> Task Status
> Check connectivity to 'rsxxx.realsender.com' Succeeded
> Send test email Succeeded
[Next]
Review connector
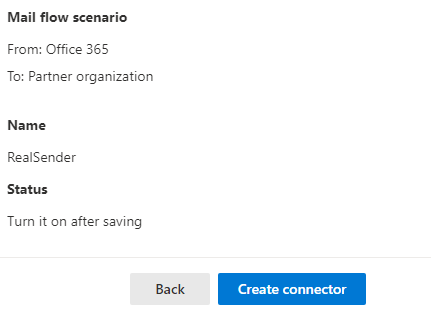
Mail flow scenario
From: Office 365
To: Partner organization
Name
RealSender
Status
Turn it on after saving
Use of connector
Use only when I have a transport rule set up that redirects messages to this connector.
Routing
Route email messages through these smart hosts: rsxxx.realsender.com
Security restrictions
Always use Transport Layer Security (TLS) and connect only if the recipient’s
email server certificate is issued by a trusted certificate authority (CA).
[Create connector]
Zimbra Collaboration

Zimbra Collaboration
(network edition / open source)
> Admin Console
Zimbra Administration
> Configure
> Global Settings
> MTA
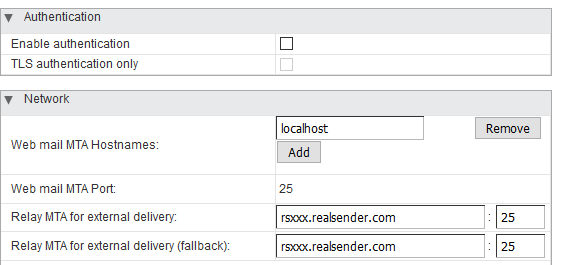
Authentication
Enable authentication [ ]
TLS authenticaton only [ ]
Network
Web mail MTA Hostnames: localhost
Web mail MTA Port: 25
Relay MTA for external delivery: rsxxx.realsender.com : 25
Relay MTA for external delivery (fallback): rsxxx.realsender.com : 25
Please [inform our support team](/we-deliver-your-emails/contacts) that you're using Zimbra Collaboration,
so that we configure our servers to accept the connection
without any further setup on your side
(no need to make any change to the Zimbra's postfix smtp settings)
inxbox app

RealSender’s “inxbox” app is a ready-to-use email server,
that receives any message sent to the authorized domain.
It immediately becomes operational as soon as the mx record points to it.
It is often used as an emergency mail server.
If your regular email service goes down,
inxbox will immediately accept any message sent to it.
Without any special configuration required,
such as specifying individual user email addresses.
When configured as historical archive of emails,
an automatic process records messages
by recipient, month, and year.
Main features:
transparently records all the emails
a secure web area to read online inxbox email messages
Subsections of inxbox app
historical archive of emails

