let's empower your emails
you get email control
 |
 |
 |
 |
 |
 |
Emails |
Ignored |
Read |
|---|---|---|
 |
 |
 |
send emails without the hassle of authentication
digitally signed email messages: spf, dkim and secure email authentication
IP addresses are important for sending email messages
safely switch from your current mailserver to RealSender

Send emails without the hassle of user authentication.
We provide you with an open port to pass through,
checking only the IP addresses of your connection.
Just declare which IP addresses you are connecting from
and you are ready to send your emails.
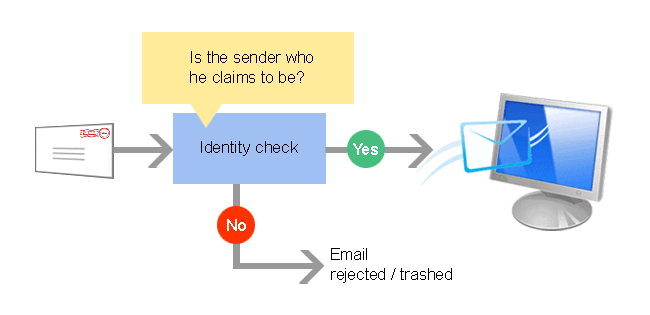
To defend from email abuse, more and more email servers
check the sender’s identity before delivering the message.
Sending emails without RealSender, your recipients can’t be sure
that the message received was generated by you.
Sending emails using RealSender, all the messages you send
are digitally signed, so that the recipients can trust them.
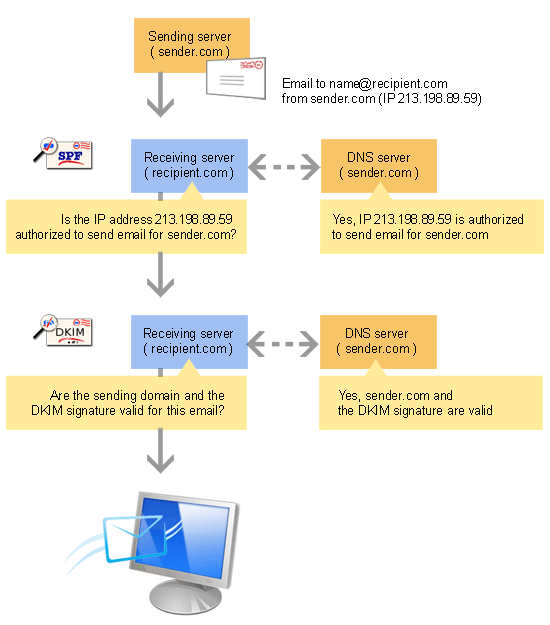
There are two standards to check the sender’s identity: SPF and DKIM.
RealSender offers both of them:

The “Internet Protocol address” or “IP address”
is similar to a telephone number on your home phone or mobile device.
It is personally identifiable information that is automatically captured
by another computer when any communications link is made over the Internet.
No other device on the Internet will have the same IP address.
This is necessary for a device to communicate with another.
“Dedicated” IP addresses are important for sending email messages
because their reputation has a strong impact on being accepted or not.
Using “shared” IP addresses for business communications
is like sending each time a different sales representative to the same customer.
Not knowing him, the recipient will treat him with suspicion.
In extreme cases, if the same seller offers different products every day,
it is very likely that he will no longer be accepted the next time he knocks on the door.
Most SMTP services on the internet provide “shared” IP addresses to their customers.
Each time you send an email, a different IP address is assigned.
Something similar happens with cloud hosting providers, who offer services on a “per minute” basis.
In this case, they give one or more “temporarily assigned” IP addresses.
Since its inception in 2009, RealSender has decided to offer only SMTP servers with “dedicated” IPs.
This means that each customer receives an IP address that will not change over time.
Linking it to the corporate domain name via email authentication, will make both of them more authoritative.
If your communications are consistent and expected,
little by little they will be recognized by the recipients, who will award them a higher reputation.
This trust can reach high levels, so that all-transmitted communications
they will be automatically accepted and considered Important or High Priority.

Switch from your current mailserver to RealSender safe environment.
You may use the same authentication credentials
as well as the smtp hostname, when it is under your domain name.
You can send email messages securely, even without authentication.
Topics in this area:
only the declared senders are allowed to pass through
unauthorized accesses are identified, blocked and banned after three failed attempts
optional extra security configurations

A dedicated RealSender smtp server is assigned to each customer.
This is the only way to keep control of the server’s reputation
and daily verify the senders’ domain reputation.
This approach requires that only the declared senders are given the green light to pass.
The system checks every message and accepts/rejects them based on the list of allowed senders.
The “authorized senders” for each RealSender account
must refer to one or more domain names registered by the same company.
RealSender partners and large organizations can independently update
the list of authorized senders.

RealSender relies on the Fail2ban server application to secure your dedicated smtp.
This protects against unauthorized access and DOS (Denial Of Service) attacks.
After three failed attempts, the source IP is blocked and banned.
The causes of the blacklisting could be:
authentication attempt with wrong credentials
(incorrect username or incorrect password)
authentication attempt on insecure channels
(the system requires TLS/SSL authentication)
sender’s email address is not authorized to send
(see restrictions on RealSender authorized senders)
smtp connection interrupted during the authentication process
(multiple broken connections make the smtp service unavailable for legitimate users)
The result of the block is that the smtp server no longer responds to connection attempts,
the computer making the request will receive this message:
connect to address 93.184.216.34: Connection refusedHow to deal with accidentally banned IP addresses:
2024-08-26 01:38:01,199 fail2ban.filter [19671]: INFO [smtp] Found 93.184.216.34 - 2024-08-26 01:38:00
2024-08-26 01:38:01,201 fail2ban.filter [19671]: INFO [smtp] Found 93.184.216.34 - 2024-08-26 01:38:01
2024-08-26 01:38:01,404 fail2ban.filter [19671]: INFO [smtp] Found 93.184.216.34 - 2024-08-26 01:38:01
2024-08-26 01:38:01,972 fail2ban.actions [19671]: NOTICE [smtp] Ban 93.184.216.342024-08-23 07:00:12,501 fail2ban.filter [30057]: INFO [smtp] Ignore 93.184.216.34 by ip
2024-08-23 07:00:12,501 fail2ban.filter [30057]: INFO [smtp] Ignore 93.184.216.34 by ip
2024-08-23 07:00:13,115 fail2ban.filter [30057]: INFO [smtp] Ignore 93.184.216.34 by ip
Topics in this area:
security option to block all emails containing potentially harmful attachments
security option to limit the number of messages sent by sender
security option to block all emails that exceed the weight limit
security option to convert large file attachments into links
transparently bcc copy all the sent emails

The “stop bad attachments” option blocks all potentially harmful attachments
except some safe extensions that you can define, like: pdf, txt, gif, jpg and png.
The sending with an unauthorized attachments is stopped.
The message does not pass through the smtp server,
the email gets bounced back to the sender with this warning:
The attachment named "example.zip"
violates Your Company's email security policy.
The delivery been been blocked.
For more information, contact your IT Administrator.
Inspired by a comment from Phil Pennock on the SAGE mailing list:
I really wish that I'd be allowed to put a per-customer throttle on mails-per-day,
raisable if a customer has legitimate reasons to be sending mail ...High email volumes are often generated by a compromised account.
They can damage your company’s reputation and the one of your mailserver.
The “limit message number” option lets you define a maximum number of daily emails per sender,
so that any excess quantities will be blocked before going on the internet.
The sending of “extra quantity” communications are stopped.
The emails get bounced back immediately to the sender, with a warning like:
An error occurred when sending email. The mail server answered:
450 4.7.1 <>... sender@example.com has exceeded n messages per 1 day.As an antispam measure, most smtp servers introduced an option to limit the number of recipients
that can be specified for a given envelope. In Sendmail it is Called “MaxRecipientsPerMessage”.
RealSender promotes the limit on the number of recipients per message,
to reduce abuses and to avoid the risk of sending cc/bcc to many addresses.
We share a list of 300 @bogusemail.net addresses for testing:
bogusemail-test.txt
The messages will reach a “black-hole” mailserver.
You can use them at your convenience,
to check how many recipients per message
your smtp server allows the sending to.

If you send a large attachment to someone,
it may not go through as their incoming attachment size may be smaller.
The “limit message weight” option lets you define a maximum message weight
so that they will be blocked even before uploading them.
The sending of overweight attachments is stopped,
the email gets bounced back immediately to the sender,
with a warning like:
The message you are trying to send exceeds
the global size limit of (xxxx bytes) of the server,
reduce the size of the message and attempt to send again.
RealSender “filelink” app automatically converts
all attachments larger than the size that you define
into a link, like this:
[large file example.pdf] (43.96 MB) moved to:
http://rsXXX-realsender.com/files/e1eb3665a1a0766ea65616b6210cfd538c4950f8.pdf
The file will be DELETED after twelve months.Your recipient receives a light message.
He can download the attachment when he needs it.
The domain in the link can be any dedicated domain or subdomain you wish to use.

Email messages are the main channel of modern business communications.
Their accidental loss would great damage the company’s knowledge base.
Furthermore, business correspondence should generally be kept for up to ten years.
!! if your company is using personal mailboxes
such as name.surname@companyname.com
you must have informed the senders before activating this functionUsing the bcc (blind carbon copy) function,
RealSender transparently transfers all the sent emails
to a special pop3 mailbox
configured to receive large amounts of emails in a short time
you can automatically download it via external services
!!! stored email messages are automatically deleted after 7 days !!!
for example using the “Check mail from other accounts” setting
available within Gmail, both individual (free) and G Suite App versions
to a different email address
properly configured so that the messages are not classified as spam
Gmail G Suite App gives the option to “Set up an inbound mail gateways”

Topics in this area:
email clients' configuration examples: Outlook - Outlook 2007 - Outlook 2013 2016 - Mac OS/X Mail - Thunderbird - Zimbra Desktop
email servers' configuration examples: Microsoft Exchange Server - Microsoft Office 365 - Zimbra Collaboration
a ready-to-use email server that receives any message sent to the authorized domain
a spam filter based on email authentication and authorized senders
To start using RealSender:
We automatically sign emails with DKIM, so you don’t need to do anything else.
Questions? Contact us!


Tools > Options > Accounts
Mail > [Properties]
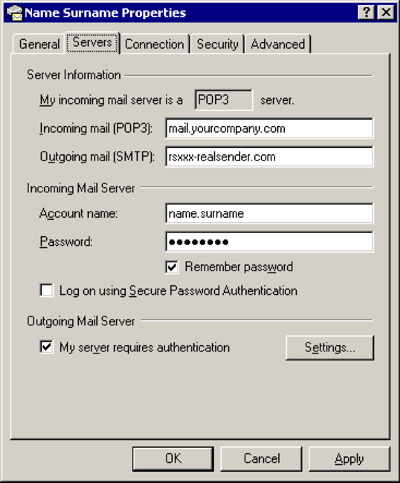
Servers
Outgoing mail (SMTP): rsxxx.realsender.com
Outgoing Mail Server
[x] My server requires authentication
[Settings…]
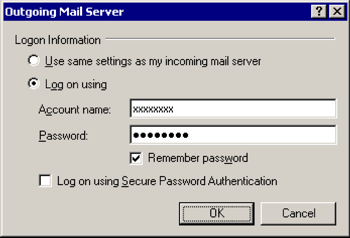
Outgoing Mail Server
[x] Log on using
Account name: (the one we sent you)
Password: (the one we sent you)[x] Remember password
[OK]
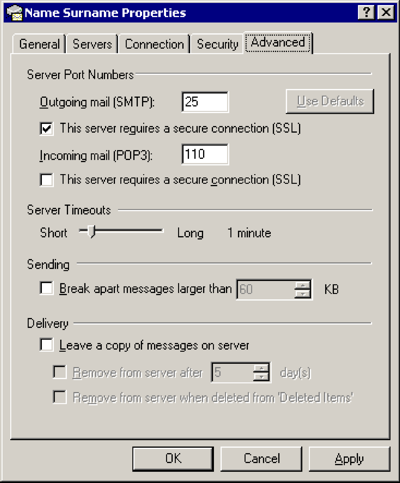
Advanced
Outgoing mail (SMTP): 25
[x] This server requires a secure connection (SSL)
[OK]

Tools > Options…
Mail Setup > [E-mail Accounts…]
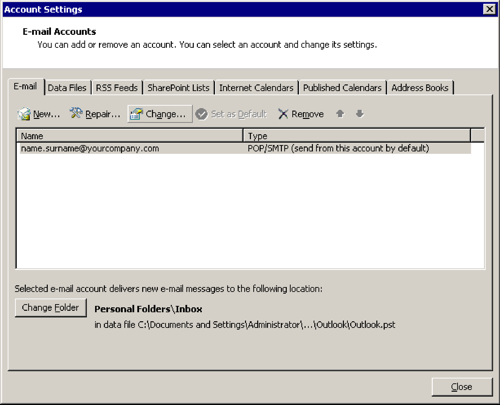
[Change…]
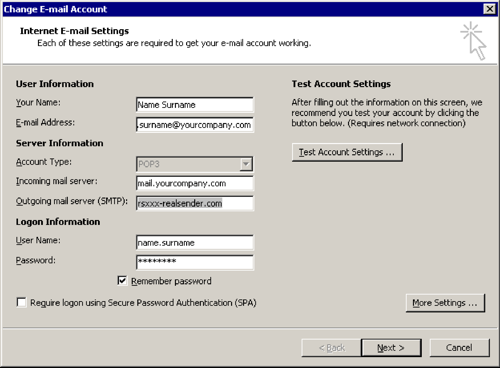
Change E-mail Account
Outgoing mail server (SMTP): rsxxx.realsender.com
[More Settings…]
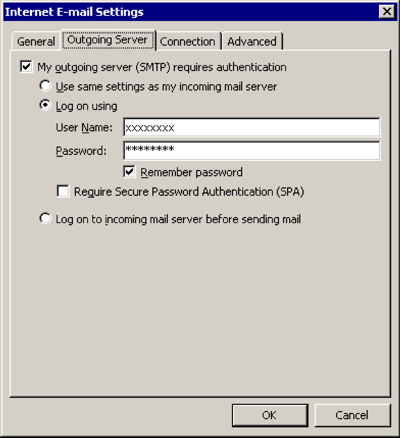
Outgoing Server
[x] My outgoing server (SMTP) requires authentication
[x] Log on using
User Name: (the one we sent you)
Password: (the one we sent you)[x] Remember password
[OK]
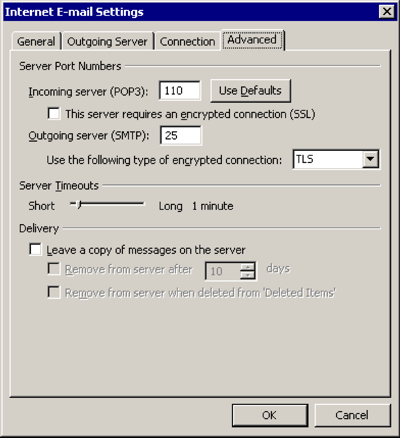
Advanced
Use the following type of encrypted connection: TLS
[OK]

File > [Info]
[Account and Social Network Settings]
[Account Settings…]
[Change…]
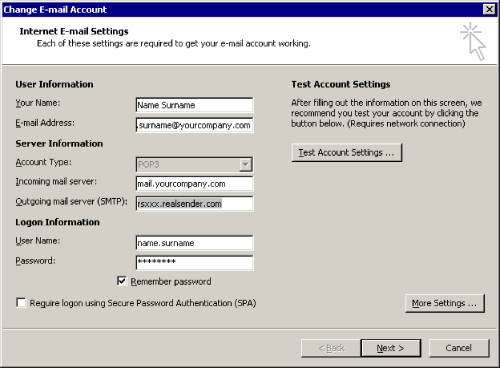
Change E-mail Account
Outgoing mail server (SMTP): rsxxx.realsender.com
[More Settings…]
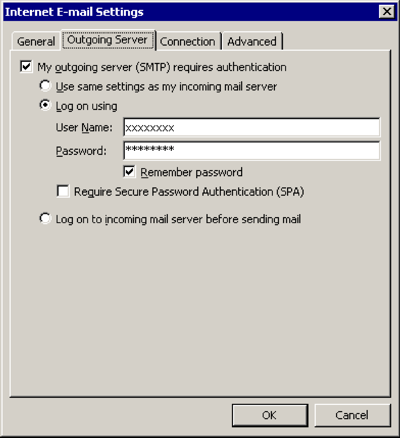
Outgoing Server
[x] My outgoing server (SMTP) requires authentication
[x] Log on using
User Name: (the one we sent you)
Password: (the one we sent you)[x] Remember password
[OK]
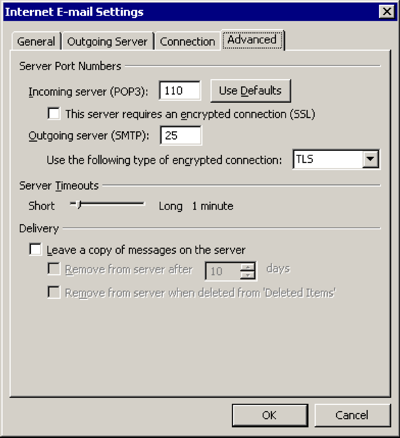
Advanced
Use the following type of encrypted connection: TLS
[OK]
Mail > Preferences… > Server Settings
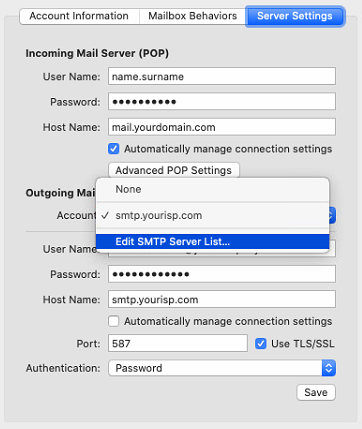
Outgoing Mail Server (SMTP) > Edit SMTP Server List …
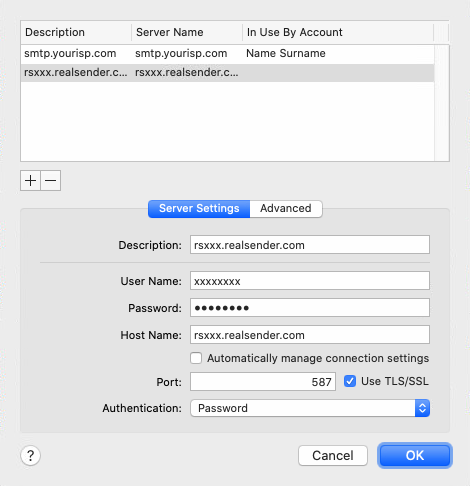
[+] Create an account
Description: rsxxx.realsender.com
User name: (the one we sent you)
Password: (the one we sent you)
Host Name: rsxxx.realsender.com
[ ] Automatically detect and maintain account settings
Port: 587 [x] Use TLS/SSL
Authentication: Password
[OK]
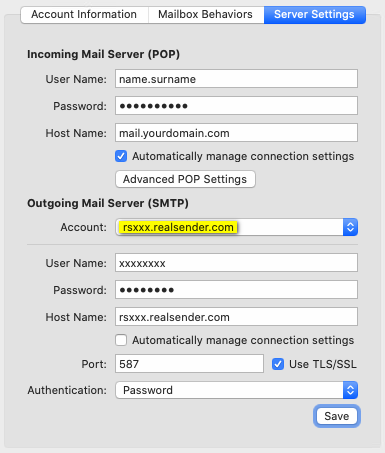
Outgoing Mail Server (SMTP)
Account: rsxxx.realsender.com
[Save]

Tools > Account Settings
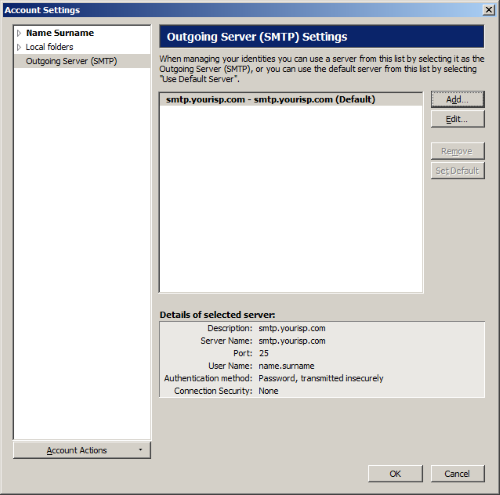
Outgoing Server (SMTP) > [Add…]
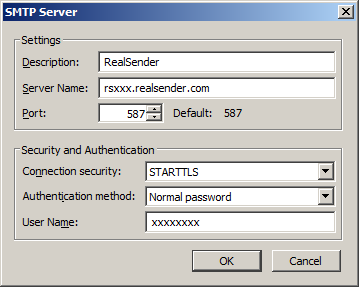
Settings
Description: RealSender
Server Name: rsxxx.realsender.com
Port: 587
Security and Authentication
Connection security: STARTTLS
Authentication method: Normal password
User Name: (the one we sent you)
[OK]
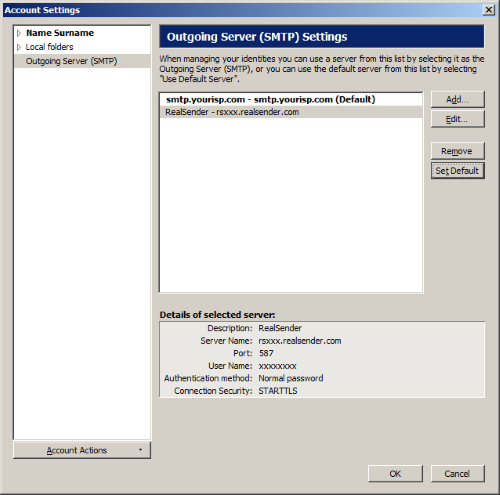
RealSender > [Set Default]
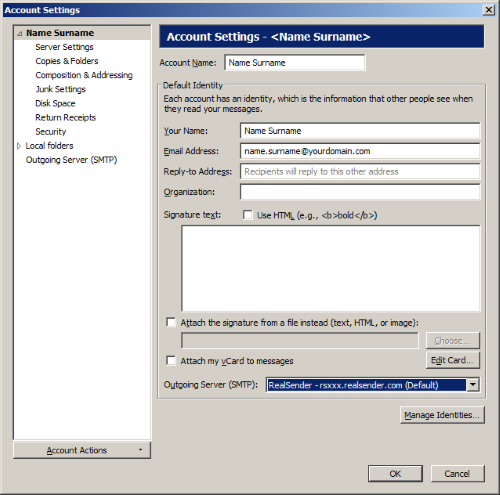
Account settings
(select you email account on the tree at the left side)
Outgoing Server (SMTP): RealSender
[OK]
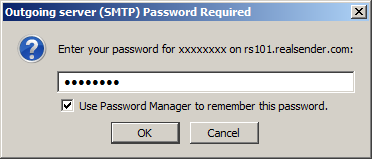
The first time you send a message
Outgoing Server (SMTP) Password Required
Enter your password for…: (the one we sent you)
[x] Use Password Manager to remember this password
[OK]

Launch Desktop > Setup (top right)
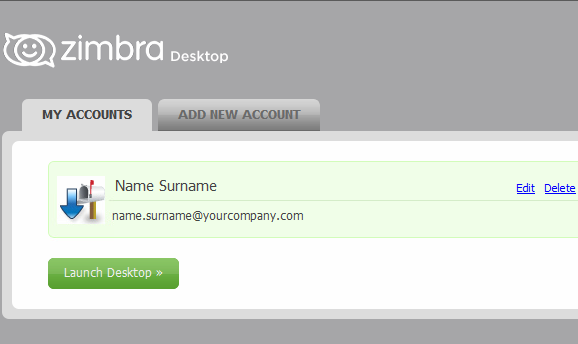
MY ACCOUNTS > [Edit]
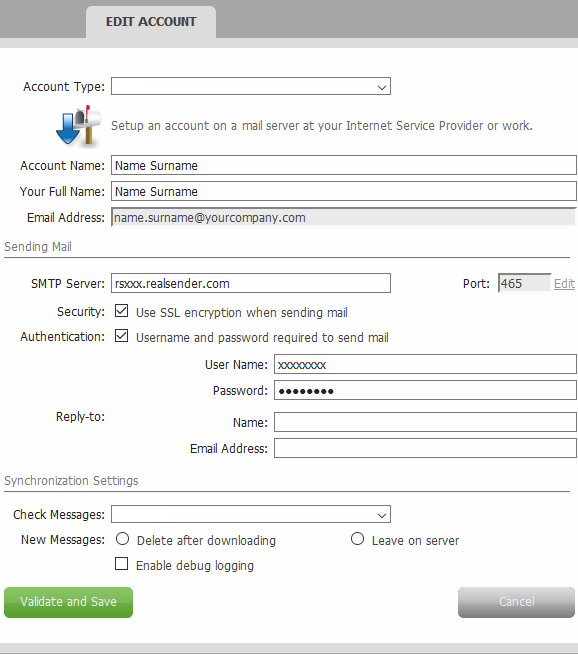
EDIT ACCOUNT
Sending Mail
SMTP Server: rsxxx.realsender.com
Security: [x] Use SSL encryption when sending mail
Authentication: [x] Username and password required to send mail
User Name: (the one we sent you)
Password: (the one we sent you)
[Validate and Save]
To start using RealSender:
We automatically sign emails with DKIM, so you don’t need to do anything else.
Questions? Contact us!

