protect emails from SPAM
How to protect business emails from spam ?
It is almost impossible to think about email without considering the issue of spam.
We tried to summarize the current situation and the strategies that can be followed:
- How much email traffic is spam?
- What are the costs of spam?
- What are the latest anti-spam techniques?
How much email traffic is spam?
A reputable source is SenderBase, now called Talos,
showing about 85% spam email and 15% legitimate email
compared to the email traffic recorded in September 2020.
This percentage has been stable, with little changes in the last twelve months.
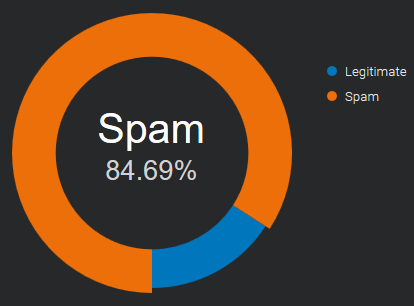
Source: Email & Spam Data - Total global email & spam volume.
What are the costs of spam?
Sometimes spam is just for promotional purposes, and the sender
is merely trying to generate more customers for his business,
causing distractions and loss of time. It can fill your inbox
so that it’s difficult to find emails that are important.
Not all spam are friendly promotional emails.
There are many cases where the intentions are malicious, aiming to damage or hijack user systems.
The most common variants of malicious spam worldwide include trojans, spyware, and ransomware.
What are the latest anti-spam techniques?
Imagine your company’s inboxes as your house door:
you have to decide who can come in and who you leave out.
No technique is a complete solution to the spam problem.
Each has trade-offs between incorrectly rejecting legitimate email (false positives)
as opposed to not rejecting of spam (false negatives)
and the associated costs in time, effort, and cost of wrongfully blocking good mail.
Anti-spam techniques can be broken into two areas: prevention and cure.
Spam prevention (before it happens)
Restrict the availability of your email addresses, with the goal of reducing the chance of receiving spam.
-
Discretion
don’t give your email address to everybody
the less known it is, the less spam you will receive
whenever it is possible, use a different email for online registrations -
Contact forms
don’t publish your email address online
anybody can see it, “spambots” catch them all the time
to get contacted online, use secure* web forms / contact forms
* = protected by robots that fill them automatically
Spam cure (while it’s happening)
Once the spammers have your email address, the fight moves to your mail server and inbox.
-
SpamAssassin-like score systems
They use several spam-detection techniques including DNS based email blacklists
(commonly called Realtime blacklist, DNSBL or RBL), text analysis and Bayesian filtering.
Each test has a score value. The scores can be positive or negative, with positive values indicating “spam” and negative “ham” (non-spam).
The default score threshold for the recipient is “5.0”. If an email score lands higher than the threshold, is marked as spam.
There are a lot of “SpamAssassin Tests” available on the net,
that let the spammers check their messages before sending them. -
Powered by users
Users of these systems can flag incoming emails as legitimate or spam and these notations are recorded into a central database.
After a certain number of users mark a particular email as junk, the filter automatically blocks it from reaching the rest of the community’s inboxes.
Sometimes users feedback is integrated with automated controls like the number of interactions with message contents,
as the amount of click on links and the images downloaded, or the count of the occurrences of the same message in multiple mailboxes.
When a collaborative content filtering system involves a large, active user base,
it can quickly block a spam outbreak, sometimes within a matter of minutes.
This kind of filter can hardly be overcome by spammers. -
Email Authentication
SPF, DKIM and DMARC are authentication techniques that let you recognize if the from address is really who it claims to be.
In 2020 they’re widely used and they are a good source to identify the trusted senders.
It is important to know in advance the exact domain the emails are coming from,
otherwise it is easy to be misled by the simple change of a letter.
It’s possible for spammers to comply with email authentication
so that their messages look to come from “legitimate senders”. -
Authorized senders, whitelist
In a whitelist one can specify a series of trusted addresses or domains.
In the beginning the personal address book and the past received emails will be of great help.
If a sender is in this list, all controls are skipped and the message is received without delays.
This method is easy to implement and very effective when associated with Email Authentication, to avoid email address spoofing*.
* = use of a fake sender to make the message appear from someone other than the actual source
Once your list of trusted contacts is filled, no unknown sender will reach your mailbox.
All unwanted messages can be redirected to a different mailbox to be checked once a day or more rarely.
Spammers will hardly find which are the trusted senders of each recipient.
Even when they do it, email authentication checks will alert you of the fraudulent use.