Email messages are the main channel of modern business communications.
Their accidental loss would great damage the company’s knowledge base.
Furthermore, business correspondence should generally be kept for up to ten years.
!! if your company is using personal mailboxes
such as name.surname@companyname.com
you must have informed the senders before activating this function
We provide you with a dedicated inbound email domain,
so RealSender’s “inxbox” app archives transparently
all the emails, that you can access via:
An automatic process archives the messages divided by recipient, month and year.
When associated with RealSender Secure Email Gateway,
all the sent emails are duplicated and archived automatically.
Request a free trial
webmail interface
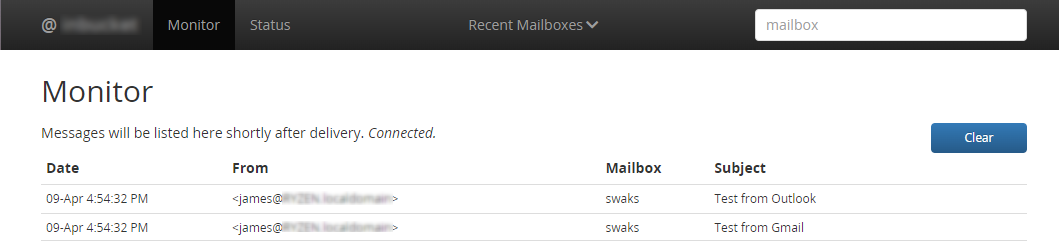
Web-interface features:
- List messages in a mailbox
- Displays content of a particular message
- Displays source of a message (headers + body)
- Displays HTML version of a message (in a new window)
- List MIME attachments with buttons to display or download
- Delete a message
- Monitor: a real time display of all received messages
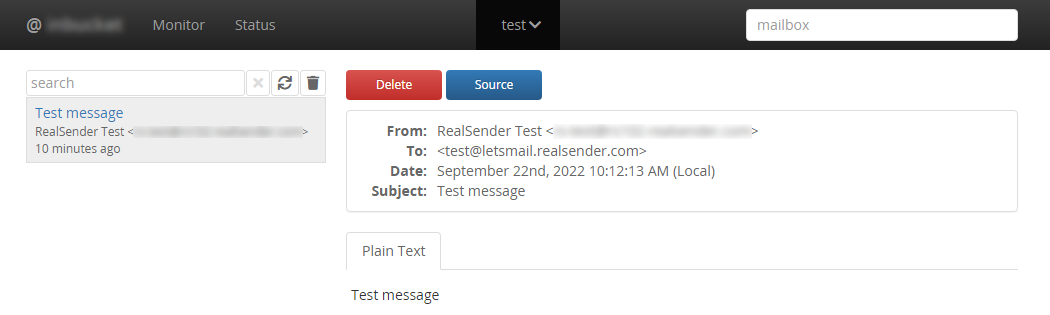
A working demo is available in our (free) postmaster tools area:
» inxbox demo temporary email
Request a free trial
spamstop app

Email is the main channel for cyber attacks.
Sender address spoofing can be detected by email authentication information.
RealSender’s “spamstop” app shows the results of authenticity checks
directly in the subject of received messages.
It is an efficient anti-spam solution when combined with a filter
that splits messages according to senders that are NOT in your address book.
It can be activated for the entire domain or even just a few email addresses.
Main features:
spf-based email sender check
dkim-based sender and email seal check
at least one of the domains must align with the sending From domain
two SPAM tags added to the subject to highlight fraud
to receive in your inbox only the senders you have previously authorized
to receive email messages only from the senders that you have previously authorized
to protect your email boxes from unwanted senders and dangerous attachments
Subsections of spamstop app
1 - spf check

We want to make sure that the sender address has not been forged/spoofed*.
* = make the message appear from someone other than the actual source
SPF authentication helps us identifying if the message has been sent through an authorized smtp server.
This information is stored in the domain’s dns, that is a safe place, outside the email message.
Only if the message has NOT been authenticated correctly:
the !! (attention) symbol is added to the subject,
one of the following explanatory notes is inserted in the message header, line “X-RealSender”:
:: spf-none :: the sender domain contains no information to authenticate the email
:: spf-softfail :: the smtp server is not listed among the authorized ones but this case should be treated as a "softfail"
:: spf-fail :: the smtp server is not listed among the authorized ones and the email should be rejected or discarded
Sometimes the information recorded at domain level is not correct/understandable.
:: spf-permerror :: a permanent error has occured (eg. badly formatted SPF record)
SPF check is made against the “Mail From” email address, that is hidden in the email headers.
Only the “From” email address is visible. If their root domains are different, this warning is displayed:
:: spf-diff :: the "Mail From" and the "From" root domains are different
Tell me more
2 - dkim check