EAC
(Exchange Admin Center)
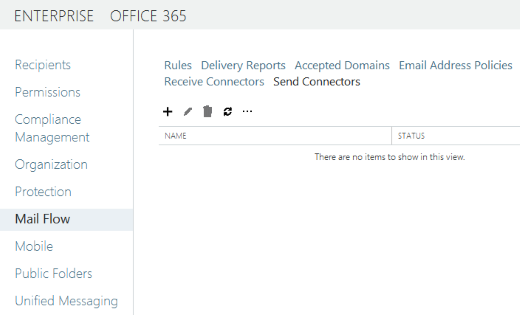
Mail Flow > Send Connectors
[+] New send connector
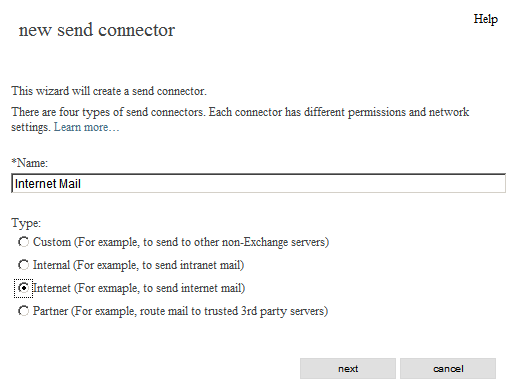
new send connector
*Name:
Internet Mail
Type:
[x] Internet (For example, to send internet mail)
[next]
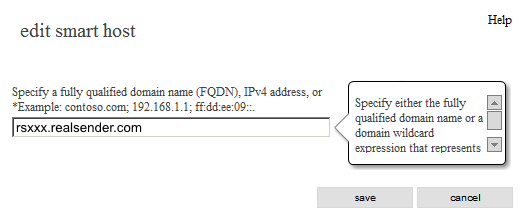
edit smart host
Specify a fully qualified domain name (FQDN), IPv4 address, or IPv6 address:
rsxxx.realsender.com
[save]
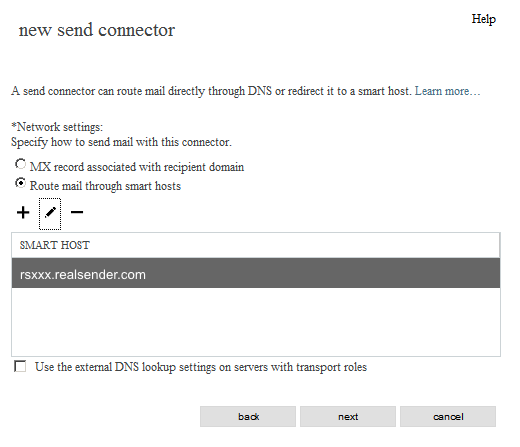
new send connector
*Network settings:
[x] Route mail through smart hosts
(unchanged)
[next]
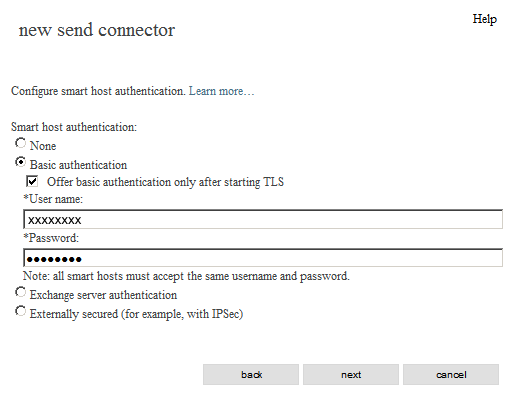
new send connector - authentication
Smart host authentication:
[x] Basic authentication
[x] Offer basic authentication only after starting TLS*User name:
(the one we sent you)*Password:
(the one we sent you)
[next]
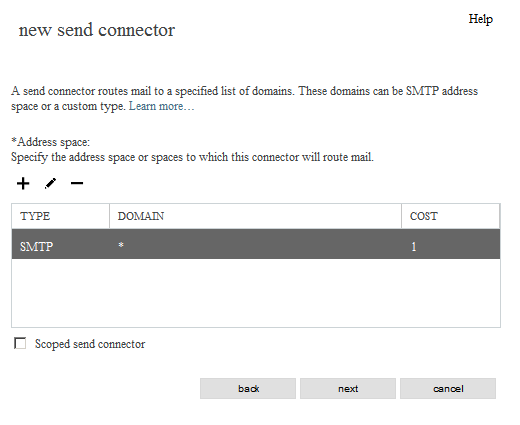
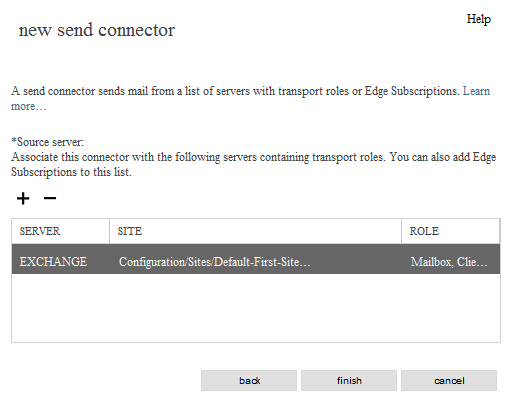
new send connector - routing
*Address space:
TYPE: SMTP
DOMAIN: *
COST: 1
[next]
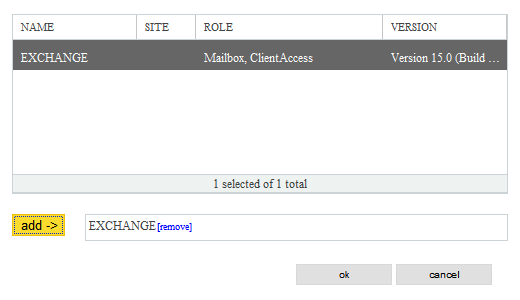
new send connector - which exchange server
[EXCHANGE]
[add ->] EXCHANGE
[ok]
[finish]

Microsoft Office 365 Admin center
Left-menu > Admin
Microsoft 365 admin center > … Show all
Microsoft 365 admin center > Admin centers > Exchange
Exchange admin center > Mail flow > Connectors
Connectors > Add a connector
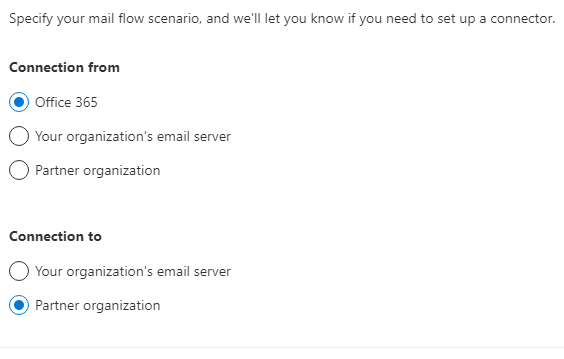
Connection from: [x] Office 365
Connection to: [x] Partner organization[Next]
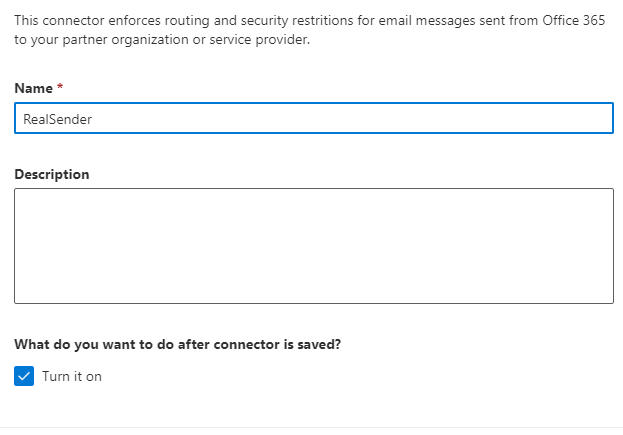
This connector enforces routing and security restritions for email messages sent
from Office 365 to your partner organization or service provider.
Name: RealSender
What do you want to do after connector is saved?
[x] Turn it on[Next]
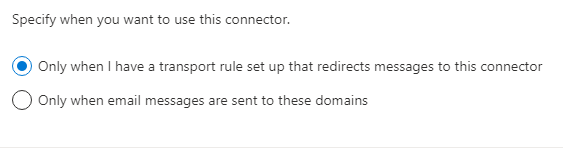
Specify when you want to use this connector.
[x] Only when I have a transport rule set up that redirects messages to this connector[Next]
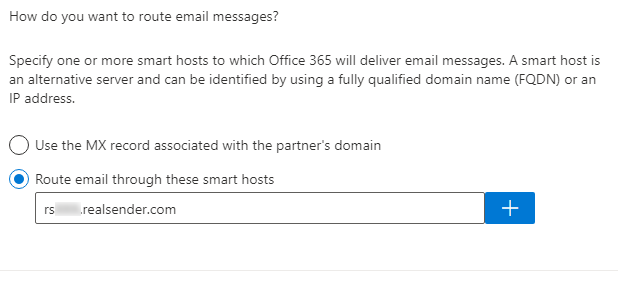
How do you want to route email messages?
Specify one or more smart hosts to which Office 365 will deliver email messages.
A smart host is an alternative server and can be identified by using a fully qualified domain name (FQDN) or an IP address.
[x] Route email through these smart host
rsxxx.realsender.com [+][Next]
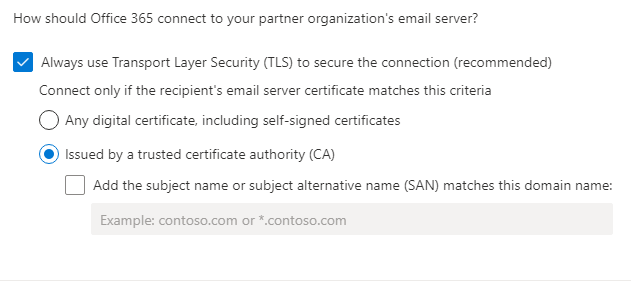
How should Office 365 connect to your partner organization's email server?
[x] Always use Transport Layer Security (TLS) to secure the connection (recommended)
Connect only if the recipient's email server certificate matches this criteria
[x] Issued by a trusted certificate authority (CA)[Next]
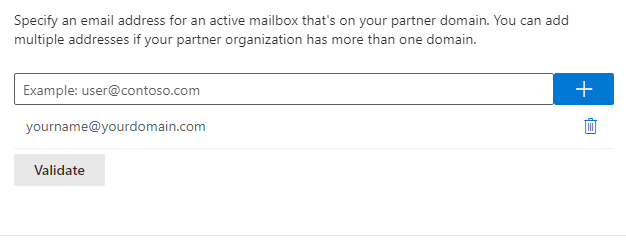
Specify an email address for an active mailbox that's on your partner domain.
You can add multiple addresses if your partner organization has more than one domain.
yourname@yourdomain.com [+]
[Validate]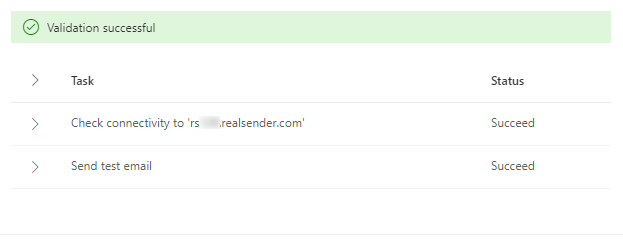
[Validate]
Validation in progress...
Validation successful
> Task Status
> Check connectivity to 'rsxxx.realsender.com' Succeeded
> Send test email Succeeded[Next]
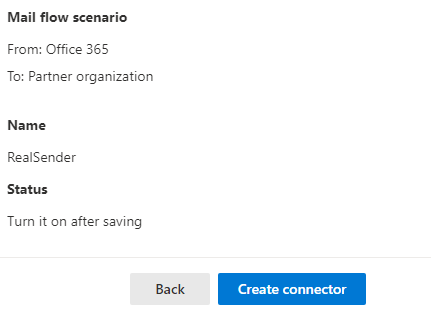
Mail flow scenario
From: Office 365
To: Partner organization
Name
RealSender
Status
Turn it on after saving
Use of connector
Use only when I have a transport rule set up that redirects messages to this connector.
Routing
Route email messages through these smart hosts: rsxxx.realsender.com
Security restrictions
Always use Transport Layer Security (TLS) and connect only if the recipient’s
email server certificate is issued by a trusted certificate authority (CA).[Create connector]

Zimbra Collaboration
(network edition / open source)
> Admin Console
Zimbra Administration
> Configure
> Global Settings
> MTA
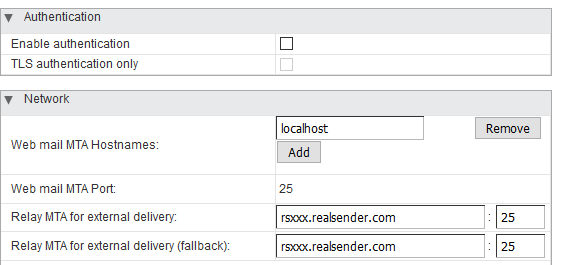
Authentication
Enable authentication [ ]
TLS authenticaton only [ ]
Network
Web mail MTA Hostnames: localhost
Web mail MTA Port: 25Relay MTA for external delivery: rsxxx.realsender.com : 25
Relay MTA for external delivery (fallback): rsxxx.realsender.com : 25

RealSender’s “inxbox” app is a ready-to-use email server,
that receives any message sent to the authorized domain.
It immediately becomes operational as soon as the mx record points to it.
It is often used as an emergency mail server.
If your regular email service goes down,
inxbox will immediately accept any message sent to it.
Without any special configuration required,
such as specifying individual user email addresses.
When configured as historical archive of emails,
an automatic process records messages
by recipient, month, and year.
Main features:
transparently records all the emails
a secure web area to read online inxbox email messages

Email messages are the main channel of modern business communications.
Their accidental loss would great damage the company’s knowledge base.
Furthermore, business correspondence should generally be kept for up to ten years.
!! if your company is using personal mailboxes
such as name.surname@companyname.com
you must have informed the senders before activating this functionWe provide you with a dedicated inbound email domain,
so RealSender’s “inxbox” app archives transparently
all the emails, that you can access via:
a special pop3 mailbox
configured to accept large amounts of emails in a short time
a secure web area
available online through a customized version of our webmail interface
An automatic process archives the messages divided by recipient, month and year.
When associated with RealSender Secure Email Gateway,
all the sent emails are duplicated and archived automatically.
Web-interface features:
A working demo is available in our (free) postmaster tools area:
» inxbox demo temporary email

Email is the main channel for cyber attacks.
Sender address spoofing can be detected by email authentication information.
RealSender’s “spamstop” app shows the results of authenticity checks
directly in the subject of received messages.
It is an efficient anti-spam solution when combined with a filter
that splits messages according to senders that are NOT in your address book.
It can be activated for the entire domain or even just a few email addresses.
Main features:
spf-based email sender check
dkim-based sender and email seal check
at least one of the domains must align with the sending From domain
two SPAM tags added to the subject to highlight fraud
to receive in your inbox only the senders you have previously authorized
to receive email messages only from the senders that you have previously authorized
to protect your email boxes from unwanted senders and dangerous attachments

We want to make sure that the sender address has not been forged/spoofed*.
* = make the message appear from someone other than the actual source
SPF authentication helps us identifying if the message has been sent through an authorized smtp server.
This information is stored in the domain’s dns, that is a safe place, outside the email message.
Only if the message has NOT been authenticated correctly:
the !! (attention) symbol is added to the subject,
one of the following explanatory notes is inserted in the message header, line “X-RealSender”:
:: spf-none :: the sender domain contains no information to authenticate the email
:: spf-softfail :: the smtp server is not listed among the authorized ones but this case should be treated as a "softfail"
:: spf-fail :: the smtp server is not listed among the authorized ones and the email should be rejected or discardedSometimes the information recorded at domain level is not correct/understandable.
:: spf-permerror :: a permanent error has occured (eg. badly formatted SPF record)SPF check is made against the “Mail From” email address, that is hidden in the email headers.
Only the “From” email address is visible. If their root domains are different, this warning is displayed:
:: spf-diff :: the "Mail From" and the "From" root domains are different
DKIM (DomainKeys Identified Mail) allows senders to prove that the email was actually sent by them and has not been modified after being sent.
It achieves this by affixing a digital signature (seal), linked to a domain name, to each outgoing email message.
Only if the message has NOT been signed correctly:
the !! (attention) symbol is added to the subject,
one of the following explanatory notes is inserted in the message header, line “X-RealSender”:
:: dkim-none :: no DKIM-Signature headers (valid or invalid) were found
:: dkim-fail :: a valid DKIM-Signature header was found, but the signature does not contain a correct value for the message Sometimes it’s not possible to execute the check:
:: dkim-invalid :: there is a problem in the signature itself or the public key record. I.e. the signature could not be processed
:: dkim-temperror :: some error was found which is likely transient in nature, such as a temporary inability to retrieve a public keyWhen the message has been signed using a different domain, a “diff” notice is added:
This warning will NOT appear if the sender passes the SPF check:
:: dkim-diff :: the message has NOT been signed by the sender's domain
DMARC (Domain-based Message Authentication, Reporting and Conformance),
is an email authentication standard, developed to combat spoofed domain mail.
In the chapter “3.1. Identifier Alignment” it says:
Email authentication technologies authenticate various (and
disparate) aspects of an individual message. For example, [DKIM]
authenticates the domain that affixed a signature to the message,
while [SPF] can authenticate either the domain that appears in the
RFC5321.MailFrom (MAIL FROM) portion of [SMTP] or the RFC5321.EHLO/
HELO domain, or both. These may be different domains, and they are
typically not visible to the end user.
DMARC authenticates use of the RFC5322.From domain by requiring that
it match (be aligned with) an Authenticated Identifier.
-- https://tools.ietf.org/html/rfc7489#section-3.1It simply means:
when a sender authenticates their email using SPF and/or DKIM,
at least one of the domains must align with the sending From domainThis approach is widely accepted and generally considered
a good practice to identify trusted sender domains.
For SPF authentication
the root domain of the Mail From address must match the root domain of the From address.
Relaxed alignment allows any subdomain to be used and still meet the domain alignment requirement.
For DKIM authentication
the root of the dkim signing domain must match the From domain.
Relaxed alignment allows any subdomain to be used and still meet the domain alignment requirement.
both the rules are respected
the sender domain is fully trusted,
the message arrives unchanged
only one of the two rules is met
the ~ (tilde) symbol is added to the subject,
one of the following explanatory notes is inserted in the message header
~ ... subject ...
X-RealSender: ~ | spf=pass (domain NOT aligned) | dkim=pass | ~~ ... subject ...
X-RealSender: ~ | spf=pass | dkim=pass (domain NOT aligned) | ~
DMARC is being used by more and more companies to protect their senders from spoofing.
Its use requires proper authentication with SPF or DKIM and alignment of From / Mail-From domains.
For more information:
<dmarc> act on fraudulent email
Messages from senders with the _dmarc record,
if they are NOT authenticated, they are highlighted with two [ SPAM ] tags in the subject:
[ SPAM ] ... message subject ... [ SPAM ]Messages without the _dmarc record, when both SPF and DKIM authentication fail,
are reported with a [suspicious] tag in the subject:
[suspicious] ... message subject ... 
RealSender’s “spamstop” app is an efficient anti-spam solution
when combined with a filter that splits messages
according to senders that are NOT in your address book.
Most modern email clients offer this feature.
Here are some configuration examples:
in outlook settings enable: trust email from my contacts
in Thunderbird create a filter with rules 'From isn't in my address book'

Below is the “Settings” screen in Outlook.
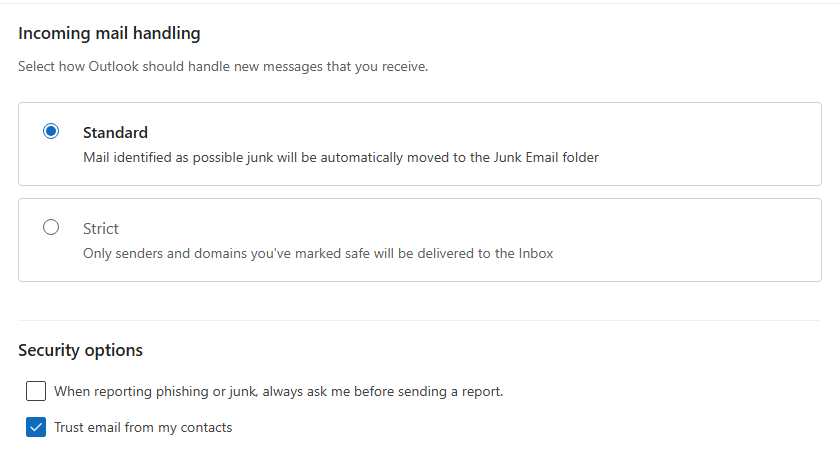
In “Junk email”, check “Trust email from my contacts”.
Press [Save] to record the changes.

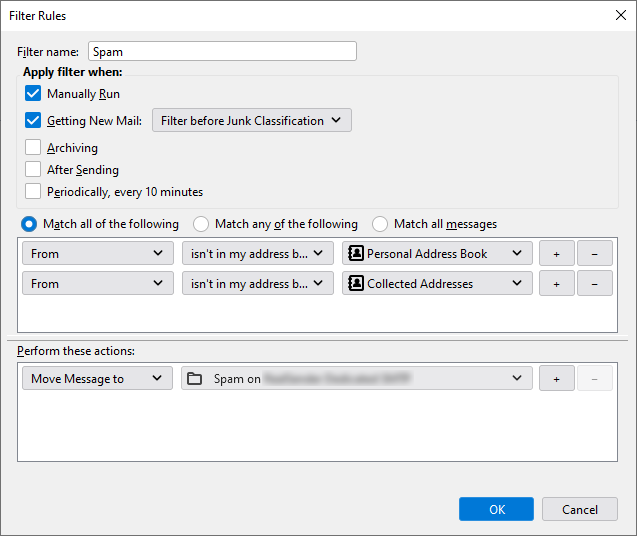
Below is a screenshot of the “Message filter” tool in Thunderbird.
Add conditions with the “Match ALL of the following” option:
Perform these actions: Move Message to: Spam.

Not all email clients provide sophisticated ways to filter emails.
In these cases it is possible to act upstream.
The “Authorized senders” feature allows you to receive messages
only from the senders you have previously authorized
(you can also specify the entire domain, e.g. @example.com):
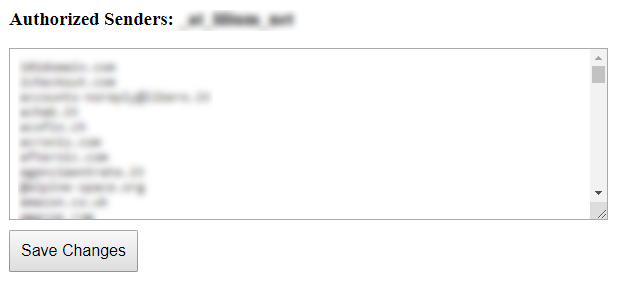
All the regular messages will arrive as usual in your inbox.
All the spam messages will go to a different mailbox
or in the user’s “Junk” email folder of Microsoft 365 Exchange.
No emails will be lost.
You may read the discarded messages mailbox once or more a day.
You will save so much precious time.

This configuration allows to correctly move mail
from UNauthorized senders to the user’s Junk email folder
The messages filtered by SpamStop app will arrive
with the following anti-spam headers and values:
X-Forefront-Antispam-Report: SFV:SKB(message marked as spam by spam filtering
due to the sender’s email address or email domain
NOT present in the list of authorized senders)
The following Action must be activated:
Set the spam confidence level (SCL) of these messages to 6 (spam)
The default value of the SCLJunkThreshold parameter is 4, which means
an SCL of 5 or higher should deliver the message to the user’s Junk email folder.
In the In the Exchange admin center (EAC), go to Mail flow > Rules.
On the Rules page, select Add > Create a new rule in the dropdown list.
In the New rule page that opens, configure the following settings:
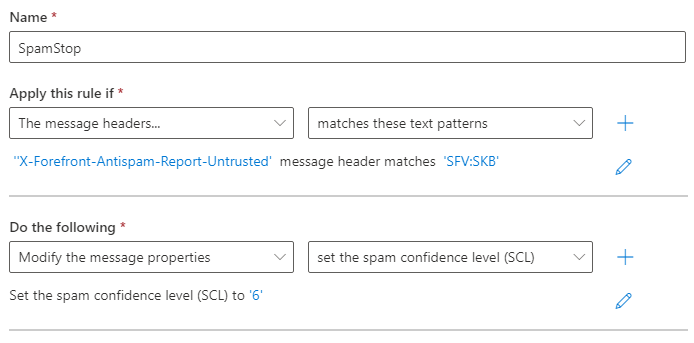
Name: SpamStop
Apply this rule if: ‘X-Forefront-Antispam-Report-Untrusted’
message header matches: ‘SFV:SKB’
Do the following:
Modify the message properties
Set the spam confidence level “SCL” to: ‘6’
Save and Enable the rule.

They add an extra layer of security to your emails.
To protect your email inboxes
from fake senders and dangerous attachments.
Security options that are activated on request:
to receive emails only from senders who have passed authentication checks
to remove all potentially harmful attachments from emails

This is useful when you only want to receive messages from verified senders.
All emails that do not pass the checks are deleted or bounced.
You need to make sure that the sender’s email address has not been spoofed.
This control can be done putting together SPF and DKIM authentication.
SPF confirms the sender’s address and its relationship with the server that sent out the message.
DKIM ensures that email messages (including attachments) are not modified
after they have been “signed” during sending.
In theory it’s that easy, in practice both SPF and DKIM can refer
to a different domain than the sender’s email address.
We check that SPF authentication and DKIM signature are related to the domain in the from address.
In this way no other than the original sender can authenticate the email. This guarantees its origin.

The “remove dangerous attachments” option blocks all potentially harmful attachments
except some safe extensions as pdf, txt, gif, jpg and png.
The recipient receives the message without the attachment.
A warning is added to the beginning of the content, like this:
WARNING: This email violated Your Company's email security policy and
has been modified. For more information, contact your IT Administrator.
An attachment named "example.zip" was removed from this document as it
constituted a security hazard. If you require this document, please contact
the sender and arrange an alternate means of receiving it.There is an interesting case study published on the Internet, which ends with this sentence:
“For us, attachment filtering has been very successful”
– web.mit.edu/net-security/Camp/2004/presentations/reillyb-mit2004.ppt (PowerPoint presentation)

Topics in this area:
newsletter softwares' configuration examples: GroupMail - Inxmail Professional - Joomla AcyMailing - MaxBulk Mailer - phplist - SendBlaster - WordPress MailPoet 3 - WordPress MailPoet 2 - WordPress Mailster
auto set up of one-click unsubscribe for email messages
to analyze bounced messages, extract hard bounces and soft bounces
to send mass mailings directly from your email client
To start using RealSender:
We automatically sign emails with DKIM, so you don’t need to do anything else.
Questions? Contact us!

GroupMail > Tools
Manage Accounts > New
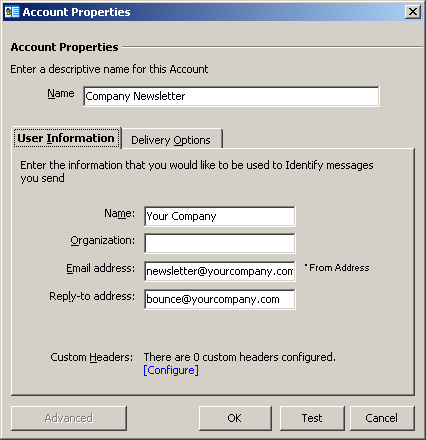
Account Properties
Name / User Infomation:
fill in the form with your company’s data
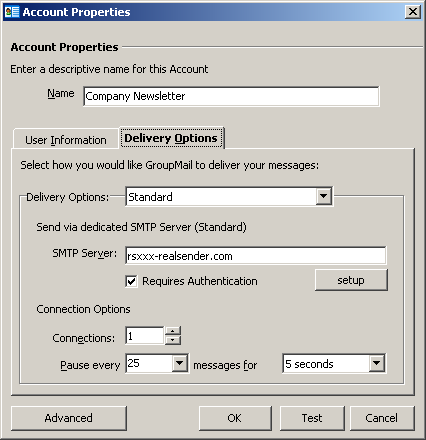
Delivery Options
Delivery Options: Standard
SMTP Server: rsxxx-realsender.com
[x] Requires Authentication
[setup]
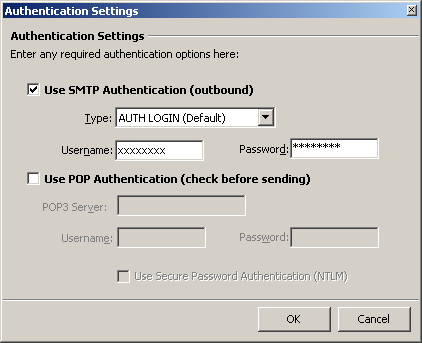
Authentication Settings
[x] Use SMTP Authentication (outbound)
Type: AUTH LOGIN (Default)
Username: (the one we sent you)
Password: (the one we sent you)
[OK]
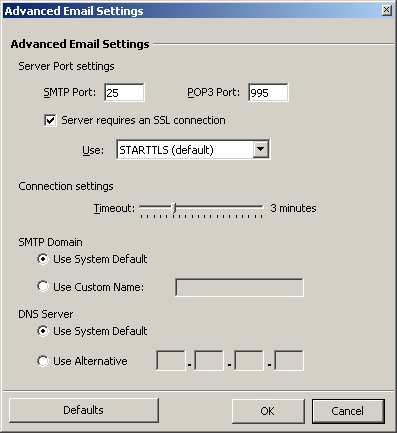
Advanced Email Settings
SMTP Port: 25
[x] Server requires an SSL connection
Use: STARTTLS (default)
[OK]

Global Settings > Administration
> Mail Server > Sending Emails
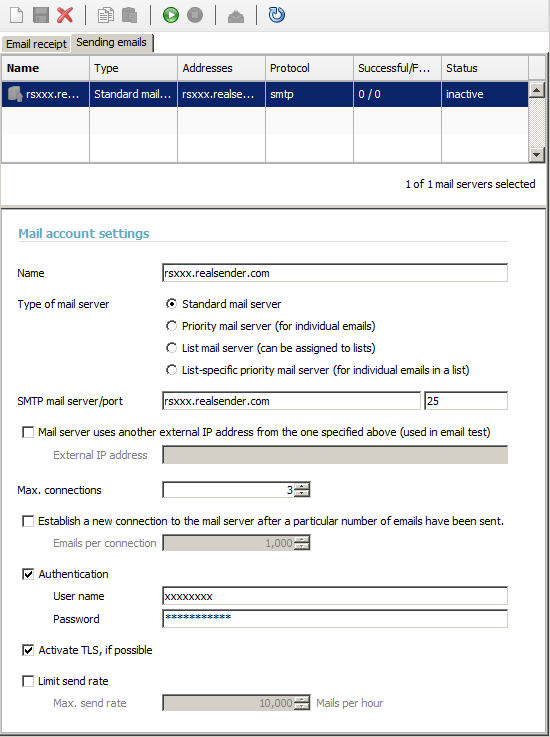
Mail account settings
Name: rsxxx.realsender.com
SMTP mail server: rsxxx.realsender.com - Port: 25
Max. connections: 3
[x] Authentication
User name: (the one we sent you)
Password: (the one we sent you)[x] Activate TLS, if possible
[Save]
[Activate connection to the mail server account]


Joomla > Components
AcyMailing > Configuration
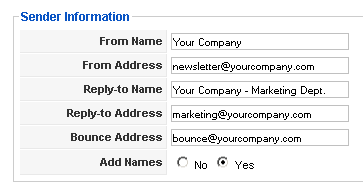
Sender Information
fill in the form with your company’s data
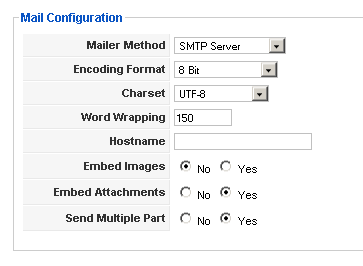
Mail Configuration
Mailer Method: SMTP Server
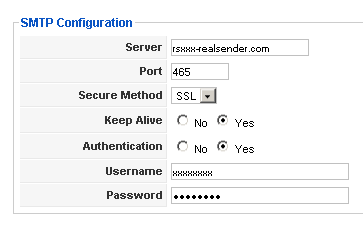
SMTP Configuration
Server: rsxxx.realsender.com
Port: 465
Secure Method: SSLKeep Alive: [x] Yes
Authentication: [x] YesUsername: (the one we sent you)
Password: (the one we sent you)

[Settings]
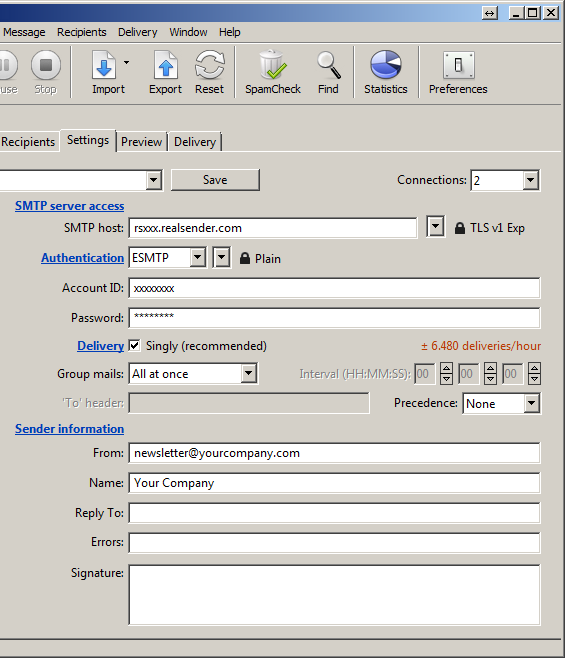
Settings
Connections: 2
SMTP server access
SMTP host: rsxxx.realsender.com - TLS v1 EXP
Authentication: ESMTP - Plain
Account ID: (the one we sent you)
Password: (the one we sent you)
Delivery: [x] Singly (recommended)
Group mail: All at once
Sender information
From: (the sender email address)
Name: (the sender description)
[Save new account as…]
Name: rsxxx
[Create]

Configuration tested on:
phplist, version 3
Attention: make a backup copy before making
any changes on your phplist server configuration files
phplist config
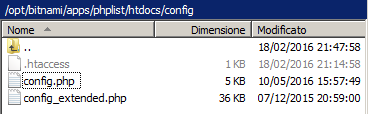
Fill phplist/htdocs/config/config.php
with the correct data:
[…]
define(‘PHPMAILERHOST’, ‘rsxxx.realsender.com’);
[…]
define(‘PHPMAILER’,1);
define(‘PHPMAILER_SECURE’,‘TLS’);
$phpmailer_smtpuser = 'the one we sent you';
$phpmailer_smtppassword = ’the one we sent you’;
$phpmailer_smtpport = 587;
$pageroot = ‘/’;
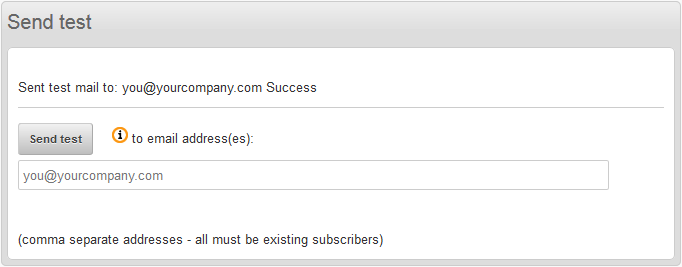

Messages > Send
Send settings:
Send mode: [x] Use SMTP server
SMTP Server: rsxxx.realsender.com
Port: 25 - [x] SSL[x] Authentication required
Username: (the one we sent you)
Password: (the one we sent you)
[Take snapshot]

Sendy

Select a brand > [Add a new brand]
New brand
Brand name
From name
From email
Reply to email
(fill the form with the list name and your company’s data)
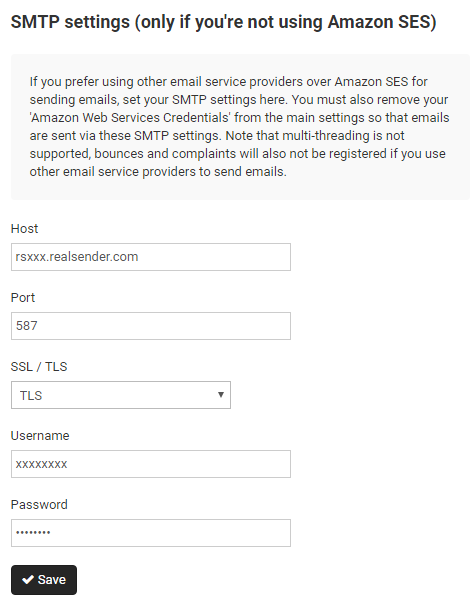
SMTP settings
Host: rsxxx.realsender.com
Port: 587
SSL / TLS: TLS
Username: (the one we sent you)
Password: (the one we sent you)
[Save]

WordPress
MailPoet > Settings
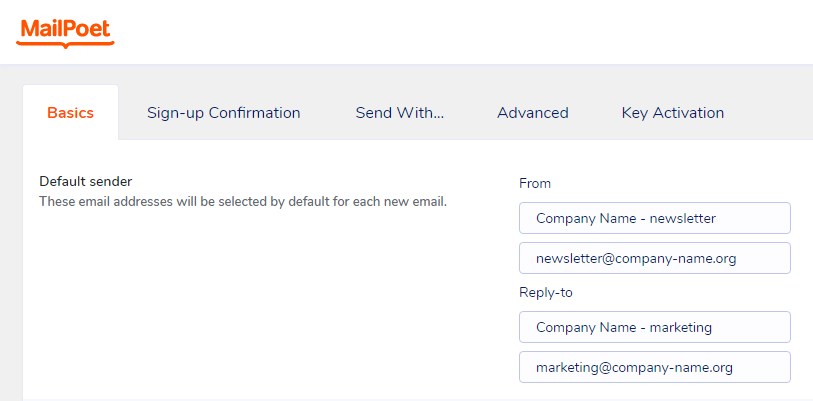
Basics > Default sender
(fill the form with your company’s data)
From:
Company Name - newsletter (description)
newsletter@company-name.org (email address)Reply-to
Company Name - marketing (description)
marketing@company-name.org (email address)
[Save settings]
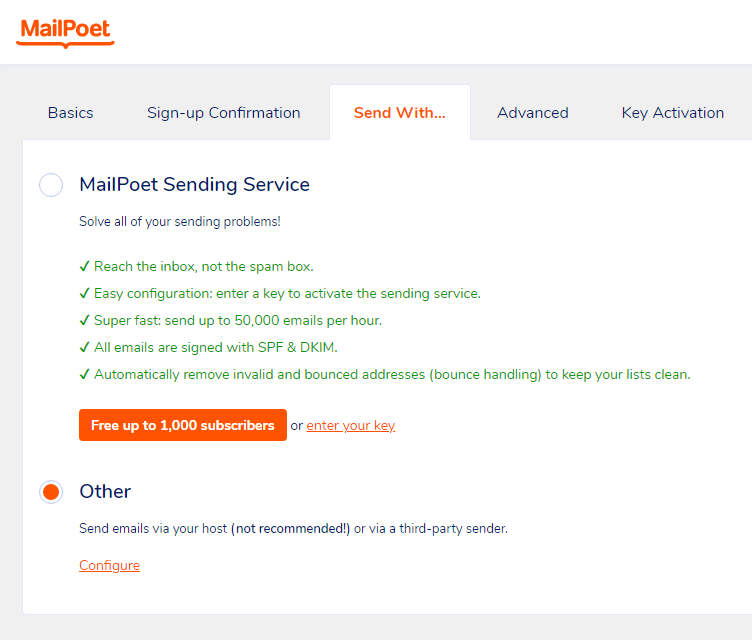
Send With…
[x] Other
Send emails via your host (not recommended!)
or via a third-party sender.[Configure]
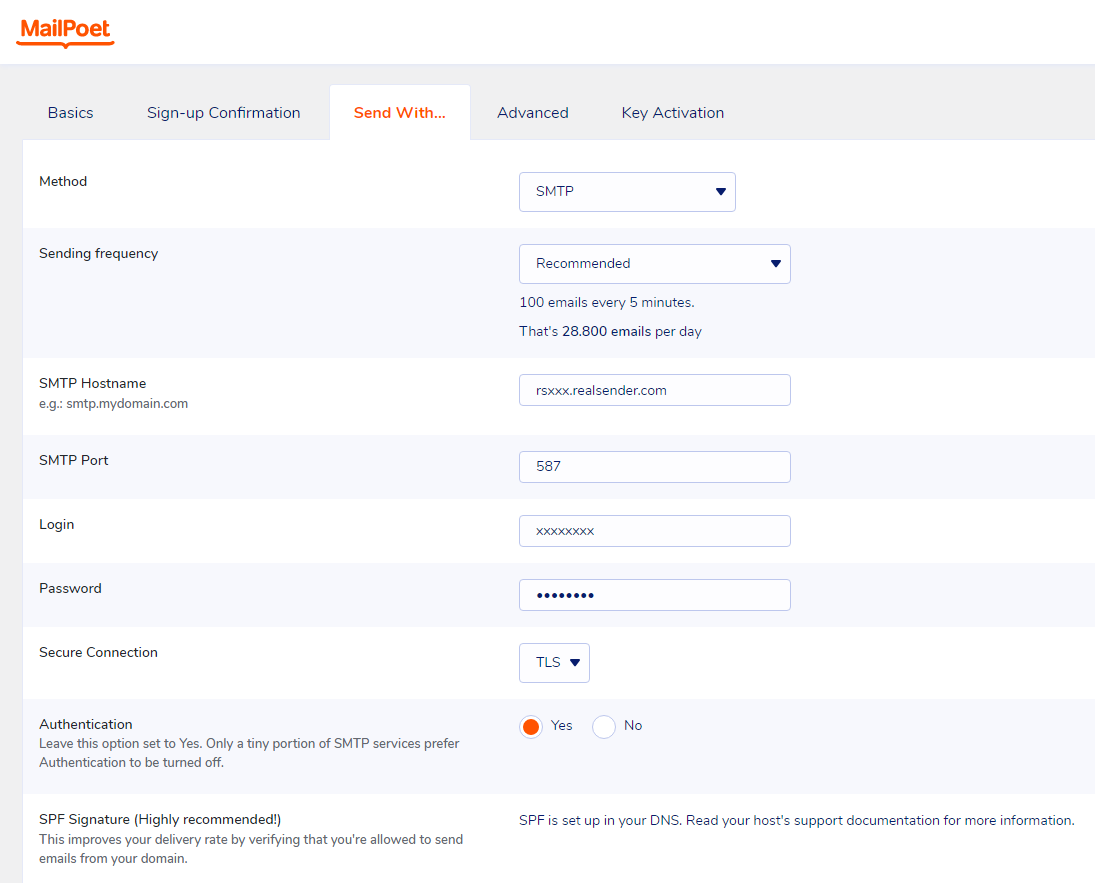
Send With…
Method: SMTP
Sending frequency: Recommended
(100 emails every 5 minutes. That’s 28.800 emails per day)SMTP Hostname: rsxxx.realsender.com
SMTP Port: 587
Login: (the one we sent you)
Password: (the one we sent you)
Secure connection: TLS
Authentication: [x] Yes
[Save settings]
For Premium features and support, on the Mailpoet pricing page
choose the “I just want the Premium with no sending” option.
In this way you can continue to use RealSender,
combining it with a dedicated email address to receive the bounces.
The “Bounce Handler Mailpoet” plugin will also have to be installed.
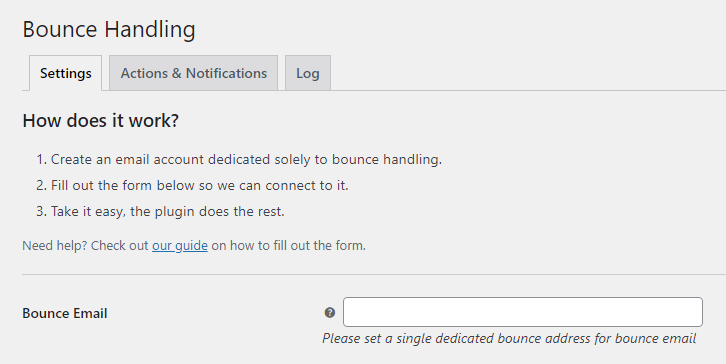
Bounce Handling
Bounce Email:
Please set a single dedicated bounce address for bounce email