DKIM (DomainKeys Identified Mail) allows senders to prove that the email was actually sent by them and has not been modified after being sent.
It achieves this by affixing a digital signature (seal), linked to a domain name, to each outgoing email message.
Only if the message has NOT been signed correctly:
the !! (attention) symbol is added to the subject,
one of the following explanatory notes is inserted in the message header, line “X-RealSender”:
:: dkim-none :: no DKIM-Signature headers (valid or invalid) were found
:: dkim-fail :: a valid DKIM-Signature header was found, but the signature does not contain a correct value for the message
Sometimes it’s not possible to execute the check:
:: dkim-invalid :: there is a problem in the signature itself or the public key record. I.e. the signature could not be processed
:: dkim-temperror :: some error was found which is likely transient in nature, such as a temporary inability to retrieve a public key
When the message has been signed using a different domain, a “diff” notice is added:
This warning will NOT appear if the sender passes the SPF check:
:: dkim-diff :: the message has NOT been signed by the sender's domain
Tell me more
3 - dmarc alignment

DMARC (Domain-based Message Authentication, Reporting and Conformance),
is an email authentication standard, developed to combat spoofed domain mail.
In the chapter “3.1. Identifier Alignment” it says:
Email authentication technologies authenticate various (and
disparate) aspects of an individual message. For example, [DKIM]
authenticates the domain that affixed a signature to the message,
while [SPF] can authenticate either the domain that appears in the
RFC5321.MailFrom (MAIL FROM) portion of [SMTP] or the RFC5321.EHLO/
HELO domain, or both. These may be different domains, and they are
typically not visible to the end user.
DMARC authenticates use of the RFC5322.From domain by requiring that
it match (be aligned with) an Authenticated Identifier.
-- https://tools.ietf.org/html/rfc7489#section-3.1
It simply means:
when a sender authenticates their email using SPF and/or DKIM,
at least one of the domains must align with the sending From domain
This approach is widely accepted and generally considered
a good practice to identify trusted sender domains.
**RealSender MX Protect checks the dmarc-default "relaxed" alignment:**
-
For SPF authentication
the root domain of the Mail From address must match the root domain of the From address.
Relaxed alignment allows any subdomain to be used and still meet the domain alignment requirement.
-
For DKIM authentication
the root of the dkim signing domain must match the From domain.
Relaxed alignment allows any subdomain to be used and still meet the domain alignment requirement.
**Possible results:**
-
both the rules are respected
the sender domain is fully trusted,
the message arrives unchanged
-
only one of the two rules is met
the ~ (tilde) symbol is added to the subject,
one of the following explanatory notes is inserted in the message header
~ ... subject ...
X-RealSender: ~ | spf=pass (domain NOT aligned) | dkim=pass | ~
~ ... subject ...
X-RealSender: ~ | spf=pass | dkim=pass (domain NOT aligned) | ~
- no alignment at all
the “:: spf-diff ::” and “:: dkim-diff ::” warnings
are displayed in the subject
Tell me more

DMARC is being used by more and more companies to protect their senders from spoofing.
Its use requires proper authentication with SPF or DKIM and alignment of From / Mail-From domains.
For more information:
<dmarc> act on fraudulent email
Messages from senders with the _dmarc record,
if they are NOT authenticated, they are highlighted with two [ SPAM ] tags in the subject:
[ SPAM ] ... message subject ... [ SPAM ]
Messages without the _dmarc record, when both SPF and DKIM authentication fail,
are reported with a [suspicious] tag in the subject:
[suspicious] ... message subject ...
Request a free trial
client side sender filter

RealSender’s “spamstop” app is an efficient anti-spam solution
when combined with a filter that splits messages
according to senders that are NOT in your address book.
Most modern email clients offer this feature.
Here are some configuration examples:
in outlook settings enable: trust email from my contacts
in Thunderbird create a filter with rules 'From isn't in my address book'
Subsections of client side sender filter
Microsoft 365 Outlook