WordPress
MailPoet > Settings
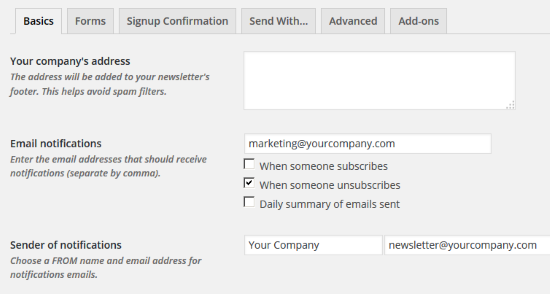
Basics
Email notifications:
fill with the proper email addressSender of notifications:
fill with the newsletter’s
FROM name and email address
[Save settings]
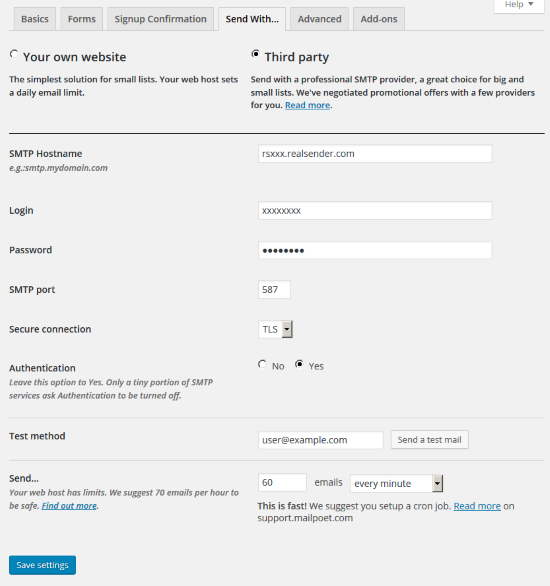
Send With…
[x] Third party
SMTP Hostname: rsxxx.realsender.com
Login: (the one we sent you)
Password: (the one we sent you)
SMTP Port: 587
Secure connection: TLS
Authentication: [x] Yes
Send… 60 emails every minute
[Save settings]

WordPress > Plugins
MailPress > Settings
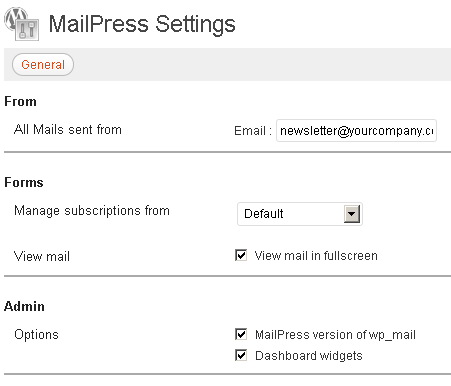
General
From - All Mails sent from:
fill in the form with the sender’s email address and name
if it’s your first MailPress setup
you must press [Save Changes]
to see the additional settings options (SMTP, Test, Logs)
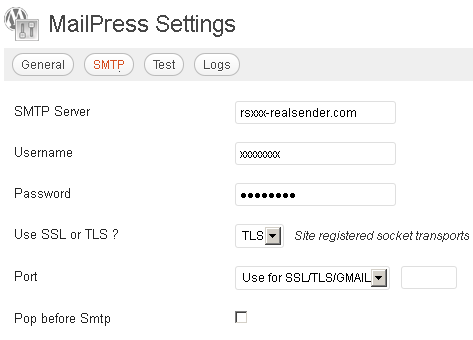
SMTP
SMTP Server: rsxxx.realsender.com
Username: (the one we sent you)
Password: (the one we sent you)Use SSL or TLS ? TLS
Port: Use for SSL/TLS/GMAIL

WordPress
Settings > Newsletter
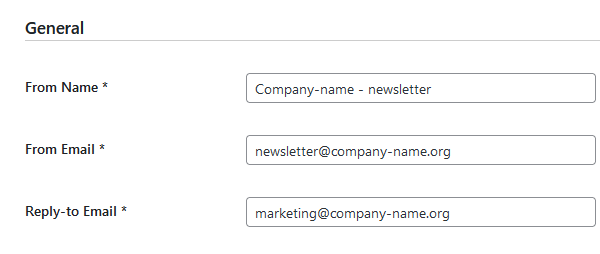
General
From Name:
From Email:
Reply-to Email:
(fill the form with your company’s data)
[Save Changes]
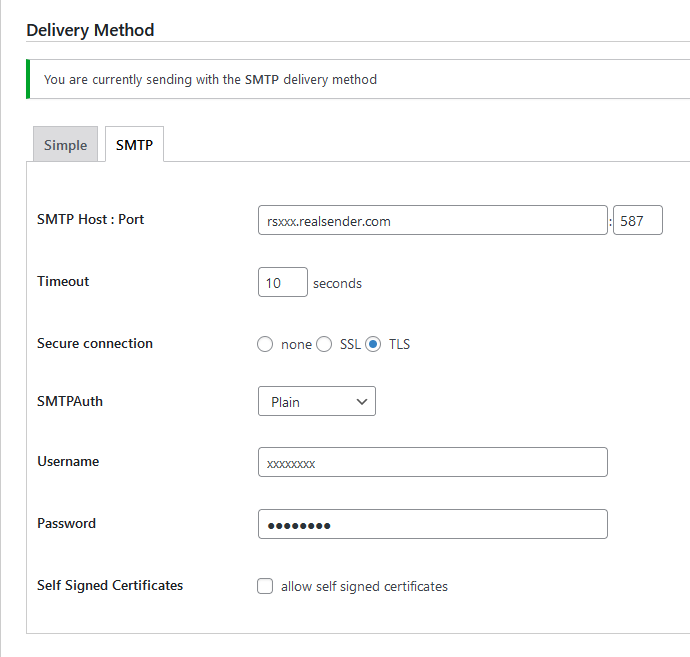
Delivery Method
[SMTP]
SMTP Host : Port rsxxx.realsender.com : 587
Timeout: 10 seconds
Secure connection: [x] TLS
SMTPAuth: Plain
Username: (the one we sent you)
Password: (the one we sent you)
[Save Changes]
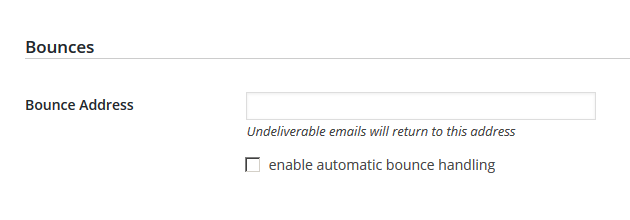
Bounces
Bounce Address:
Undeliverable emails will return to this address
Always give recipients an easy way to unsubscribe from your messages.
Letting people opt out of your messages can improve open rates,
click-through rates, and sending efficiency.
Important: If you send more than 5,000 messages per day,
your marketing and subscribed messages must support one-click unsubscribe.
-- Gmail, Email sender guidelines, 2024Learn more about List-Unsubscribe: headers in RFC 2369 and RFC 8058.
After considering that most of our customers were NOT using List-Unsubscribe: headers in their sent messages,
we decided to add them automatically to each message, only if those headers are not already present.
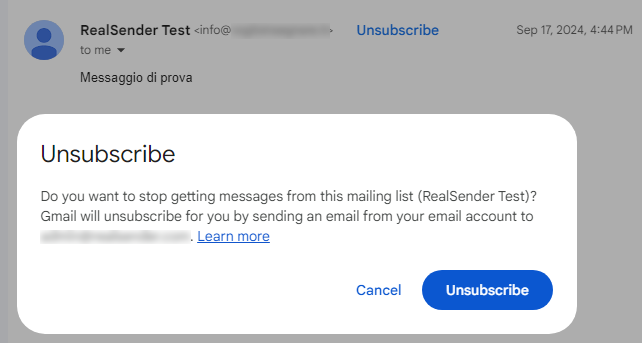
Cancellation requests MUST BE HANDLED within two days.
You must NOT respond with a request to unsubscribe in any other way.
An email message will be automatically generated by Gmail and other providers.
It will be delivered to the email address you communicate to us (even more than one).
Alternatively, at the web address: rsXXX-realsender.com/unsubs
you can access all list-unsubscribe requests received in the last seven days,
in JSON format, as per the example below:
{
"mailbox": "rsXXX",
"id": "20241107T001800-0000",
"from": "<john.doe@gmail.com>",
"to": [
"<abuse@rsXXX-realsender.com>"
],
"subject": "RealSender :: rsXXX Nov-7 4A6NDqsl008203 :: please UNSUBSCRIBE me ::",
"date": "2024-11-07T00:18:00.938050657+01:00",
"posix-millis": 1730935080938,
"size": 4350,
"seen": false
},
Repeated sending to wrong / inactive recipients is considered “spammer behavior”.
In recent years, more and more smtp servers have been blacklisted for this reason.
The most noticeable error occurs when the Mail-From/Return-Path address mailbox,
the one receiving the bounced messages, is full or non-existent.
By sending thousands of messages, if 20% come back, it’s easy to fill even a large inbox in minutes.
Receiving all bounced messages without reading them could be considered a minor flaw.
You keep sending emails to addresses that bounce back, with error details that no one cares about.
In both cases, the result is that the smtp server is blacklisted. In this way,
not only will messages not be delivered to invalid recipients, but valid recipients will also receive them as SPAM.
To solve the first problem, we have been offering “newsletter mailboxes” for a long time.
Analyzing bounced messages is more difficult and requires a tool that works very well.

We chose “Sisimai: Mail Analyzing Interface”, formerly known as bounceHammer 4: an error mail analyzer.
An open source software, that parses RFC5322 bounce mails and generates structured data as JSON.
To get an idea of all the possible error codes that Sisimai parses, take a look at “The SMTP Field Manual”,
a collection of raw SMTP error code responses from major email service providers.
Implementing the bounce handler within RealSender is simple.
The “bouncehandler” app starts checking the bounced messages.
Two blocklists are activated:
the hard bounces blocklist
contains all the email addresses that generated a permanent error,
such as user unknown or host unreachable
the weekly hard bounces log is available at the web address:
https://…hardbounces.email.weekly
the soft bounces blocklist
contains all the email addresses that generated three or more transient errors,
such as mailbox full, at least one week away from each other
the weekly soft bounces log is available at the web address:
https://…softbounces.email.weekly
Sending messages to a blocklisted recipient will generate an error like this:
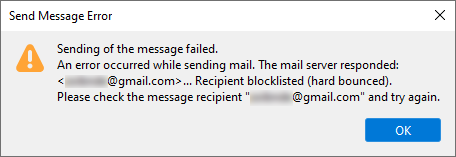
We provide you with the following files,
as web addresses, protected by password or IP address:
https://…bounces.json
the details of the bounces received in the last seven days, in JSON format, such as:
{
"feedbacktype": "",
"addresser": "info@circuitocinemascuole.com",
"diagnostictype": "SMTP",
"timezoneoffset": "+0200",
"lhost": "linp.arubabusiness.it",
"destination": "gmail.com",
"timestamp": 1635536166,
"senderdomain": "circuitocinemascuole.com",
"deliverystatus": "5.1.1",
"token": "daad8f8fc89cef70e1406a9d2b38be6c35326e03",
"recipient": "...@gmail.com",
"subject": "Prenotazioni aperte_Giornata Internazionale dei Diritti dell'Infanzia e dell'Adolescenza_Film FIGLI DEL SOLE",
"origin": "/home/rs109-bounce/Maildir/new/1635528969.21113_0.rsbox.realsender.com",
"rhost": "gmail-smtp-in.l.google.com",
"reason": "userunknown",
"diagnosticcode": "550-5.1.1 The email account that you tried to reach does not exist. Please try double-checking the recipient's email address for typos or unnecessary spaces. Learn more at https://support.google.com/mail/?p=NoSuchUser z3si7494964ybg.507 - gsmtp 503 5.5.1 RCPT first. z3si7494964ybg.507 - gsmtp",
"messageid": "McuPi4DjtlyhvlSMVNB4wTXsUKQeIy6XwlKoAZuJ4@www.circuitocinemascuole.com",
"listid": "",
"action": "failed",
"softbounce": 0,
"replycode": "550",
"catch": null,
"alias": "",
"smtpagent": "Sendmail",
"smtpcommand": "DATA"
},https://…hardbounces.json
the details of the hard bounces 1 received in the last seven days, in JSON format
https://…hardbounces.email
the list of email addresses that generated a hard bounce 1 in the last seven days
1 = selection criteria: softbounce == 0
https://…softbounces.json
the details of the soft bounces 2 received in the last seven days, in JSON format
https://…softbounces.email
the list of email addresses that generated a soft bounce 2 in the last seven days
2 = selection criteria: softbounce == 1
These are the same files used by the automatic blocklist:
https://…hardbouncesfull.email
the list of all email addresses that generated two or more hard bounces
at least one week away from each other
https://…softbouncesfull.email
the list of all email addresses that generated three or more soft bounces
at least one week away from each other
To receive the bounced messages generated by sending newsletters and mass mailings,
you need to setup additional mailboxes (e.g. bounce@…)
and optionally one mailbox for receiving reply emails (e.g. news@…)
if you want to filter them and send automatic replies to the most common requests.
For this reason we introduced two mailboxes matched to your RealSender account:
bounce@email.youremaildomain.com -> bounce@rsXXX-realsender.com
news@email.youremaildomain.com -> news@rsXXX-realsender.com
Explanation:
Using a Mail-From address (also known as bounce/return-path/envelope address)
with a domain other than the From address
would break the DMARC authentication
To use the "newsletter mailboxes"
you need to set up a sub-domain of the From address
e.g. the From address is: offers@youremaildomain.com
the sub-domain could be: email.youremaildomain.com CNAME rsXXX-realsender.com
the Mail-From address becomes: bounce@email.youremaildomain.comThe suggested configuration follows the rules
to send DMARC compliant emails on behalf of customers.
DMARC allows you to send authenticated emails using a sub-domain (such as email.youremaildomain.com), and still be able to use the top-level domain in the From: header (e.g. From: offers@youremaildomain.com).
No additional settings are required in the DNS of your domain name.
As per RFC1912 section 2.4:
A CNAME record is not allowed to coexist with any other data.
In other words, if email.youremaildomain.com is an alias for rsXXX-realsender.com,
you can't also have an MX record for email.youremaildomain.com, or an A record,
or even a TXT record The mailboxes have been configured so that they can receive
large amounts of emails in a short time, as in the case of bounces.
!!! Please note: email messages are automatically deleted after 7 days !!!
To download the emails, you should configure your email client,
or the application that analyzes the bounced messages,
with the following POP3 server address: pop.rsXXX-realsender.com.
Usernames and passwords are available through the website’s restricted area.

If they are not present, RealSender automatically adds the List-Unsubscribe headers
to your sent messages, as described on the page “make it easy to unsubscribe”.
In the recipient’s messaging app,
after clicking the “Unsubscribe” link, a confirmation request appears:
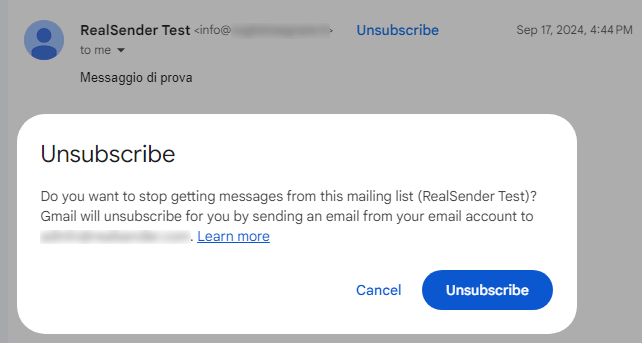
Following the request received, the provider sends us the cancellation notification,
which we immediately deliver to the email address indicated by the customer, even more than one,
with the subject: “RealSender :: rsXXX MM-DD #EMAILID# :: please UNSUBSCRIBE me ::”.
The “bouncehandler” app automatically checks for unsubscribe requests
and blocks new emails from recipients who have requested not to receive future emails.
The “unsubscriptions” blocklist is activated:
it contains all the email addresses that have requested unsubscribe
via the “List-Unsubscribe” function, as described above.
the weekly log of all “unsubscriptions” is available at the web address:
https://…unsubs.email.weekly
Sending messages to a recipient on the blocklist will result in an error like this:
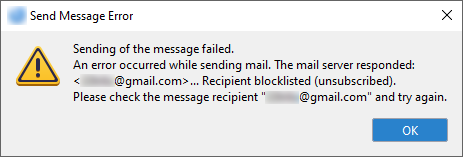
We provide you with the following files,
as web addresses, protected by password or IP address:
https://…unsubs.json
the details of unsubscribe requests received in the last seven days, in JSON format, such as:
{
"mailbox": "rsXXX",
"id": "20241121T181856-0088",
"from": "Jonh Doe <john.doe@bogusemail.net>",
"to": [
"<abuse@rsXXX-realsender.com>"
],
"subject": "RealSender :: rsXXX Nov-1 4ALGbKtb016000 :: please UNSUBSCRIBE me ::",
"date": "2024-11-21T18:18:56.908809804+01:00",
"posix-millis": 1732209536908,
"size": 4057,
"seen": false
},https://…unsubs.email
the list of email addresses that have requested unsubscription in the last seven days
This is the same files used by the automatic blocklist:
https://…unsubssfull.email
the list of all email addresses that requested unsubscription, in alphabetical order

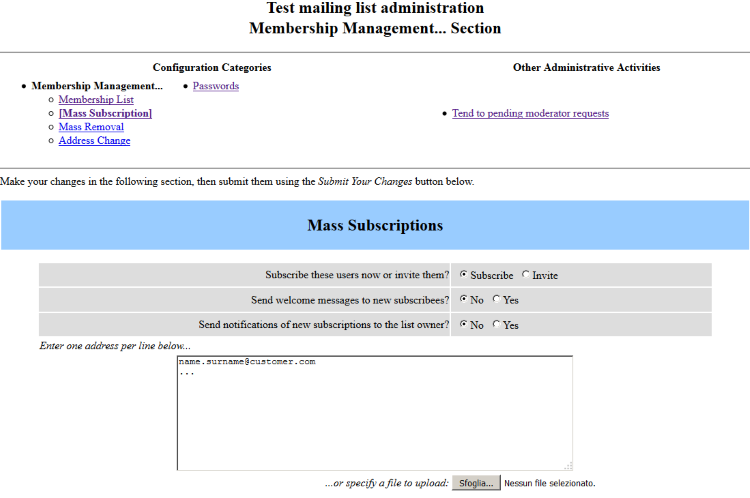
RealSender “copymail” app lets you send mass mailings,
up to thousands of recipients, directly from your email client.
With three easy steps:
Each recipient will receive the message as if it were sent to himself only,
with your email address as the sender.
Essential features:

Repeated sending to incorrect/inactive recipients is considered “spammer behavior.”
RealSender’s “copymail” app handles this automatically and transparently.
The receiver will only see the original sender, who will continue to receive replies from the recipients.
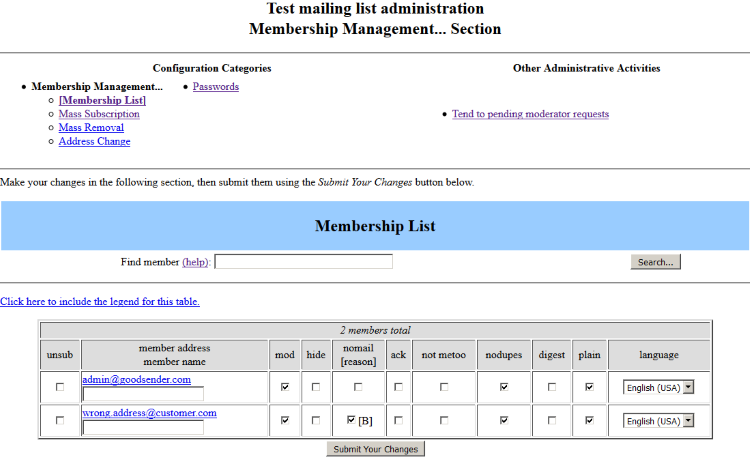
Email messages contain a header that remains invisible to the recipient. It’s called “Return-Path” and allows error messages to be sent to another email address.
Copymail automatically populates it with valuable information that, in addition to allowing them to be received, will also allow it to determine which list the message was sent from and which email address generated the error.
Below is an example of the header inserted in a message,
sent from the “test” list to the recipient "wrong.address@customer.com":
Return-Path: <test-bounces+wrong.address=customer.com@mXXX-realsender.com>
The application identifies two types of errors:
hard bounce (status-code 5.XXX.XXX): the email address generated a permanent error
such as “550 5.1.1 … User unknown” or “5.1.2 … Host unknown”
A permanent error indicates that you should never send to that recipient again.
soft bounce (status-code 4.XXX.XXX): the email address generated a temporary error
such as “452 4.2.2 … Mailbox full”
A transient error indicates that you can retry delivery in the future.
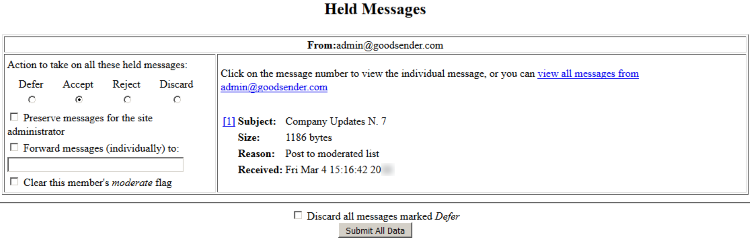
Here’s a brief description of how automatic bounce management works:
After three hard bounces (permanent error, e.g., “user unknown”) or six soft bounces (temporary error, e.g., “mailbox full”), the recipient is blocked and a checkmark is added under the “nomail” column in the subscriber list.
Once the recipient is blocked, three “Your subscription to the list … has been disabled” messages are sent before the recipient is removed from the list.
When the recipient is removed from the list, the administrator receives an email notification.
Note: Only one error per day affects the subscriber’s score, so even if ten bounces are received in the same day, the score will only increase by one.
All these operations may seem simple and manageable even manually by an operator.
This is only possible with very small numbers, up to a few hundred recipients.
On average, about 20% of sent messages are bounced back.
For every 1,000 emails, about 200 are bounced,
which become unmanageable without the help of an automated system.
1. The use of automated calling and communication systems without
human intervention (automatic calling machines), facsimile machines (fax)
or electronic mail for the purposes of direct marketing may be allowed
only in respect of subscribers or users who have given their prior consent.
2. Notwithstanding paragraph 1, where a natural or legal person obtains
from its customers their electronic contact details for electronic mail,
in the context of the sale of a product or a service, in accordance with
Directive 95/46/EC, the same natural or legal person may use these electronic
contact details for direct marketing of its own similar products or services
provided that customers clearly and distinctly are given the opportunity
to object, free of charge and in an easy manner, to such use of electronic
contact details at the time of their collection and on the occasion of each
message in case the customer has not initially refused such use.
-- Unsolicited communications, extract from Article 13 of Directive 2002/58/ECThis rule, now outdated, is still used as a basis of principle. In short:
Beyond the legal implications, failure to comply with these simple rules essentially leads to being labeled a “spammer.” The damage caused can even lead to the inability to reach even those recipients who wish to receive your communications.
RealSender’s “copymail” app provides a link to an “options” page for unsubscribing from each list,
which the customer can include in email messages. Here’s an example:
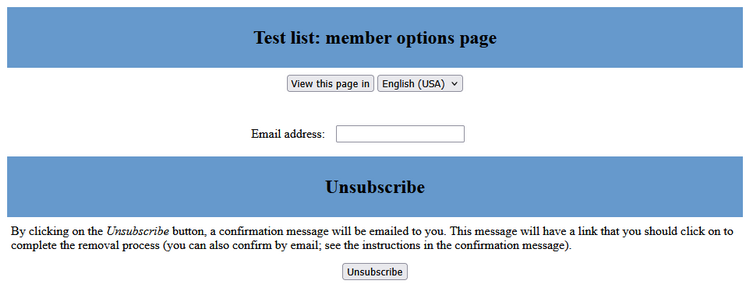
After completing the form, the entered address will receive an email
inviting them to click the link to confirm the cancellation:
We have received a request ... for the removal of your email
address, ... from the ... mailing list. To confirm that you want
to be removed from this mailing list, visit this web page:
(http address for unsubscription confirmation)This same message is sent to those requesting unsubscription
via the “List-Unsubscribe: …” header, which is automatically inserted into every email sent.
This header allows webmail applications like Gmail to activate the “Unsubscribe” link
directly in the interface, without requiring the user to search for it in the message.
To be notified of all unsubscribes made independently by recipients, it is recommended
to activate the notification feature to the administrator’s email address
from the “General Options” of the list:


Topics in this area:
send email messages without authentication
use your own subdomain, such as: smtp.yourdomain.com
how to send email messages via API
how to get via email the output of http requests, generated by web forms or text messages
two ready-to-use scripts to receive instant feedback even with just one click
use the email proxy server to simplify electronic communications and reach mobile devices

Sometimes old softwares or very simple applications
do not allow to issue a secure authentication as RealSender requires.
The solution is to provide an open a port to go through the smtp server,
checking only the connection’s ip address and the sender’s email address.
In this way you’ll be able to send your email messages without authentication,
but you will always be allowed to authenticate whenever possible.
RealSender partners and large organizations
can independently update the list of authorized IPs.

A corporate smtp hostname is used in multiple applications settings.
Changing it is an error-prone activity that takes time.
RealSender allows you to define your subdomain, such as:
smtp.youremaildomain.comWe’ll take care of everything, including SSL certificates
that are required for secure smtp authentication.
This setup will give you complete peace of mind,
knowing that the smtp hostname is under your control.
Your IT staff won’t have to remember where it’s configured
since it will no longer be necessary to change it.
Please note: the special configuration required
involves an additional annual cost
which will be specified during the offer phase.
Topics in this area:
server address, mandatory parameters, JSON answers
charset, content-type, optional parameters, JSON responses
php and curl examples
php and curl examples with attachments
RealSender lets you send email messages via API (Application Programming Interface).
In this way you can dispatch the emails directly from your application, without passing through smtp (Simple Mail Transfer Protocol). We currently support POST requests only.
Server address:
https://rsXXX-api.realsender.com/mail/send
Required/mandatory parameters:
| apiuser | authentication user name |
| apipass | authentication password |
| from | sender email address |
| to | recipient email address |
| subject | subject of the email |
| text | email body in plain text |
| html | email body in HTML format |
If everything is ok, the message will be sent and you will receive a positive JSON answer:
{"success":true}
In case of errors you will get something like this:
{"success":false,"errorMsgs":["Please provide the 'subject' value."]}
The contents must be sent using the UTF-8 international charset.
To test it, add “€uro” in your subject and submit it. If the charset is wrong, you will receive this JSON warning:
{"success":false,"errorMsgs":["The 'subject' value is not correctly encoded. It must be UTF-8 encoded."]}
Depending on whether you have filled in one or both the fields “text” and “html”, the messages will be sent using one of these “Content-Type”:
| text | text/plain (text only) |
| html | text/html (html only) |
| text+html | multipart/alternative (both text and html) email client settings will decide which part is displayed |
Not required/optional parameters:
| fromname | sender description |
| toname | recipient description |
| replyto | email address that will receive the replies |
| returnpath | email address that will receive the bounced mails it must be present among the RealSender’s authorized senders |
| cc | carbon copy email address |
| ccname | carbon copy description |
| bcc | blind carbon copy email address |
| bccname | blind carbon copy description |
| attach | file(s) to be attached - can be present multiple times in the form - 3MB max weight the file contents must be part of the multipart HTTP POST enctype=“multipart/form-data” is required for INPUT TYPE=FILE |
To, cc and bcc values can contain a single email address or a comma separated list of email addresses.
!! Within RealSender the total number of recipients for each piece of email is limited to 25 (it can be increased up to 100).
The server’s responses are in JSON (JavaScript Object Notation) format:
| email sent | {"success":true} |
| email NOT sent | {"success":false,"errorMsgs":["..."]} |
POST request
CURL-less method with PHP
<?php
$url = 'https://rsXXX-api.realsender.com/mail/send';
$data = array('apiuser' => 'the one we provided you', 'apipass' => 'the one we provided you', 'from' => 'sender@example.com', 'to' => 'recipient@example.com', 'subject' => 'subject of the message', 'text' => 'email body in plain text', 'html' => 'email body in HTML format');
// use key 'http' even if you send the request to https://...
$options = array(
'http' => array(
'header' => "Content-type: application/x-www-form-urlencoded\r\n",
'method' => 'POST',
'content' => http_build_query($data),
),
);
$context = stream_context_create($options);
$result = file_get_contents($url, false, $context);
var_dump($result);
?>POST request
CURL method
curl -d 'apiuser=the one we provided you&apipass=the one we provided you&from=sender@example.com&to=recipient@example.com&subject=subject of the message&text=email body in plain text&html=email body in HTML format'https://rsXXX-api.realsender.com/mail/sendPOST request with attachments (max 5: attach1, attach2, …)
CURL-less method with PHP
<?php
require_once 'HTTP/Request2.php';
$config = array('use_brackets' => false,
);
$request = new HTTP_Request2('https://rsXXX-api.realsender.com/mail/send',
HTTP_Request2::METHOD_POST,
$config);
$data = array('apiuser' => 'the one we provided you',
'apipass' => 'the one we provided you',
'from' => 'sender@example.com',
'to' => 'recipient@example.com',
'subject' => 'subject of the message',
'text' => 'email body in plain text',
'html' => 'email body in HTML format');
foreach ($data as $k => $d) {
$request->addPostParameter($k, $d);
};
$request->addUpload('attach1', './sample.pdf', 'sample.pdf', 'application/pdf');
$request->addUpload('attach2', './sample.txt', 'sample.txt', 'text/plain');
$result = $request->send();
var_dump($result);
?>POST request with attachments
CURL method
curl -F 'apiuser=the one we provided you' \
-F 'apipass=the one we provided you' \
-F 'from=sender@example.com' \
-F 'to=recipient@example.com' \
-F 'subject=subject of the message' \
-F 'text=email body in plain text' \
-F 'html=email body in HTML format' \
-F 'attach=@sample.pdf;type=application/pdf' \
-F 'attach=@sample.txt;type=text/plain' \
https://rsXXX-api.realsender.com/mail/sendTopics in this area:
script address, mandatory parameters, hidden and non-hidden fields
not required / optional parameters, hidden and non-hidden fields
simple html web form example
sms forwarding to http configuration example using Teltonika routers
RealSender lets you easily submit http requests, such as web forms contents, via email messages.
In this way you can receive the results of your feedback forms directly in your mailbox.
There’s no need of any special configuration on your side.
The forms can be published in any html webpage or added directly within your email messages.
Script address:
<form action="https://rsXXX.realsender.com/script/form.pl" method="post" accept-charset="utf-8">
Required/mandatory parameters (hidden fields):
| recipient | the email address or the “alias” to which the form submission will be sent for security reasons, the “real” address should be configured at sever level |
| required | this is a list of fields that the user must fill in before they submit the form we suggest to check the “email” field only (content and syntax are verified) additional checks are usually done via javascript, we can provide examples |
| redirect | the user will be redirected to this URL after a successful form submission |
| missing_fields_redirect | the user will be redirected here if any of the ‘required’ fields are left blank |
Required/mandatory parameters (non-hidden fields):
| it will become the sender’s email address of the message | |
| if the email address is correct |
the data will be sent to the configured recipient the user will be redirected to the “redirect” URL |
| if the email address is missing or syntatically wrong |
no mail will be sent the user will be redirected to the “missing_fields_redirect” URL |
Not required/optional parameters (hidden fields):
| subject | the subject line for the email |
| env_report | a list of the user’s environment variables that should be included in the email useful for recording things like the IP address of the user, example: value=“REMOTE_HOST,REMOTE_ADDR,HTTP_USER_AGENT” |
| print_blank_fields | if this is set to “1” then fields left blank will be included in the email |
Not required/optional parameters (non-hidden fields):
| realname | the user’s full name, it will become part of the sender’s email address |
| any_other_field | you can add as many fields you need, no setup is required at server level |
The encoding that will be used for the form submission is the UTF-8 international charset.
To test it, add “€uro” in any of your fields, submit the form and check the email message you’ll receive.
This is a simple html web form example
with two optional parameters: “realname” and “notes”
<form action="https://rsXXX.realsender.com/script/form.pl" method="post" accept-charset="utf-8">
<input type="hidden" name="recipient" value="email_address-or-alias" />
<input type="hidden" name="required" value="email" />
<input type="hidden" name="redirect" value="/form/thankyou.html" />
<input type="hidden" name="missing_fields_redirect" value="/form/error.html" />
Name:<br />
<input name="realname" /><br />
Email:<br />
<input name="email" /><br />
Notes:<br />
<textarea cols="40" rows="2" name="notes"></textarea><br />
<input type="submit" />
</form>The “redirect” and “missing_fields_redirect” landing pages can reside on your server.
You can add as many fields you need, no setup is required at server level.
To receive SMS messages directly in your mailbox
Teltonika routers offer the “SMS Forwarding To HTTP Configuration” option.
You can find it within the Teltonika WebUI: Services > Mobile Utilities > SMS Gateway.
!! The recipient’s domain (yourdomain.com) must be pre-authorized by RealSender !!
Number value name: email
Method: Post
URL: https://rsXXX.realsender.com/script/sms.pl
Message value name: message
Extra data pair 1: recipient | name@yourdomain.com
Extra data pair 2: subject | Text-Message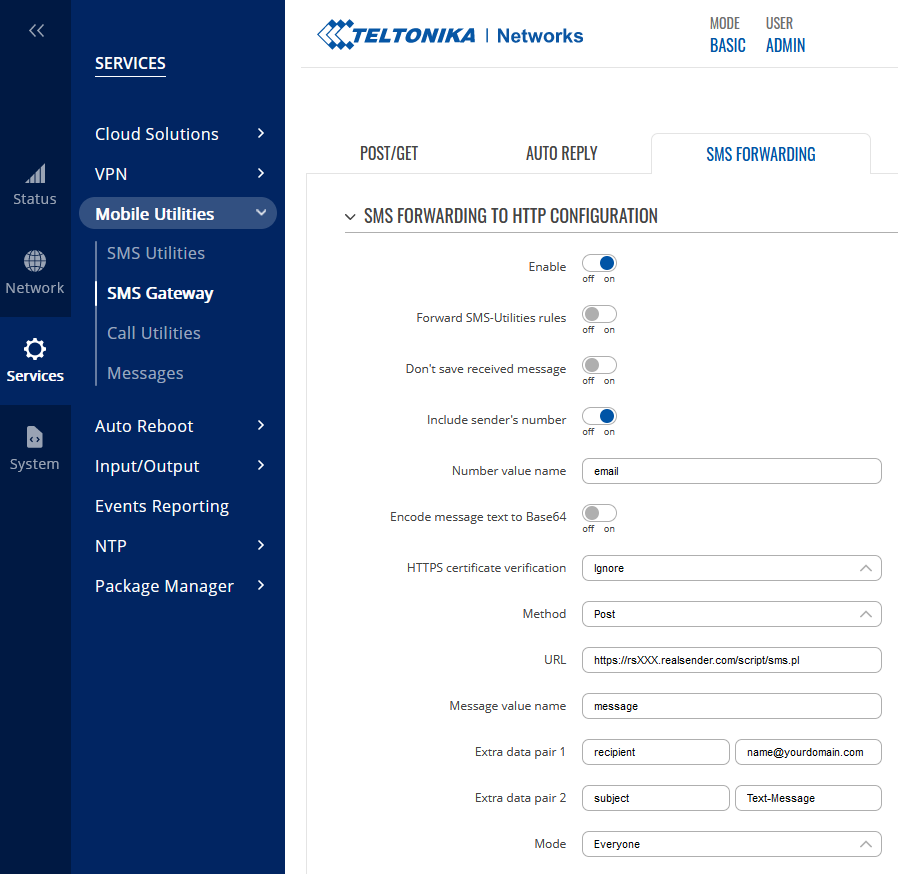
!! A 4G (LTE) connection is required to work properly with RealSender !!
You can setup it up inside Teltonika WebUI: Network > Mobile > SIM card settings
Network type: 4G (LTE) only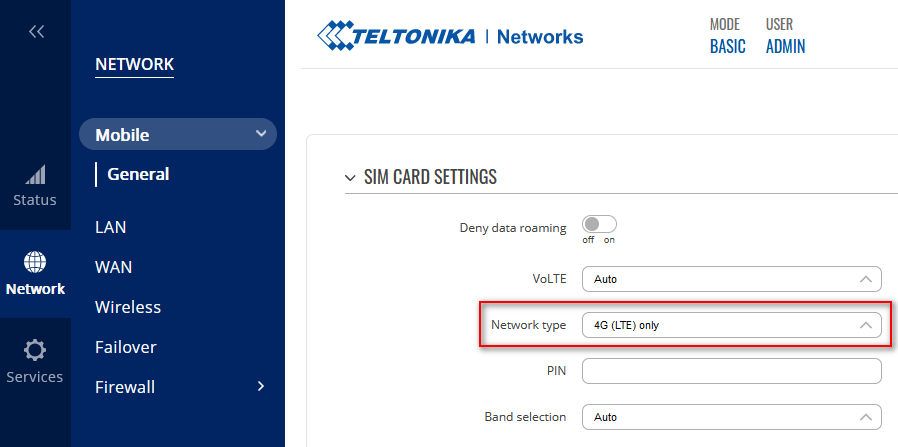
You can set the internet gateway to go through your LAN.
Teltonika WebUI: Network > LAN > NETWORK INTERFACES > [edit]

Just configure the IPv4 gateway and the DNS servers
see the example below (modify it with your own parameters):
INTERFACES: LAN
...
IPv4 gateway: 192.168.1.1
DNS servers: 8.8.8.8 !! mandatory !!The Mobile Data Connection can be disabled in a few ways, see: Disable Mobile Data.
When mobile data is disabled, SMS messaging remains operational.
The easiest way to Disable Mobile Data, is to TEXT to the mobile number: <router_password> mobileoff
You can check the changes in the same way, using the “status” command: <router_password> status
Subject: Text-Message (+41790000000)
Below is the received text message. It was submitted by
(+41790000000) on Monday, June 26, 2023 at 08:31:29 CEST
---------------------------------------------------------------------------
Test Message
---------------------------------------------------------------------------
Receiving clear and structured information via the internet can be complicated.
It needs a user interface to fill in and a server application that sends the data.
RealSender’s “emaildata” app handles server-side interactions.
The “formmail” and “flashmail” scripts allow you to easily create
fillable forms and pre-populated custom links to insert into your email messages,
to allow you to receive immediate feedback, even with just one click.
Main Features:
create simple forms, receive the data in your email
insert pre-populated personalized links into email messages and receive instant feedback

Receiving clear and structured information via the internet can be complicated.
It needs a user interface to fill in and a server application that sends the data.
RealSender’s “formmail” script lets you create simple and responsive forms,
therefore usable also on tablets and smartphones with small screens,
that will send the data directly to your email address.
Few “Drag & Drop” components will help you structure your questions:
The source is downloadable in a ready-to-use “form.html” file:
The message is received in the RealSender’s “temporary email” service: inxbox.realsender.com
NOTE: in the form.html file, three parameters can be changed:
- recipient = the code associated with the recipient's email
to prevent abuse, the email address is pre-encoded in the sending script
leaving "0" the message is received in the RealSender's "temporary email"
- email = the email address of the person filling out the form (ID=email)
it is only used if there is NO "email" field in the form
- subject = the subject of the email message emailRequest a free trial if you want to publish the html file online.
You will thus get an elegant confirmation popup like the one below.
The entered data will be delivered directly to your email box.

for more information on this month's promotion, click here:
https://click.youremaildomain.com/s/flash.pl?promo=yesif you wish to participate in the event, click here:
https://click.youremaildomain.com/s/flash.pl?event=yesto order the new product, click here:
https://click.youremaildomain.com/s/flash.pl?newproduct=yesIf you add the email address at the end of the link, as indicated below,
the reply-to will be inserted, the response will go to the email of the person who clicked:
&email=name@example.comTo set the “landing page” displayed after sending the data,
add the “rdir” parameter to the end of the link, as shown below:
&rdir=/okAlternatively indicate your website address, for example:
&rdir=www.example.com/thankyouTo prevent the links included in your communications
from being considered as a “phishing attempt”,
a subdomain of the sending domain must be configured, for example:
click.youremaildomain.com CNAME click.realsender.comThe notification recipient, even more than one, is set in the script.
You will let us know it during the configuration phase.
In the examples above, notifications reach
our temporary email, which can be found at:
https://inxbox.realsender.com/monitor

The email proxy server allows you to:
Main Features:
instantly connect your entire IT infrastructure to certified email providers
squeeze your email messages into a single line, convert email attachments into links
send notifications to the ntfy app, available on Android and iPhone systems
send email messages to the mobile world, receive text messages in your email and reply to text messages from your email

Certified Electronic Mail is an email capable of certifying the sending and delivery of a message and providing receipts that can be used against third parties.
There are three operating modes, which can also be combined, to enable sending email messages via certified email:
These email messages are transmitted to another server that authenticates itself with the customer’s certified email SMTP service (such as Aruba, Legalmail, Register, to name a few).
The sender is automatically changed to the customer’s certified email address.
Bounced messages (e.g., user unknown/mailbox full) will be sent to the certified email address indicated as the sender.
Incorrect or no longer valid email addresses must be manually corrected or deleted to prevent further sending, as they could trigger spam protection in the recipient email inboxes.

The “plainmail” app reduces your emails to a single line of text,
it makes email attachments disappear, sending links instead:
Simply add “.plain” to the recipients’ email domain,
they will receive only the subject:
Recipient: email@example.com.plain
Subject: your short message, emoticons are allowedAdditional email content and attachments are ignored,
in their place, the following message will appear:
< PlainMail >
All content except the subject line has been removed.Just write “[A]” in the subject and add an attachment to the email.
The “plainmail” app will automatically convert it into a link.
The domain in the link can be any dedicated domain or subdomain you wish to use.
The file will be DELETED after six months.

ntfy (pronounced “notify”) works as a “publish-subscribe” notification service, in which you send a message to a “topic.” A smartphone or computer running the ntfy app and subscribed to the same topic receives the message as a real-time push notification.
This allows for the delivery of instant alerts generated by scripts, servers, or any other service, allowing users to receive notifications without complex configuration.
Publishers:
you can publish messages on a topic via email by sending an email to a specific address.
For example, you can publish a message by sending an email to topic@ntfy.youremaildomain.com.
The message content matches the email subject.
Only RealSender users are authorized to send emails to this address
Subscribers:
they receive notifications via their smartphone or computer,
with the ntfy app installed and the topic they’ve subscribed to
Topics:
think of topics as channels, with unique names and streams of events that are published within them.
You don’t need to explicitly create topics; just choose a name and use it.
Topic names are public, so it’s wise to choose something that cannot be guessed easily
After the email is sent, the ntfy server receives the message and stores it for that topic’s subscribers.
A subscriber (via the ntfy app) is connected to the topic and receives the message in real time.
It’s a “decoupled system”, publishers don’t need to know their subscribers, and vice versa.
This simplifies its use and management, both for the publisher and the subscriber.
Just write “[A]” in the subject and add an attachment to the email.
The “plainmail” app will automatically convert it into a link.
The domain in the link can be any dedicated domain or subdomain you wish to use.
The file will be DELETED after six months.

Connect your emails to the mobile world,
maximize your business communication opportunities,
without changing your work habits:
Push notifications are the most effective way to reach your customers quickly.
With super high open rates (up to 95%) and top response rates (up to 45%).
– source: Gartner study on Text Messages, year 2019
Recipient: mobilenumber@text.yourdomain.com
Subject: the text message content, emoticons are allowed
(additional email content and attachments are ignored)We will provide you with an industrial router pre-configured for your mobile operator.
Control over the sending and delivery of text messages must be carried out via the operator used.
Our system checks every ten minutes that the router is responding (check power and internet connection).
To avoid abuses, messages must be sent via RealSender, using pre-authorized senders,
with the SPF and DKIM “strict” alignment. Learn more on email authentication - advanced.
The text message replies will be delivered directly to your preferred mailbox,
with an email message like this:
Subject: Text-Message (+41790000000)
Below is the received text message. It was submitted by
(+41790000000) on Monday, July 29, 2025 at 10:57:00 CEST
---------------------------------------------------------------------------
Test Message
---------------------------------------------------------------------------RealSender’s “plainmail” app lets you send text messages directly from your EMAIL.
So you can reply from your favorite email application.
The recipient address is already filled with the original sender number:
Recipient: mobilenumber@text.yourdomain.com
Subject: the content of the reply
(additional email content and attachments are ignored)The conversation between email application and mobile device can thus continue.
Just write “[A]” in the subject and add an attachment to the email.
The “plainmail” app will automatically convert it into a link.
The domain in the link can be any dedicated domain or subdomain you wish to use.
The file will be automatically DELETED after six months.

Topics in this area:
our history and our task
how to contact us for commercial or technical questions
plans for a single dedicated smtp server or multiple dedicated smtp servers
no spam policy and other service details
what we can't provide you
how do we manage privacy
technical terms explanation

During the years 2006-2009, after having distributed
for more than a decade a German email marketing platform,
we knew the importance of the smtp server reputation.
There was only one way to guarantee it:
a dedicated smtp server, with dedicated IP address, for each customer.
It was our first step towards providing innovative solutions,
in a reliable, constantly monitored environment.
Our task is: "to empower your emails".
We work hard for it every day.
Giving you full control and the awareness of the outgoing emails,
so that the recipients will receive and trust your messages.