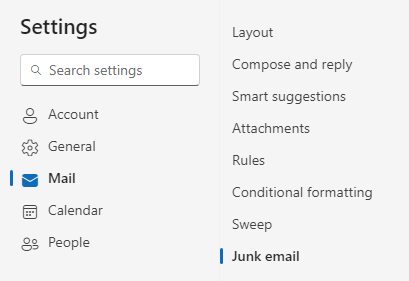
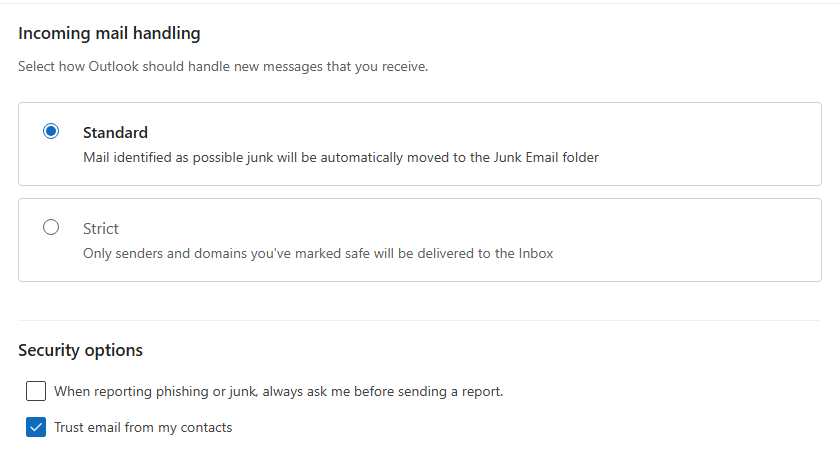
Below is the “Settings” screen in Outlook.
In “Junk email”, check “Trust email from my contacts”.
Press [Save] to record the changes.
Request a free trial
Mozilla Thunderbird

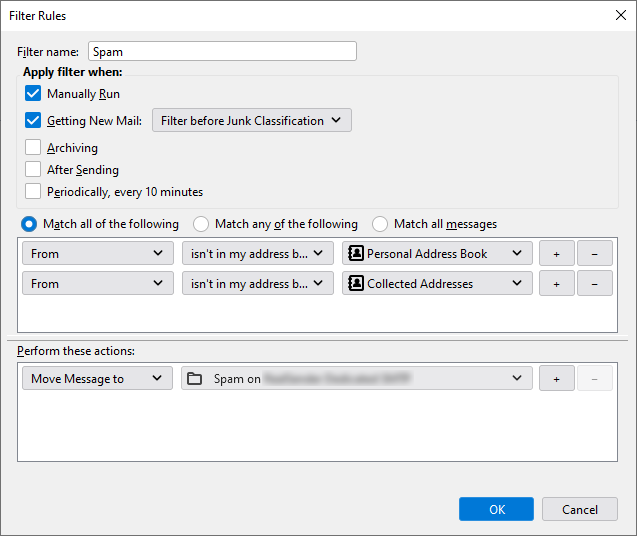
Below is a screenshot of the “Message filter” tool in Thunderbird.
Add conditions with the “Match ALL of the following” option:
- From isn’t in my address book, Personal Address Book
- From isn’t in my address book, Collected Addresses
Perform these actions:
Move Message to: Spam.
Request a free trial
server side sender filter

Not all email clients provide sophisticated ways to filter emails.
In these cases it is possible to act upstream.
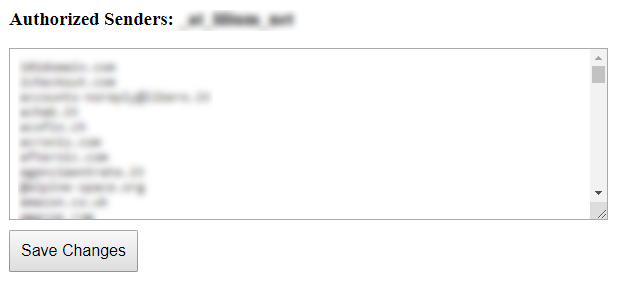
The “Authorized senders” feature allows you to receive messages
only from the senders you have previously authorized
(you can also specify the entire domain, e.g. @example.com):
All the regular messages will arrive as usual in your inbox.
All the spam messages will go to a different mailbox
or in the user’s “Junk” email folder of Microsoft 365 Exchange.
No emails will be lost.
You may read the discarded messages mailbox once or more a day.
You will save so much precious time.
Request a free trial
Subsections of server side sender filter
Microsoft 365 Exchange