For commercial or technical questions:
Email: contact@mx.realsender.com
Telephone: +41 61 5000365
Text messages: +41 79 6276163
Our office is open Monday to Friday, between 9:00 a.m. and 7:00 p.m. (Central European Time).
How to reach us:
VAT/EU VAT ID no. IT02457460125
 |
RealSender single dedicated smtp server it can send up to 10,000 emails per week (generally used for 1-to-1 / transactional emails) |
 |
HighSender one email gateway to multiple dedicated smtp servers relays over 2 to 100 servers, automatically balanced it can send up to 1,000,000 emails per week (generally used for newsletters / mass mailings) |
services identified as “apps” have an additional cost please contact us for more information |
completely free, no obligation trial period
90 days money back guarantee after purchase
addresses |
usage (GB) |
(€ is for EU only) |
(emails that can be sent) |
|
|---|---|---|---|---|
| RealSender 100x3 | 100 | 9 | 990 $/€ | up to 30,000 |
| RealSender 50x2 | 50 | 6 | 590 $/€ | up to 20,000 |
| RealSender 25 | 25 | 3 | 390 $/€ | up to 10,000 |
| RealSender 10 | 10 | 2 | 240 $/€ | up to 6,000 |
| RealSender 5 | 5 | 0.5 | 190 $/€ | up to 2,000 |
the weekly limit may be lower if we experience delivery issues
do you need more email “from” addresses or more traffic? please contact us
x3 = the messages will be sent through three dedicated smtp servers, in two different datacenters:
if one stops working or is unreachable, the other two will continue relaying your messages
x2 = the messages will be sent through two dedicated smtp servers, in different datacenters:
if one stops working or is unreachable, the other will continue relaying your messages
1 GB traffic is generated sending approx. 10,000 emails of 100 KB each
on “email from addresses” and “weekly traffic” we have +20% tolerance limit
when the limit is exceeded you will be contacted to perform the upgrade
RealSender has a zero tolerance for SPAM (unsolicited email advertising)
Customers sending out unsolicited commercial email or prohibited advertising
or other harassing or illegal materials through email,
will be subject to immediate account termination without any refund
completely free, no obligation trial period
90 days money back guarantee after purchase
addresses |
usage (GB) |
(emails that can be sent) |
||
|---|---|---|---|---|
| HighSender 4 | n.a. | 8 | contact us for a quote | up to 40,000 |
| HighSender 3 | n.a. | 6 | contact us for a quote | up to 30,000 |
| HighSender 2 | n.a. | 4 | contact us for a quote | up to 20,000 |
the weekly limit may be lower if we experience delivery issues
do you need a higher weekly limit? please contact us
1 GB traffic is generated sending approx. 10,000 emails of 100 KB each
on “weekly traffic” we have +20% tolerance limit
when the limit is exceeded you will be contacted to perform the upgrade
n.a.: only one “email from address” is generally used, please ask if you need more
RealSender has a zero tolerance for SPAM (unsolicited email advertising)
Customers sending out unsolicited commercial email or prohibited advertising
or other harassing or illegal materials through email,
will be subject to immediate account termination without any refund
RealSender has a zero tolerance for SPAM (unsolicited email advertising). Customers sending out unsolicited commercial email or prohibited advertising or other harassing or illegal materials through email, will be subject to immediate account termination without any refund. Repeated mailing to wrong recipients and the failure to comply with the weekly limit are considered a “spammer behaviour”.
The “email from addresses” for each RealSender account must be under one or more domain names registered by the same company. Each server can send up to 10,000 emails per week. The number of recipients for each piece of email is limited to 100. RealSender service is provided for business use only: both a full mailing address and tax id number are required.
RealSender simply conveys the emails and does not check the content thereof under legal, factual or other aspects. RealSender is furthermore not responsible for the content of the emails it conveys.
Customer agrees to indemnify RealSender against any liability for any and all use of Customer’s account. Furthermore, Customer agrees to indemnify and hold RealSender harmless from any claims and expenses, including reasonable attorney’s fees, related to Customer’s violation of the Service Agreement or Customer’s direct or indirect damage to another party.
Customer expressly agrees that use of RealSender’s service is at customer’s sole risk. Neither RealSender nor any of its information providers, licensers, employees, or agents warrant that the service will be uninterrupted or error free; nor does RealSender or any of its information providers, licensers, employees, or agents make any warranty as to the results to be obtained from use of the service. the service is distributed on an “as is” basis without warranties of any kind, either express or implied, including but not limited to warranties of title or implied warranties of merchantability or fitness for a particular purpose or otherwise, other than those warranties which are implied by and incapable of exclusion, restriction, or modification under the laws applicable to this service agreement. Neither RealSender nor anyone else involved in creating, producing or delivering the service shall be liable for any direct, indirect, incidental, special or consequential damages arising out of use of the service or inability to use the service or out of any breach of any warranty. Customer expressly acknowledges that the provision of this paragraph shall also apply to all third party content and any other content available through the service.
Upon notice provided in written, faxed or emailed form to the Customer, RealSender may modify this Service Agreement or prices, and may discontinue or revise any or all aspects of the Service in its sole discretion without prior notice.
RealSender and Inxbox are registered trademarks in EU.
For each customer, a dedicated smtp server is prepared, tuned and kept active 24/7.
This has a minimum cost that you won’t find in shared smtp environments,
which on the other hand offer very few guarantees and high risks for those who use them.
We do not control the content of the messages sent, these can cause the delivery to the Spam / Junk folder.
Some freemail providers, per default deliver messages from unknown senders to the junk mail folder.
Their antispam system learns from what their users do with the messages they receive.
If the individual recipient flags once the received mail as NON spam, it will learn that they are valid messages
and will begin delivering them to the “Inbox” folder instead of “Junk”.
Alternatively, the sender must be in the address book of the recipient or have previously exchanged emails.
Our technical staff will help you to identify these cases and to implement an effective delivery strategy.
RealSender simply conveys the emails on behalf of its customers and does not monitor or archive the content.
We keep the logs of the last 7 days and the statistics related to the traffic generated, which are available to the customers as described here:
Logs & delivery
Statistics
The use of the service is subject to acceptance by our customers of the Terms of service.
In case of abuse we act quickly, thanks to the automatic monitoring system on blacklistings.
All of our servers’ homepages advertise the email address to report unsolicited advertising emails transmitted by our customers: [abuse@realsender.com] (mailto: abuse@realsender.com)
The Data Protection Officer can be reached filling this form.
Closed loop marketing
the process by which customer data can feed your marketing campaigns and drive up sales performance.
DomainKeys Identified Mail (DKIM)
DKIM is an email authentication protocol that enables the sender to use public-key cryptography to sign outgoing emails in a manner that can be verified by the receiver. The DKIM specification is based on the prior protocols Domain Keys and Identified Internet Mail. DKIM is defined in IETF RFC 4871. The DKIM standard is already being adopted by Gmail and other large corporations to completely eliminate phishing and spoofing from internet mail.
email authentication technology that verifies whether an email message originates from the domain name it claims to have been sent from [2]. Ensuring a valid identity on an email has become a vital first step in stopping spam, forgery, fraud, and even more serious crimes. [3]
Internet Engineering Task Force (IETF)
the Internet Engineering Task Force is a large open international community of network designers, operators, vendors, and researchers concerned with the evolution of the Internet architecture and the smooth operation of the Internet. It is open to any interested individual. The goal of the IETF is to make the Internet work better.
Message Transfer Agent (MTA)
any system running SMTP routing software that can take a message, process it, look up destination information in DNS (or other routing table), and deliver to the intended receiving system. MTAs are typically server applications such as Sendmail, Microsoft Exchange, Postfix, Lotus Domino, qmail, PowerMTA, etc.
secure smtp
extension to the SMTP service that allows an SMTP server and client to use TLS (Transport Layer Security) to provide private, authenticated communication over the Internet. [1]
Sender Policy Framework (SPF)
SPF is a path-based email authentication protocol that allows email receivers to determine if the sender is authorized to use the domains in the message’s header by evaluating the IP address of the sender’s outbound MTA based on information published by the sender in DNS TXT records. SPF is defined in IETF RFC 4408.
Simple Mail Transfer Protocol (SMTP)
is an Internet standard for electronic mail (e-mail) transmission across Internet Protocol (IP) networks. SMTP was first defined by Jonathan Postel in IETF RFC 821 (1982), and last updated by IETF RFC 5321 (2008) which includes the extended SMTP (ESMTP) additions, and is the protocol in widespread use today. SMTP is specified for outgoing mail transport and uses port 25.
Transport Layer Security (TLS)
the TLS protocol provides communications security over the Internet. The protocol allows client/server applications to communicate in a way that is designed to prevent eavesdropping, tampering, or message forgery. TLS is an IETF standards track protocol, last updated in RFC 5246.
[1] RFC 3207 - SMTP Service Extension for Secure SMTP over Transport Layer Security
[2] 2008 OTA State of the State of Email Authentication Report
[3] Email Authentication by David MacQuigg

Topics in this area:
the minimum settings that are required
get full control over the reputation of your emails
control what happens to your emails
automatically checks the correct operation of the services every ten minutes
Topics in this area:
Sender Policy Framework introduction
validate your email SPF settings sending an email message
DomainKeys Identified Mail introduction
validate your email DKIM settings sending an email message

SPF is the abbreviation of Sender Policy Framework, an email authentication standard,
that lets you declare which are the smtp servers authorized to send emails for your domain.
It allows you to confirm the sender’s address and its relationship with the server that sent out the message.
If emails are sent with your sender domain, the recipient can identify if it has been sent from one smtp server that you recognize.
It’s recommended to configure it, because some recipients may reject your messages if spf is not set at all.
There are two different approaches:
The “soft” setup will produce less/no rejection by the recipients.
The “hard” one will cause some messages to be rejected if the server has not been declared or in some cases when the email has been redirected or sent through a mailing list.
The “hard” setup provides the destination mail server with more faculty to decide whether to accept the message or not, this is the approach that we suggest.
SPF setup requires to know exactly which servers you use to send out email messages.
With RealSender, the TXT record of your domain (example.com) should contain the string
a:example.realsender.com and look like this:
example.com TXT "v=spf1 a:example.realsender.com ~all" With HighSender, the TXT record of your domain (example.com) should contain the string
include:spf.realsender.com and look like this:
example.com TXT "v=spf1 include:spf.realsender.com ~all" These tools will help you validate the configuration:
www.kitterman.com/spf/validate.html *
retrieves SPF records for the specified domain name and determines if the record is valid
spf check online
validates your email SPF settings sending an email message
* = external website link, will open in a new page
Even if everything is set correctly, the message verification may fail
if the email has been redirected (forwarded) or sent through a mailing list.
In these cases, to keep the email authentication consistent,
configure the dkim signature domain to be aligned with the sender’s From address.
See: email authentication advanced » <dkim> alignment for dmarc.

spf@tester.realsender.comhttps://tester.realsender.com/spfRealSender SPF check online will add a subject prefix, if the message has not been authenticated correctly:
!! spf-fail !! the smtp server is not listed among the authorized ones
and the email should be rejected or discarded
!! spf-softfail !! the smtp server is not listed among the authorized ones
but this case should be treated as a "softfail"
!! spf-neutral !! the SPF record specifies explicitly that nothing can be said about validity
!! spf-none !! the sender domain contains no information to authenticate the email Sometimes the information recorded at domain level is not correct/understandable.
!! spf-permerror !! a permanent error has occurred (eg. badly formatted SPF record)
!! spf-temperror !! a transient error has occurredSPF check is made against the “Mail-From” email address, that is hidden in the email headers.
Only the “From” email address is visible. If their root domains are different, this warning is displayed:
!! spf-diff !! the "Mail-From" and the "From" root domains are differentIf the message passes both SPF check AND SPF alignment check for DMARC (relaxed alignment), you will get:
|OK| spf-pass your email passes SPF check + SPF alignment checkIf only one, SPF OR DKIM, passes the alignment check for DMARC (relaxed alignment),
the message is still considered “OK” (trusted) and the ~ (tilde) symbol is added at the beginning:
|~OK| spf-pass your email passes SPF check (not the alignment) + DKIM alignment check
DKIM is the acronim of DomainKeys Identified Mail, an email authentication standard,
designed to guarantee that the email (including the attachments) has not been modified since the “signature” was affixed.
It achieves this by affixing a digital signature, linked to a domain name, to each outgoing email message.
Two keys are used: a “public” and a “private” key:
While sending a message, the smtp server generates an “encrypted hash signature”, based on the email message contents and the private key.
The recipient system can verify the signature in the email header, comparing it with the email content and the sender’s “public” key.
DKIM signatures are not immediately visible to end-users, they are added and verified by the email infrastructure.
RealSender smtp servers sign all outgoing email messages with the dkim signature.
RealSender initially signs all outgoing messages with its own domain connected to the smtp server,
no setup is needed on the user/administrator side.
To get the “dkim domain alignment for dmarc”,
the message must be signed with the same domain of the sender.
With RealSender, you should add two CNAME records
in the dns settings of your domain (example.com), like these ones:
key1._domainkey.example.com CNAME key1._domainkey.yourcompany.realsender.com
key2._domainkey.example.com CNAME key2._domainkey.yourcompany.realsender.comThis tool will help you validate the configuration:
toolbox.googleapps.com *
* = external website link, will open in a new page
A dkim sealed message can’t be modified, but it still can be read by anyone.
A signed message that does not pass the verification, usually gets rejected.
If no changes have been made along the way from sender to recipient, this should not happen.
We’ve experienced rare cases, all related with lines lenght (it must be max 990 characters).
Some applications send the content all in one line or transmit a very long line within the html.
On these occasions the dkim signature gets corrupted, causing the “dkim=fail” check result.

dkim@tester.realsender.comhttps://tester.realsender.com/dkimRealSender DKIM check online will add a subject prefix, if the message has not been signed correctly:
!! dkim-none !! no DKIM-Signature headers (valid or invalid) were found
!! dkim-fail !! a valid DKIM-Signature header was found, but the signature
does not contain a correct value for the message Sometimes it’s not possible to execute the check:
!! dkim-invalid !! there is a problem in the signature itself or the public key record.
I.e. the signature could not be processed
!! dkim-temperror !! some error was found which is likely transient in nature,
such as a temporary inability to retrieve a public keyWhen the message has been signed using a different domain, a “diff” alert will be added to the subject.
This warning will NOT be displayed if the sender passes the SPF check and SPF alignment for dmarc:
!! dkim-diff !! the message has NOT been signed by the sender's domainIf the message passes both DKIM check AND DKIM alignment check for DMARC (relaxed alignment), you will get:
|OK| dkim-pass your email passes DKIM check + DKIM alignment checkIf only one, DKIM OR SPF, passes the alignment check for DMARC (relaxed alignment),
the message is still considered “OK” (trusted) and the ~ (tilde) symbol is added at the beginning:
|~OK| dkim-pass your email passes DKIM check (not the alignment) + SPF alignment checkTopics in this area:
SPF domains out of alignment may cause the DMARC check to fail
DKIM domains out of alignment may cause the DMARC check to fail
Domain-based Message Authentication, Reporting and Conformance
rua messages collection and daily dmarc reports generation online

DMARC is an email authentication standard, developed to combat spoofed domain mail.
For domain alignment it requires that:
when a sender authenticates their email using SPF and/or DKIM,
at least one of the domains must align with the sending From domainTo get it within SPF (Sender Policy Framework), you deal with two domains:
DMARC allows two types of SPF alignment: relaxed alignment and strict alignment.
If you do not specify strict alignment, relaxed alignment is assumed as the default.
With relaxed alignment, only the root domain of the Mail-From address must match the root domain of the From address.
Relaxed alignment allows any subdomain to be used and still meet the domain alignment requirement.
example:
if your Mail-From domain is mail.abc.com and your From domain is abc.com,
your email will pass SPF alignment (the root domains “abc.com” match)
if your Mail-From domain is abc.mail.com and your From domain is abc.com,
your email will NOT pass SPF alignment (the root domains “mail.com” and “abc.com” do not match)
With strict alignment, the domain of the Mail-From address must match exactly the domain of the From address.
example:
if your Mail-From domain is mail.abc.com and your From domain is mail.abc.com,
your email will pass SPF alignment (the domains “mail.abc.com” match)
if your Mail-From domain is mail.abc.com and your From domain is abc.com,
your email will NOT pass SPF alignment (the domains “mail.abc.com” and “abc.com” do not match)

DMARC is an email authentication standard, developed to combat spoofed domain mail.
On domain alignment it requires that:
when a sender authenticates their email using SPF and/or DKIM,
at least one of the domains must align with the sending From domainTo get it within DKIM (DomainKeys Identified Mail),
the dkim signing domain (DKIM-Signature: d=…) must match the sending From domain.
DMARC allows two types of DKIM alignment: relaxed alignment and strict alignment.
If you do not specify strict alignment, relaxed alignment is assumed as the default.
With relaxed alignment, only the root of the dkim signing domain must match the sending From domain.
Relaxed alignment allows any subdomain to be used and still meet the domain alignment requirement.
example:
if your dkim sigining domain is mail.abc.com and your From domain is abc.com,
your email will pass DKIM alignment (the root domains “abc.com” match)
if your dkim sigining is abc.mail.com and your From domain is abc.com,
your email will NOT pass DKIM alignment (the root domains “mail.com” and “abc.com” do not match)
With strict alignment, the dkim signing domain must match exactly the domain of the sending From address.
example:
if your dkim sigining domain is mail.abc.com and your From domain is mail.abc.com,
your email will pass DKIM alignment (the domains “mail.abc.com” match)
if your dkim sigining domain is mail.abc.com and your From domain is abc.com,
your email will NOT pass DKIM alignment (the domains “mail.abc.com” and “abc.com” do not match)

DMARC stands for: Domain-based Message Authentication, Reporting and Conformance.
It is an email authentication standard, developed to combat spoofed domain mail.
Senders:
Receivers:
With some mailbox providers, it influences deliverability in a meaningful way, see:
How dmarc works with Google Mail and Office 365 in 2020 *
“Office 365 is generally responsive to spf and dkim authentication.
The only way to get consistent results, reaching the inbox, is to associate them with dmarc”
* = external website link, will open in a new page
DMARC uses SPF (Sender Policy Framework) and DKIM (Domain Keys Identified Emails)
to control the situation when email fails authentication tests.
SPF requires that you declare which servers you use to send out email messages.
Check how to configure spf to know more and set it correctly.
RealSender smtp servers sign all outgoing email messages with the DKIM signature.
A setup is needed if you want to sign with the same domain of the sender.
Check how to configure dkim to know more.
RealSender provides you a mailbox that collects the dmarc reports generated by the receivers.
_dmarc.example.com. IN TXT "v=DMARC1; p=none; rua=mailto:dmarc.example@rsbox.com"Starting from the next day, you will begin to receive the dmarc rua reports online.
You might discover that you forgot to authenticate an email campaign that’s being deployed from a third party.
If something like that happens, simply authenticate it and check that the next mailing passes the dmarc tests.
When the reports are correct for a few weeks, tell the Mailbox Providers to reject/block those spoofed/phished emails.
The _dmarc TXT record of your domain should be changed to look like this:
"v=DMARC1; p=reject; rua=mailto:dmarc.example@rsbox.com"If your organization implements dmarc, you will need to check carefully
before you introduce any new method of sending email.
Dmarc applies strict policies on how spf and dkim are tested
this can cause emails which would otherwise pass those tests
to be rejected by mailbox providers.
Even if everything is set correctly, the verification may fail:

RealSender collects and analyses the dmarc rua(*) reports for you.
* = rua meaning:
Reporting URI(s) for aggregate data. In RealSender, the “rua” is the email address provided to the customers,
to which aggregate reports are sent by domains
that have received mail claiming to be from your domain.
The reports are generated every day at 13:00 (CET) and contain the data of the last seven days.
This is a dmarc online report, sample page:
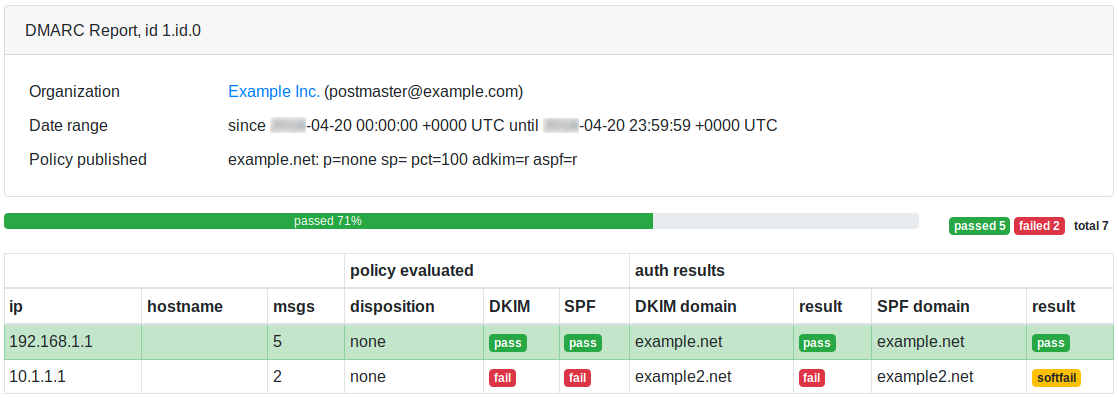
Topics in this area:
detailed reports per month, days, hours, hosts, sender email
emails' logs, Delivery Status Notifications (DSN), Successful delivery notifications
look into the email messages that have been sent to understand what's going on
RealSender offers detailed reports of each smtp server / outgoing emails activity.
The data are updated automatically every five minutes.
On request we can send a weekly summary by email.
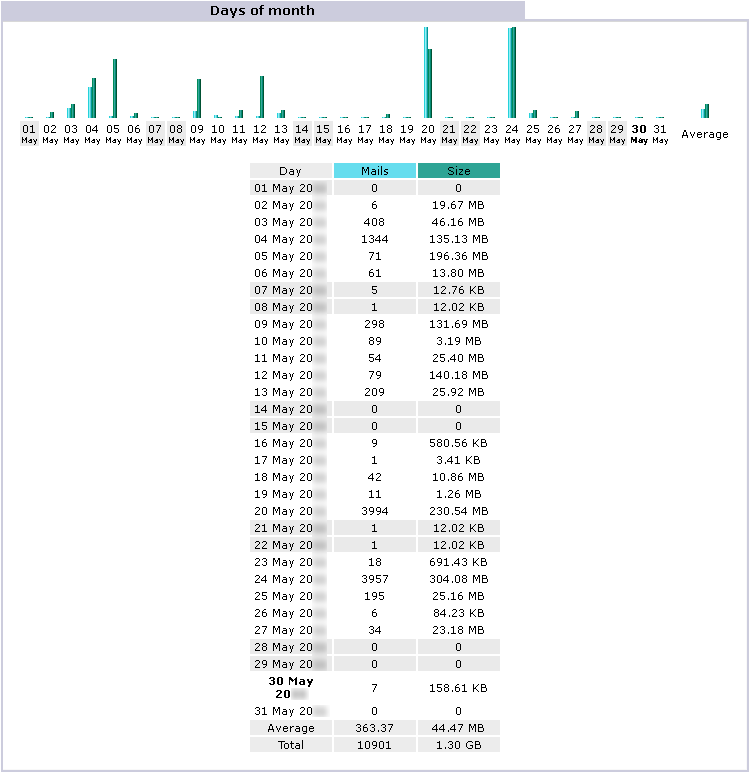
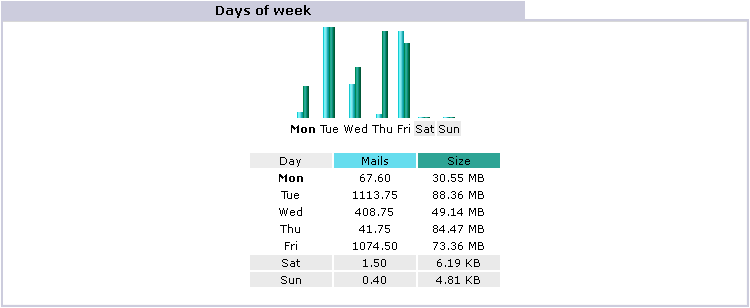
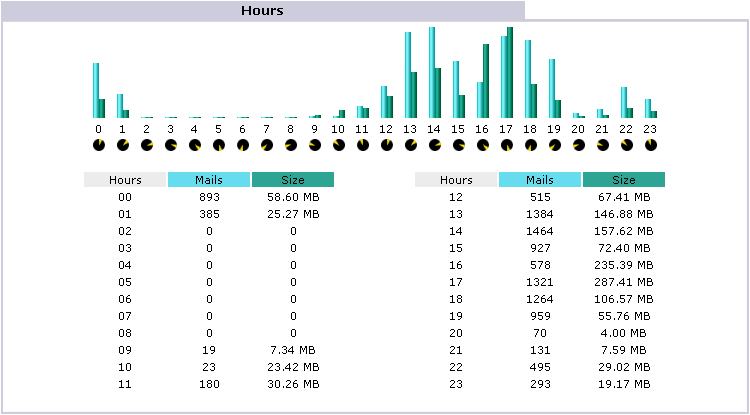
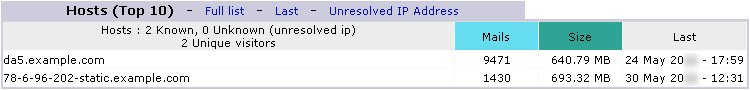
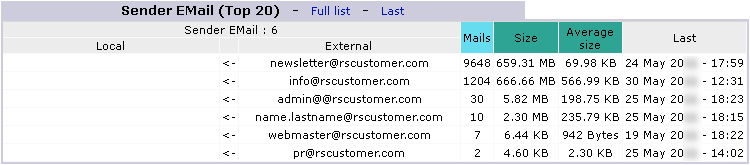
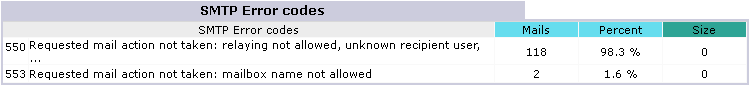
Note: these errors are generated by unauthorized attempts to send emails through the server
RealSender lets you access via browser to the processed emails data:
The displayed data can be saved locally directly from the browser, or automatically registered at regular intervals (eg once a day), to keep a history.
May 31 06:26:22 rs336 v4V4QL1K030027: from=sender@yourcompany.com
May 31 06:26:25 rs336 v4V4QL1K030027: to=recipient@yourcustomer.com, dsn=2.0.0, stat=Sent (Message accepted for delivery)
May 31 08:58:04 rs336 v4V6w3jN001390: from=sender@yourcompany.com
May 31 08:58:05 rs336 v4V6w3jN001390: to=recipient@yourcustomer.com, dsn=4.0.0, stat=Deferred: 421 recipient@yourcustomer.com Service not available - too busy
May 31 09:02:03 rs336 v4V6w3jN001390: to=recipient@yourcustomer.com, dsn=4.0.0, stat=Deferred: 421 recipient@yourcustomer.com Service not available - too busy
May 31 09:12:42 rs336 v4V6w3jN001390: to=recipient@yourcustomer.com, dsn=2.0.0, stat=Sent (Message accepted for delivery)
May 31 10:00:22 rs336 v4V80L9Z004176: from=sender@yourcompany.com
May 31 10:00:24 rs336 v4V80L9Z004176: to=recipient@yourcustomer.com, dsn=4.7.1, stat=Deferred: 451 4.7.1 recipient@yourcustomer.com: Recipient address rejected: Greylisting in effect, please come back later
May 31 10:02:03 rs336 v4V80L9Z004176: to=recipient@yourcustomer.com, dsn=4.7.1, stat=Deferred: 451 4.7.1 recipient@yourcustomer.com: Recipient address rejected: Greylisting in effect, please come back later
May 31 10:12:04 rs336 v4V80L9Z004176: to=recipient@yourcustomer.com, dsn=2.0.0, stat=Sent (Message accepted for delivery)
May 31 16:17:14 rs336 v4VEHCk6017038: from=sender@yourcompany.com
May 31 16:17:15 rs336 v4VEHCk6017038: to=recipient@yourcustomer.com, dsn=5.1.1, stat=User unknown
May 31 16:17:15 rs336 v4VEHCk6017038: v4VEHFk5017041: DSN: User unknown
May 25 12:43:37 rs336 v4PAhZw1019212: from=sender@yourcompany.com
May 25 12:43:38 rs336 v4PAhZw1019212: to=recipient@yourcustomer.com, dsn=5.0.0, stat=Service unavailable
May 25 12:43:38 rs336 v4PAhZw1019212: v4PAhcw0019217: DSN: Service unavailable
May 25 09:17:41 rs336 v4P7Hc6P011481: from=sender@yourcompany.com
May 25 09:17:42 rs336 v4P7Hc6P011481: to=recipient@yourcustomer.com, dsn=4.1.1, stat=Deferred: 452 4.1.1 recipient@yourcustomer.com 4.2.2 mailbox full
[…] the system retries the delivery every ten minutes* […]
May 25 13:25:47 rs336 v4P7Hc6P011481: to=recipient@yourcustomer.com, dsn=4.1.1, stat=Deferred: 452 4.1.1 recipient@yourcustomer.com 4.2.2 mailbox full
May 25 13:25:48 rs336 v4P7Hc6P011481: v4PBPko0020848: sender notify: Cannot send message for 4 hours*
* = see note at the end of the next paragraph
Bounced mails (eg user unknown) return to the sender’s email address or to the return-path address (if specified).
In the event of a delay in the delivery of the messages, you will receive a warning after 30 minutes*, like this:
Subject:
Warning: could not send message for past 30 minutes
Body:
**********************************************
** THIS IS A WARNING MESSAGE ONLY **
** YOU DO NOT NEED TO RESEND YOUR MESSAGE **
**********************************************
[...] The system will automatically retry for four hours*. If you do not receive further notifications, it means that the messsage has been successfully delivered. You can check the details within the logs (see the above mentioned examples).
After four hours* unsuccessfull retries, a definite error will be returned to the sender’s email address or to the return-path address (if specified), like this:
Subject:
Returned mail: see transcript for details
Body:
The original message was received at ...
----- The following addresses had permanent fatal errors -----
<recipient@yourcustomer.com>
----- Transcript of session follows -----
Deferred: Connection timed out with yourcustomer.com.
Message could not be delivered for 4 hours
Message will be deleted from queue
[...] * = when sending bulk mailings:
delayed delivery status notifications are disabled,
the interval between the delivery attempts is increased (from ten to thirty minutes),
the maximum time of permanence in the queue is longer (from four to twenty-four hours)
On request, we can turn on the “delivery notification” for successfully delivered mails too. In this way, for each delivered message, the sender will receive the delivery receipt from the destination server. like the one below. This option is useful for those who need delivery receipts for each mail sent.
Subject:
Return receipt
Body:
The original message was received at ...
----- The following addresses had successful delivery notifications -----
<recipient@yourcustomer.com> (successfully delivered to mailbox)
----- Transcript of session follows -----
<recipient@yourcustomer.com>... Successfully delivered
[...]In rare cases (less than 1% of mails sent), the receipt is not released to the sender. This happens if the recipient has activated a special “privacy / noreceipts” option on his mailserver. This setting is generally not recommended as it also blocks the sending of standard non delivery notifications.

Sometimes, to understand what’s going on, it is necessary to examine the email messages that have been sent.
On request, RealSender may activate the automatic copy of all outgoing emails into a dedicated mailbox.
The mailbox is configured so that it can receive large amounts of emails in a short time with no hassle.
Email messages are automatically deleted after 7 days.
Pay attention: if the messages are sent from personal email accounts (even if they’re company’s accounts),
you need to inform the sender that the communications he sends can be read to perform technical checks.

To verify the correct functioning of the service,
we have activated an automatic control environment.
An external application connects to each SMTP server every ten minutes
and sends a real message. The successful sending of the email allows us to guarantee
the availability and correct functioning of the system.
The result is published on the “status page” of your RealSender server,
freely accessible at the web address: rsXXX-realsender.com/status
The data is displayed in real-time, such as the example data shown below.
The information shown is for the last twenty-four hours.
2024-09-11 06:25:26 UTC
rsXXX- every ten minutes UPTIME CHECK (an email has been successfully sent) - OK
2024-09-11 06:16:18 UTC
rsXXX- every ten minutes UPTIME CHECK (an email has been successfully sent) - OK
2024-09-11 06:05:56 UTC
rsXXX- every ten minutes UPTIME CHECK (an email has been successfully sent) - OK
2024-09-11 05:55:41 UTC
rsXXX- every ten minutes UPTIME CHECK (an email has been successfully sent) - OK
2024-09-11 05:45:57 UTC
rsXXX- every ten minutes UPTIME CHECK (an email has been successfully sent) - OK
2024-09-11 05:35:58 UTC
rsXXX- every ten minutes UPTIME CHECK (an email has been successfully sent) - OK
2024-09-11 05:25:27 UTC
rsXXX- every ten minutes UPTIME CHECK (an email has been successfully sent) - OK
2024-09-11 05:16:30 UTC
rsXXX- every ten minutes UPTIME CHECK (an email has been successfully sent) - OK
2024-09-11 05:05:57 UTC
rsXXX- every ten minutes UPTIME CHECK (an email has been successfully sent) - OK
2024-09-11 04:55:36 UTC
rsXXX- every ten minutes UPTIME CHECK (an email has been successfully sent) - OK
Topics in this area:
click.it: the link tracker with instant email feedback
share your secrets via email - enigma is a secure, one-time use, passwordless link generator
a ready-to-use mailbox that receives any message and keeps it for a limited time
a fake smtp/api service with web gui for testing emails in applications easily
an online check tool to validate SPF and DKIM settings sending an email message
![]()
The free version is fully functional, with some limitations:
The paid version is customized and lets you:

Email is not private or secure. It wasn’t designed with privacy or security in mind.
Anyone who handles your email in transit can read it,
including your ISP, a hacker, or the NSA (U.S. National Security Agency).
End-to-end (e2ee) encryption for email can be used to ensure
that only the sender and the recipient of a message can read the contents.
PGP is the best solution for secure communications with a partner that is
already using it. Asking your counterpart to start using PGP could be hard.
Enigma is an app based on the SnapPass open source project.
It allows you to share secrets in a secure, ephemeral way.
Input a single or multi-line secret, its expiration time and click Generate URL.
Share the one-time use URL with your intended recipient.
Try it out:
enigma.realsender.com

inxbox demo is a ready-to-use temporary mailbox
that receives any message
and keeps it in memory for an hour
!! all received messages are visible to anyone !!pay attention: the associated domain name is different from the previous point

inxsend is a Fake SMTP/API Service
for testing emails in applications easily
by sending all the messages to a single mail serverConfigure the smtp server with the following parameters:
Server Name: inxsend.realsender.com
Port: 25 |or| 2525 |or| 587 (+TLS) |or| 465 (+SSL)
User Name: CDED54
Password: 478DEDUse API access as described in the “sending via api” instructions, with the following parameters:
Server address: (https://) inxsend-api.realsender.com/mail/send
apiuser: CDED54
apipass: 478DEDSend a message to:
[yourname]@inxbox.realsender.com
!! all received messages are visible to anyone !!
(other recipients will be rejected)
Let us know if you’re facing any issue.
Open https://inxbox.realsender.com/monitor and check for reception
(use Google Chrome browser > New Incognito Window or Microsoft Edge browser)
Further information on this mailbox is available at: inxbox demo temporary email.

RealSender offers a free online check tool
to validate your SPF + DKIM settings sending an email message:
During verification, a prefix is added to the subject
if the message is not authenticated correctly.
Details on how it works
are located in the “email authentication basics” area of the website:
email authentication basics :: <spf> check online

Topics in this area:
Mailman 'one-way' list, a special configuration for newsletters or announcements
how to improve the security, performance, and scalability of your SMTP server
you can get the desired data using regex
an easy way protect domains that don't send emails from abuse
why sms text messages are used by businesses
how to handle bounced emails to avoid getting hurt
how to check if my SMTP server is safe
what domain DNS settings are required to send emails
how to manage mailing lists with foresight
how to send newsletters while maintaining list hygiene and recipients interest
how to send private and encrypted emails
how to send and limit Bcc emails: pros, cons, conclusions
how to measure the performance of your email marketing campaigns
what users and mail servers qualify as spam emails
how to regain email control using ready-to-run open source email clients
employee emails: can they be read? can they be backed up? can they be archived?
how to protect business emails from spam
how dmarc works with Google Mail and Office 365 - updated
how DKIM domain alignment affects DMARC authentication
which are the most popular email providers in 2020
how dmarc works with Google Mail and Office 365

In a previous post we explained the pros and cons of using bcc emails,
see: “how to send and limit BCC EMAILS”.
In the conclusions, among the other sentences, we stated:
Use dedicated apps to send mass mailings.
The professional systems have an approval workflow
and step by step control,
they are designed to avoid mistakes.
Summary of this article:
Email marketing platforms can be hard to learn and to support (in case you provide them to your customers).
What we are describing here is the idea to use the open source software “GNU Mailman” to send your mass mailings.
The suggestion comes from our own experience offering the easy to use “copymail app”.
A Mailman “one-way” list is a configuration for newsletters or announcements
where only authorized moderators can post, and members cannot reply to the list.
Here’s how it works:
The user sends the message from their email client or from the webmail to the list’s email address.
He must then approve the delivery, which will be distributed server-side to all subscribers.
The system automatically handles bounces (returned emails) and, if desired, unsubscribes.
Subscriptions must be registered manually.
The service is highly reliable, capable of handling thousands of addresses without difficulty.
Sending relies on RealSender’s or other SMTP servers.
GNU Mailman is a widely used software that most Internet Service Providers offer.
On the interenet there are a few guides that explain how to configure and use it for mass mailings:
The main reference is this document taken from two posts by Barry Warsaw to the mailman-users list:
How do I create a newsletter/announcement/one-way list?
The text explains in detail the main points:
Another article from Stanford University explains how Mailman
can be used to set up a list to be ‘announcement-only’:
How to set up a ‘one-way’ announcement-only or newsletter list - Knowledge article KB00010792
Mailing lists can be discussion-based or announcement-based. Mailman software is written in Python language, before its release the Python community used Majordomo, a Perl-based mailing list manager.
Today, Mark Sapiro is maintaining the stable 2.1 branch,
while Barry Warsaw, concentrates on the new 3.X version.
Two overriding principles that are critical to Mailman’s ongoing success:
In Mailman 2 the developers re-designed the message handling system to ensure that these two principles would always be of prime importance. This part of the system has been stable for at least a decade now, and is one of the key reasons that Mailman is as ubiquitous as it is today.
VERP stands for Variable Envelope Return Path. It is a well-known technique that mailing lists use to unambiguously determine bouncing recipient addresses. When the mailing list gets the bounce, it can do something useful, such as disable the bouncing address or remove it from the list’s membership.
There is a standard format for the bounces, called delivery status notifications. Mailman uses a library that contains dozens of bounce format heuristics, all of which have been seen in the wild during the twenty years of Mailman’s existence.
VERP exploits a requirement of the fundamental SMTP protocol to provide unambiguous bounce detection, by returning such bounce messages to the envelope sender.
This is not the From: field in the message body, but in fact the MAIL FROM value set during the SMTP dialog. This is preserved along the delivery route, and the ultimate receiving mail server is required, by the standards, to send the bounces to this address.
If the Mailman server is mylist@example.org, then the VERP-encoded envelope sender for a mailing list posting sent to anne@example.com will be:
mylist-bounce+anne=example.com@example.org. Bounced emails are sent to the VERP-encoded recipient address. Mailman can then parse the To: header to decode the original recipient as anne@example.com
Using VERP requires that Mailman send out exactly one copy of the message per recipient.
VERP requires a unique MAIL FROM for each recipient, and the only way to do that is to send a unique copy of the message.
This approach also helps prevent the message from being identified as spam.
During the trial period, the default “copymail app” configuration uses a domain provided by us as the Mail From address (also known as the bounce/return-path/envelope address), which is the address to which bounced emails are returned. This Mail From domain is different from the From address domain (the sender address visible to recipients).
Before putting it into production, some changes must be made to the DNS, to authenticate the messages sent with the From domain.
The latest email standards allow you to send authenticated emails using a subdomain as the Mail From address (for example, email.youremaildomain.com) while still being able to use the base domain as the From/Sender address (for example, info@youremaildomain.com). Further details can be found within the email authentication advanced page.
The same situation may occur in other environments. We recommend verifying this with your internet service provider.
Key Benefits:
There are several tools available on the internet; after research, we initially ruled out those that only support the HTTP protocol (Layer 7):
NO Apache
“Oh dear. Take a moment to learn about the technologies you’re dealing with. Email uses SMTP.
Apache uses HTTP. Apache knows absolutely nothing about SMTP. If you want to work with email messages, you’ll need a technology that speaks SMTP.”
– EEAA Commented Aug 18, 2016 at 2:49
NO Caddy
“Caddy cannot proxy TCP, only HTTP over TCP.
Use a reverse proxy that can proxy TCP like Traefik, Nginx, or haproxy, or use this experimental plugin.”
– ElevenNotes Commented Sep 24, 2024
We then focused on the three recommended in the comments: “Traefik, NginX, or HAProxy,” installing and testing them one by one.
Most of the tutorials started with Docker, a platform I wanted to avoid and opt for a simple solution, possibly based on one of the Linux package managers, such as YUM for RPM-based distributions like Fedora and CentOS, or APT (Advanced Package Tool), which is used on Debian-based distributions like Ubuntu and Debian.
After a long search, we found this recent article, which describes the type of installation we were looking for: Setup Traefik as a systemd Service.
One note: you need to change the SELinux settings from “Enforcing” to “Permissive.”
Again, after trying two courses on Udemy, we found this excellent course:
Traefik Crash Course (Without Docker)
We managed to get it working by reproducing the examples provided.
Toward the end of the video, the excellent instructor expressed his complete disapproval of this tool:
Traefik Crash Course - 53:50 Summary.
This discouraged us from further testing, leading us to try something else.
In this case, the installation was simpler, using YUM in short:
yum install epel-release nginx nginx-mod-stream nginx-mod-mail
A note: in SELinux, you need to enable relay:
setsebool -P httpd_can_network_relay 1
For the training, we played it safe, with the same instructor as the previous course:
NginX Crash Course (the first part ends after about an hour and twenty minutes).
The instructor is also NOT convinced about this application, particularly the fact that it acts as both a web server and a reverse proxy:
NginX Crash Course - 1:20:10 Summary.
The report ends with “I’ll pick HAProxy over NginX,” so we decided to try HAProxy as well.
Installation turned out to be the easiest thing ever, as it’s a very common application, available in all Linux package managers, for example: yum install haproxy
We’ve also consulted our trusted instructor: HAProxy Crash Course.
It works, but unfortunately, it’s NOT good for SMTP authentication:
“It’s not possible to configure haproxy this way, because haproxy doesn’t support SMTP at all.”
– lukastribus Commented Aug 17, 2023
At this point, after two weeks of testing, we realized that
it’s better to use a standard SMTP server as a reverse proxy for other SMTP servers.
It does its job, using only the SMTP protocol, properly authenticates connections,
and can forward requests to other SMTP servers via the “smarhost” function.
In Postfix, in main.cf, as
relayhost = [smarthost_address]:port
In Sendmail, in sendmail.mc, as
define(`SMART_HOST',`mail.example.com')
Sometimes you have exported data from your website or business software
containing order information or customer details.
You may have only needed the email address and order date.
One way is to import all the data into Excel, delete the unwanted columns
and export the remaining ones.
This may not work well if the email field also contains the email address description,
for example: “Dave Martin <davemartin@bogusemail.com>”.
It can be cumbersome if you have to repeat the task multiple times
or if you have to explain all the steps to someone else.
A regular expression (shortened as “regex” or “regexp”),
is a sequence of characters that specifies a matching pattern in text.
A very simple case is to locate a word spelled two different ways in a text editor,
the regular expression seriali[sz]e matches both “serialise” and “serialize”.
A more complex situation is the syntax for identifying in the text
an email addresses:
[a-zA-Z0-9._-]+@[a-zA-Z0-9._-]+\.[a-zA-Z0-9_-]+
source: stackoverflow - regex extract email from strings
a date:
\d{4}-\d{2}-\d{1,2}
source: stackoverflow - regex for extracting date from string
Recommended YouTube video
“38 mins well spent, totally worth it” :
How to Match Any Pattern of Text
(from minute 25 the syntax for extracting email addresses is explained)
Cheat sheet for using regular expressions
Regular expressions are generally accepted
within advanced text editors like Notepad++ or Atom.
Free online tools are also available, one of them is:
https://regexr.com - an online service to learn, build & test Regular Expressions.
Web interface explanation:
“Expression” is the field that contains the regex syntax.
“Text” is the content you want to analyze.
“Tools > List” will show the results of the extraction.
Expression:
[a-zA-Z0-9._-]+@[a-zA-Z0-9._-]+\.[a-zA-Z0-9_-]+
Text:
Dave Martin
615-555-7164
173 Main St., Springfield RI 55924
davemartin@bogusemail.com
Charles Harris
800-555-5669
969 High St., Atlantis VA 34075
charlesharris@bogusemail.com
Eric Williams
560-555-5153
806 1st St., Faketown AK 86847
laurawilliams@bogusemail.comTools > List:
$&\n
Result:
davemartin@bogusemail.com
charlesharris@bogusemail.com
laurawilliams@bogusemail.comExpression:
","(.*?)([a-zA-Z0-9._-]+@[a-zA-Z0-9._-]+\.[a-zA-Z0-9_-]+)(.*?)",".*",(\d{2}\.\d{2}\.\d{4})
Text:
"lorem ipsum dolor sit amet","Robert Farrell <rmfarrell@bogusemail.com>","",02.01.2024, ,5379,
"consectetur adipiscing elit","""Mesa, Rene <rmesa@bogusemail.com>""","",04.01.2024, ,20826,
"sed do eiusmod tempor incididunt","Antonio Bugan <antonio@bogusemail.com>","",04.01.2024, ,2856,
"ut labore et dolore magna aliqua","Crawley Down Tennis Club <hello@bogusemail.com>","",05.01.2024, ,4453,Tools > List:
$2,$4\n
Result:
rmfarrell@bogusemail.com,02.01.2024
rmesa@bogusemail.com,04.01.2024
antonio@bogusemail.com,04.01.2024
hello@bogusemail.com,05.01.2024. - Any Character Except New Line
\d - Digit (0-9)
\D - Not a Digit (0-9)
\w - Word Character (a-z, A-Z, 0-9, _)
\W - Not a Word Character
\s - Whitespace (space, tab, newline)
\S - Not Whitespace (space, tab, newline)
\b - Word Boundary
\B - Not a Word Boundary
^ - Beginning of a String
$ - End of a String
[] - Matches Characters in brackets
[^ ] - Matches Characters NOT in brackets
| - Either Or
( ) - Group
Quantifiers:
* - 0 or More
+ - 1 or More
? - 0 or One
{3} - Exact Number
{3,4} - Range of Numbers (Minimum, Maximum)source: github code snippets
Most companies and public bodies register multiple domain names.
Businesses often purchase more than one domain to defend against user error and protect their brands.
Other times to promote events or projects that deserve special visibility.
The numbers can vary from a few dozen domains up to several hundred for a single activity.
They range from about two hundred in a Municipality of a large city, to the thousands of Ferrari and Goldman Sachs.
Up to staggering numbers when you count the total number of registered domains,
which at the end of 2022 reached 350 million domain names, as claimed by Verisign.
Many of these domains are used as a “showcase”. There are no email addresses listed on the website.
Contact requests are generally redirected to forms to be filled in or to social media channels.