This configuration allows to correctly move mail
from UNauthorized senders to the user’s Junk email folder
The messages filtered by SpamStop app will arrive
with the following anti-spam headers and values:
X-Forefront-Antispam-Report: SFV:SKB
(message marked as spam by spam filtering
due to the sender’s email address or email domain
NOT present in the list of authorized senders)
The following Action must be activated:
Set the spam confidence level (SCL) of these messages to 6 (spam)
The default value of the SCLJunkThreshold parameter is 4, which means
an SCL of 5 or higher should deliver the message to the user’s Junk email folder.
-
In the In the Exchange admin center (EAC), go to Mail flow > Rules.
-
On the Rules page, select Add > Create a new rule in the dropdown list.
-
In the New rule page that opens, configure the following settings:
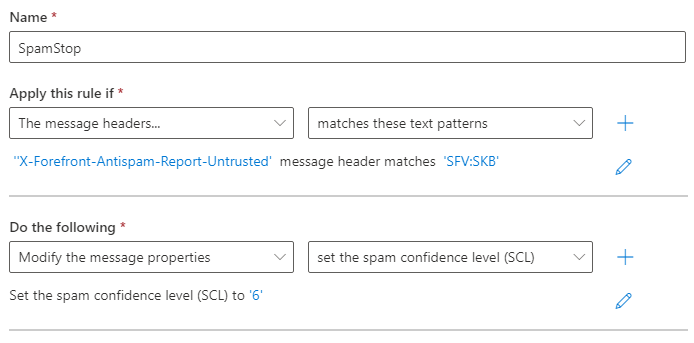
Name: SpamStop
Apply this rule if: ‘X-Forefront-Antispam-Report-Untrusted’
message header matches: ‘SFV:SKB’
Do the following:
Modify the message properties
Set the spam confidence level “SCL” to: ‘6’
Save and Enable the rule.
Request a free trial
security settings

They add an extra layer of security to your emails.
To protect your email inboxes
from fake senders and dangerous attachments.
Security options that are activated on request:
to receive emails only from senders who have passed authentication checks
to remove all potentially harmful attachments from emails
Subsections of security settings
authenticated senders only

This is useful when you only want to receive messages from verified senders.
All emails that do not pass the checks are deleted or bounced.
You need to make sure that the sender’s email address has not been spoofed.
This control can be done putting together SPF and DKIM authentication.
SPF confirms the sender’s address and its relationship with the server that sent out the message.
DKIM ensures that email messages (including attachments) are not modified
after they have been “signed” during sending.
In theory it’s that easy, in practice both SPF and DKIM can refer
to a different domain than the sender’s email address.
We check that SPF authentication and DKIM signature are related to the domain in the from address.
In this way no other than the original sender can authenticate the email. This guarantees its origin.
Request a free trial
remove dangerous attachments

The “remove dangerous attachments” option blocks all potentially harmful attachments
except some safe extensions as pdf, txt, gif, jpg and png.
The recipient receives the message without the attachment.
A warning is added to the beginning of the content, like this:
WARNING: This email violated Your Company's email security policy and
has been modified. For more information, contact your IT Administrator.
An attachment named "example.zip" was removed from this document as it
constituted a security hazard. If you require this document, please contact
the sender and arrange an alternate means of receiving it.
There is an interesting case study published on the Internet, which ends with this sentence:
“For us, attachment filtering has been very successful”
– web.mit.edu/net-security/Camp/2004/presentations/reillyb-mit2004.ppt (PowerPoint presentation)
Request a free trial
















































