The management of email sendings, with the necessary authentications (SPF, DKIM, DMARC, …) is becoming more and more complex.
For this reason, only one domain is usually the one actually used for official external communications via email.
However, the idea of protecting one’s online presence can prove to be a double-edged sword.
Misconfigured “showcase domains” can easily be exploited by malicious actors.
They often abuse the well-known name of the sender, to gain the trust of recipients and demand actions
that expose confidential information or the opening links and attachments.
Recipients are at risk of compromising the security of their systems,
allowing access from the outside to gangs of digital criminals.

The complex authentication systems mentioned above also have their positive sides.
The DMARC protocol was designed to act on fake emails,
to prevent unauthorized individuals or organizations from shipping with our senders.
A quick setup allows you to declare that a given domain is NOT in use,
warning recipients to reject any email from that domain.
It is sufficient to insert a record (single row) in the domain dns with this indication:
_dmarc.yourdomain.com. TXT "v=DMARC1; p=reject"
Whether this rule applies depends on the system receiving the messages.
The good news is that the DMARC protocol has been an approved IETF standard since March 2015.
Most online email services implement it to protect their users.
Messages from “NO-MAIL” domains will be BOUNCED automatically.
In this way, in addition to protecting your company from abuse, you will prevent “old” domains,
that are no longer authorized to send nor authenticated, from being used by mistake.
An email inbox is full of competition for the consumer’s attention,
making it that much harder for businesses to get noticed by their customers and prospects.
Getting someone to read an important email (or even getting them on a phone call)
is becoming more and more difficult.

48% of consumers have more than 50 unread messages in their inbox.
Most consumers refrain from weeding out unread messages, so emails keep piling up.
– source: ZipWhip Why Your Customers Don’t Read Your Emails Anymore (pdf 15 MB)
Some updates are urgent and may be critical. Delivering them by email entails a risk
of the message not being read or landing in the spam folder.
When asked “how many email accounts do you have?” 77% answered “two or more”.
Usually only one is configured on the smartphone.

Calling customers and NOT getting an answer
or having the call go to voicemail,
is becoming increasingly common.
97% of consumers admit to ignoring calls from businesses and unknown numbers.
– source: ZipWhip Why Your Customers Don’t Answer the Phone Anymore (pdf 15 MB)
covid-19 increased the use of electronic devices,
64% of interviewed people declared: “I spend more time on my phone”.

58% of consumers say that texting is the most effective way for businesses to reach them quickly.
– source: ZipWhip State of texting 2021 (pdf 21 MB)
Even in e-commerce, where email is usually required for registration,
some large companies, including Amazon, offer the possibility to register via the mobile number.
It is immediate
Text messages are almost always read, usually seconds after they’re received.
Open rates exceed the 95% threshold (of this 95%, 90% occur within three minutes of delivery).
SMS messages are short and concise, communications are essential and immediate.
It is simple
They don’t need an internet connection to get to their recipient.
It allows your brand to reach demographics that are not well-versed in technology.
The use is similar to video content (fast, instantaneous, that can be said in 160 characters).
It is ubiquitous
SMS is compatible with every mobile phone on the planet, without installing new apps.
The smartphone (or old generation mobile phone) is always at the owner’s side like the wallet and the house keys.
Gives the possibility to interact with a customer wherever he is, through a reliable channel.
It is cheap
SMS messages have a low cost of sending.
The average length of messages sent does not exceed 155 characters (the limit is 160 characters for a single message).
Using texts in combination with phone calls or emails can save time when communicating with customers.
It is interactive
Communication takes place through an “unloaded” channel, it is not “pushed”, it is not “stressed”.
SMS is associated with higher importance, it is more likely to be opened and read. They are also more likely to be answered.
The language of text messaging is simple and encourages interaction. Response rates are up to 45%.
Bounced emails or simply “bounces” are the emails sent automatically
by an MTA (Mail Transfer Agent) to the sender,
to inform that the message was NOT received correctly by the recipient
The subject is usually “Returned mail: see transcript for details”.
The explanatory bounce information, a code with a description, can be found in the content.
The “status-code” should clearly identify the type of error that caused the return
but often the codes and descriptions used by each email service provider
must be analyzed and interpreted to classify the bounce correctly.
Mailing to wrong/inactive recipients is considered a “spammer behaviour”.
If you want to reach the rest of your list, it’s best to stop sending to the “bad” part of it.
Sometimes this is called “list hygiene”.
There are three types of Delivery Status Notification (DSN):
Success - The email has been delivered (notification is sent only if requested by the sender)
Hard Bounce - A permanent error has occurred
Soft Bounce - A temporary error has occurred
hard bounce (status-code 5.XXX.XXX): the email address generated a permanent error
such as “550 5.1.1 … User unknown” or “5.1.2 … Host unknown”
A permanent error indicates that you should never send to that recipient again.
A single bounced message should trigger email address blocking.
soft bounce (status-code 4.XXX.XXX): the email address generated a temporary error
such as “452 4.2.2 … Mailbox full”
A transient error indicates that you can retry delivery in the future.
At least three bounced messages, within a few days of each other, should trigger email address blocking.
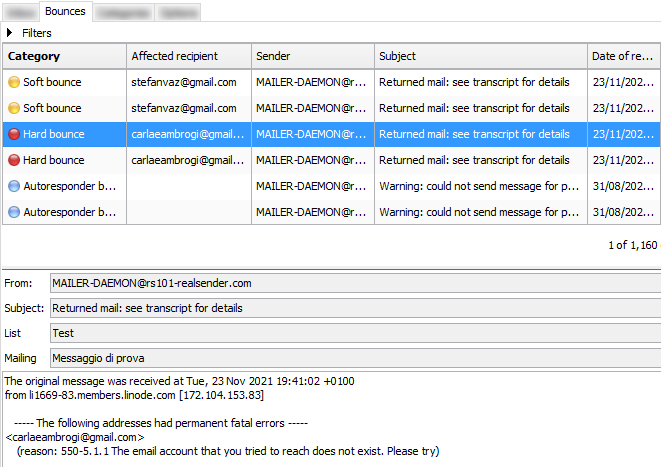
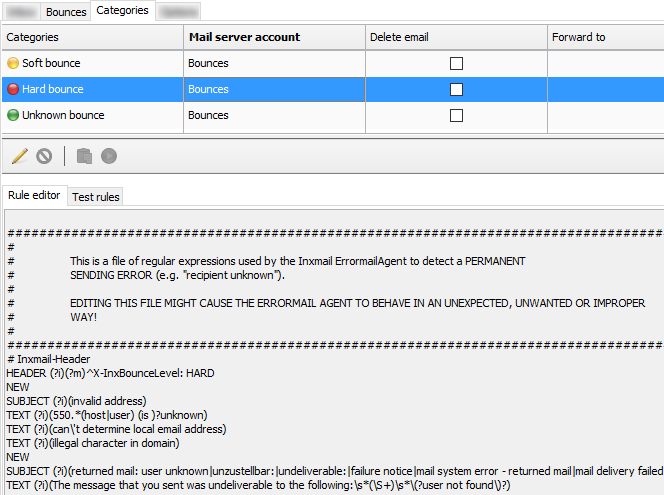
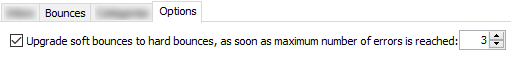
Sometimes a configuration error on both the sender’s side and the recipient’s side
can cause a soft bounce or even a hard bounce.
A good habit is to check the number of bounced messages in the last week
to see if the values are the same as before or if there are any anomalies.
If there is something wrong, you will notice immediately.
Reading the details of the bounces will help you find the cause.
Some systems allow you to define the number of days (eg 180)
after which a subscriber’s bounce information is discarded.
In this way the smtp server will try to contact that recipient again.
Blocks activated by mistake will be cleared automatically
but the reputation of the smtp server can suffer.
In one sentence: prevention is better than cure.
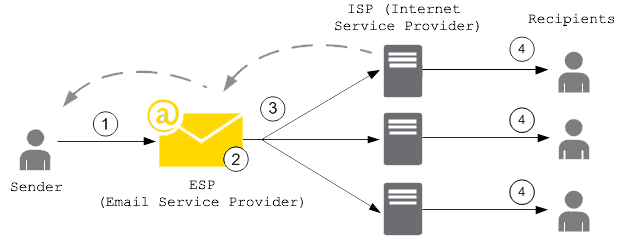
To avoid damage to the reputation of their SMTP servers,
more and more ESPs (Email Service Providers) use an “email suppression list”
that acts before the messages reach the recipient’s mailbox.
When any customer sends an email that results in a hard bounce,
the email address that produced the bounce is added to the suppression list.
The suppression list applies to all the customers. In other words,
if a different customer attempts to send an email to an address that’s on the suppression list,
the SMTP server won’t send it out, because the email address is suppressed.
Using smtp servers with dedicated IP can avoid some issues related to reputation sharing.
For example, the “email suppression list” can only be limited to your IP address,
so that if another customer causes a blacklisting of the smtp server and the related bounces,
your mailings will not be affected.
Status codes used to identify hard bounces and soft bounces have the following syntax:
status-code = class “.” subject “.” detail
Status codes consist of three numeric fields separated by “.”
The sub-code (class) provides a general classification of the status.
The values listed for each class are defined as follows in the RFC 3463 and the RFC 6522:
2.XXX.XXX Success (NOT sent unless requested by the sender)
Success specifies that the DSN is reporting a positive delivery action.
Detail sub-codes may provide notification of transformations required for delivery.
4.XXX.XXX Persistent Transient Failure
A persistent transient failure is one in which the message as sent is valid,
but persistence of some temporary condition has caused abandonment or delay of attempts to send the message.
If this code accompanies a delivery failure report, sending in the future may be successful.
5.XXX.XXX Permanent Failure
A permanent failure is one which is not likely to be resolved by resending the message in the current form.
Some change to the message or the destination must be made for successful delivery.Some code and description examples:
2.0.0: Sent (Message accepted for delivery)
4.2.2: Over quota
4.4.5: Insufficient disk space
5.0.0: Invalid domain name
5.1.1: User unknown
5.7.1: Message content rejectedWith the increasing number of ransomware attacks in the 2020s
email, our main communication channel on the Internet, is it safe?
The SMTP servers are a particularly sensitive infrastructure.
They can spread email messages on our behalf,
that our counterparts accept as coming from trusted senders
because they are correctly authenticated by the sending server.
SMTP servers are a particularly sensitive infrastructure.
They spread email messages on our behalf,
that our counterparts accept as coming from trusted senders
because they are properly authenticated by the sender’s SMTP server.
What happens if someone else uses your SMTP server?
How to check if my SMTP server is safe?
The use of sensitive infrastructures on the Internet
requires a high level of protection to prevent abuse.
If you try to send messages via smtp.gmail.com
you’ll be blocked and receive this “Critical security alert”:
Less secure app blocked
Google blocked the app that you were trying to use
because it doesn't meet our security standards. [...]The only alternative is to use OAuth2, a protocol that doesn’t share password data
but instead uses authorization tokens to prove identity.
The most used mailservers on the Internet (August 2021 data) are:
Exim (58%), Postfix (35%), Sendmail (4%)
To continue using your own mailserver
reducing the risk of being hacked,
the minimum requirements to check are:
accept only secure authentication
username and password must be transmitted via secure connections,
typically port 587+TLS or port 25+TLS or port 465+SSL
plain text sensitive data communications are disabled
there must be a check on the “Mail-From” address (the sender),
only those you have authorized will be able to pass
configure Fail2ban to block all external attacks
to prevent attempts to force your protections.
In particular Fail2ban should block all repeated attempts:
The block usually occurs between three and ten attempts
and bans the source IP for three to twenty-four hours.
It is quite easy to test these points and decide whether or not
your smtp infrastructure requires a security upgrade.
Fail2ban protects your server against BruteForce/DDOS attacks.
It works as if when a stranger knocks on the door,
after a certain number of strokes, the door disappears.

A testimony from Hacker News:
I manage my own mailserver since several years and I think many others here
use solutions like Mail-in-a-box, mailcow, Mailu, etc
Until Corona I never had big problems with my mailserver but in the last weeks
I got very big incoming Traffic - that was too much for my server and i had to manually reboot it every time ...
[...] Edit: I changed my fail2ban settings and found out I was primarily targeted
by brute force attacks which I should be able to protect against with tools like fail2banFail2ban is a log-parsing application that monitors system logs
looking for the symptoms of an automated attack.
When an abuse attempt is located, using the defined parameters,
Fail2ban adds a new rule to the firewall (iptables or firewalld)
to block the IP address of the attacker, either for a set amount of time, or permanently.
Fail2ban can also alert you through email that an attack is occurring.
Fail2ban is primarily focused on SSH attacks, although it can be further configured
to work for any service that uses log files and can be subject to a compromise.
It is widely used. Searching for it on Google, it’s easy to find
configuration examples for protecting mail servers.
What domain DNS settings are required to send emails ?
Email service providers usually require you to verify the sender’s domain
before using their smtp servers. There are two reasons for this:
Prove domain ownership
by managing the DNS, you prove that you control the sender’s domain
this means you are not using someone else’s domain (spoofing)
Sending of authenticated emails
by setting SPF and DKIM authentication, your messages
are recognized by the recipients as coming from a “real” sender
if your domain and your smtp provider have a good reputation
the messages should reach the recipients’ inbox
Summary:
Below there are some of the major providers we checked, in alphabetical order.
At the end of July 2021, we tested the basic settings required to start sending emails.
The verified domain was “emailperfect.com”. It was registred in 2012 and never used to send emails before.
| Provider name | DKIM “From” domain alignment |
SPF “Mail-From” domain alignment |
Notes |
|---|---|---|---|
| Amazon SES | yes (3 CNAME records) | NO (@amazonses.com) | |
| Mailgun | yes (TXT record) | yes (TXT record) | Hotmail and Yahoo delivery check* |
| Mailjet | yes (TXT record) | NO (@mailjet.com) | Hotmail and Yahoo delivery check* |
| RealSender | yes (2 CNAME records) | yes (TXT record) | dedicated IP address |
| Sendgrid | yes (2 CNAME records) | yes (CNAME record) | Hotmail delivery check* |
| Smtp2go | yes (1 CNAME record) | yes (CNAME record) |
* = we sent a message to each of the following mailboxes and noted if anything suggested that we check again:
Gmail, Hotmail, Yahoo, Gmx, Aruba, Tiscali, Exchange Online
In 2021 we consider mandatory that the sender’s domain is authenticated
so that the recipient knows that the sender’s email address has not been forged.
Preemptive authentication checking also greatly reduces the risk of abuse of sending systems.
For this reason we have “deleted” a provider from the list:
It does not require the domain validation before allowing them to send messages.
When sending a message, we are dealing with two domains:
The “domain alignment” requirement is summarized in this sentence:
“when a sender authenticates their email using SPF and/or DKIM,
at least one of the domains must align with the sending From domain”
For DKIM authentication, a CNAME record is easier to implement.
The same result can be achieved by adding a 2048-bit TXT record but it is more complicated.
In addition, delegation of the DKIM record via CNAME allows your provider
to modify its key when necessary for security reasons.
For SPF authentication using a CNAME record means that the Mail-From address
will be a subdomain managed by your email service provider, such as: bounce.your-company-name.org.
The provider will handle both SPF authentication and bounced messages.
TXT record for SPF authentication is the best choice with email servers such as Zimbra or Exchange,
where each sender receives the bounced messages directly.
There is only one TXT record for domain authentication,
it may be difficult to maintain if you manage multiple smtp servers.
The “Internet Protocol address” or “IP address”
is similar to a telephone number on your home phone or mobile device.
Most SMTP services provide “shared” IP addresses to their customers.
Each time a mailing is sent, a different IP address is assigned.
“Dedicated IP address” means that your email sending IP address will not change over time.
This provides great control over the sender’s reputation that cannot be harmed by the use of others.
Not necessarily, because it requires some technical skills.
The company management should be aware that a few changes in the DNS settings
can lead to serious consequences such as:
How to manage mailing lists with foresight ?
First of all: why use a mailing list manager?
CRM systems (such as Salesforce and Microsoft CRM)
and business emails (such as Office 365 and Google Apps Gmail)
they are not suitable for mass mailings.
They were created for one-to-one communication.
Often to avoid abuses they impose daily sending limits.
Many times companies have to send emails to most of their contacts or to some selected groups.
Bulk mailings must be managed with dedicated systems,
capable of processing large amounts of messages and automatic unsubscriptions.
Second step: where to look for these solutions?
The easy answer is to look at “Saas” - Software as a service - offers
(Mailchimp is the most famous system, Inxmail is less known, is used by large companies).
Local installation versus cloud services is always an important choice.
Our reflection is that the local option helps to “regain email control”, which we are promoting.
Even if you decide to use a self-hosted application in the cloud,
this allows you to easily change supplier while maintaining the same solution.
Three osolutions are worth mentioning:
In search of a clean interface, a list-centered solution, easy to maintain
and easy to restore in case of problems, we have considered listmonk as the best choice.
listmonk is a self-hosted, high performance mailing list and newsletter manager.
It comes as a standalone binary and the only dependency is a Postgres database.
This is the original announcement on Hacker News:
knadh on July 12, 2019 [–]
Author here. To give some context on why listmonk was built, at work (regulated financial business),
we have to deliver e-mails, mostly important updates, to 1.5mn+ customers regularly.
We used phpList for the longest time and then tried MailTrain and Sendy before finally deciding to reinvent the wheel
after running into a number of issues, of which, a few important ones are mentioned below.
- Performance. Unreasonably long amounts of time to send out e-mails.
phpList degraded to the point of taking several days to process a campaign.
listmonk can spawn N goroutines (~threads) and push e-mails to multiple SMTP servers.
On a commodity ec2 instance, we're able to send 1.5mn+ e-mails in a couple hours.
- Subscriber imports were extremely slow. Direct integration to keep subscribers in sync with external CRMs was cumbersome.
Direct DB inserts were complicated due to the complex table structures. listmonk imports 10k records/sec into a Postgres DB on a commodity ec2 instance.
- Segmentation. Often, we have to rapidly segment users by custom attributes and conditions and relay an update to them.
listmonk supports SQL expressions to segment users on their attributes that are defined as arbitrary JSON maps (thanks to Postgres JSONB type).
- Unavailability of dynamic templates. listmonk templates support Go template expressions so it's possible to write logic in messages to make them dynamic.Kailash Nadhis a very active developer in the FOSS (Free and Open Source Software) area.
He works at Zerodha, India’s largest stock broker.
The blog of Zerodha’s technical staff is published at zerodha.tech.
Listmonk is well documented for standard use (via web interface) and developers (via api).
The solution is suitable for large lists (up to millions of subscribers) and also for small groups.
Thanks to the Querying and segmenting subscribers feature,
it lets you query and export a selection of subscribers based on their profiles and attributes.
The extracted data can be easily imported in a new targeted mailing list.
It lacks certain important features like email bounce handling.
But it should be available in the next major release:
Bounce processing #166
Bounce processing screenshot preview
We used another Go application in the past: RealSender - DMARC REPORTS.
Source: dmarc-report-converter. It worked immediately with no hassle.
"PostgreSQL database management system with over two decades of development behind it,
is now the most advanced open-source database available anywhere."
-- A Brief History of PostgreSQL - https://www.postgresql.org/docs/9.3/history.htmlWe had a little experience of that when working in the past with Inxmail Professional server installation.
In 2017 Inxmail GmbH announced that they’ll support PostgreSQL only, dropping all the other DBs:
From 1 January 2019, we will focus on the optimal technical basis and discontinue support
for Windows servers as well as MySQL, Oracle and MS SQL Server databases.
This means that we will only offer support for Inxmail Professional based on Linux servers and PostgreSQL.
-- Inxmail Professional licence solution: Changes to our system support
https://www.inxmail.de/files/files/de/downloads/Inxmail-Professional-licence-solution-EN.pdfIt is certainly a good choice and an investment in valuable knowledge for newbies.
Udemy online courses can help with the initial installation and maintenance of PostgreSQL.
Open source has risks: will a recent project, launched in 2019, be maintained in the future?
Nobody knows, maybe in the worst case some other developer will take care of it, but:
Email Deliverability, question and answer:
hemancuso on July 12, 2019 [–]
Projects like this seem like a great idea, but deliverability seems like a big concern
that is hard to measure unless you have a reasonable amount of experience.
What are best practices for using/selecting an ESP
if you were to use a project like this and want to ensure reasonable deliverability?
knadh on July 12, 2019 [–]
Author here. We've been using listmonk in production at our company (regulated financial business)
to deliver e-mail updates including regulatory ones for over 6 months.
We host our own SMTP instances using Postal on EC2 instances and have never had any issues with deliverability.
If it's legitimate e-mail, I don't think it's much of an issue.We agree that sending expected communications to customers should help avoid most delivery issues.
In our experience, the larger the number, the more likely there will be drawbacks.
AWS EC2 servers are often blacklisted in Gmail - all sent messages are delivered to the Spam folder.
RealSender offers dedicated ip smtp servers,
that operate in a reliable and constantly monitored environment.

goberoi on July 13, 2019 [–]
Totally random question: how did you pick the name?
knadh on July 13, 2019 [–]
I can't quite recollect, but I think the thought process was along the lines of
"hassle free, peaceful list management".You can get a working demo installation in minutes using the docker image.
Alternatively ask RealSender a listmonk demo account.
After blacklisting, the customer support of a major anti-spam service often replies:
“please audit your list hygiene to ensure recipients interest in your mailings”.
“list hygiene” and “recipients interest” have many facets:
A - on the MACHINE side - “list hygiene”
well managed subscriptions and unsubscriptions
the subscriber must have validated her/his email address (double opt-in),
recipients should be able to easily and with certainty unsubscribe (opt-out)
send to “active” and fully engaged recipients only
do not repeatedly send to bad / mailbox full recipients
stop sending to inactive recipients, if they do not interact, is a clear signal of no interest
the content must be well paginated (not a single image) and “responsive”, so as to be readable on multiple devices
otherwise, spam filters may block the message before it reaches the recipient’s inbox
make sure the machines recognize who is sending
email authentication allows destination mailservers to identify messages as being sent by trusted senders
B - on the HUMAN side - “recipients interest”
subscribers should expect the content they receive
recipients should be looking forward to your message and appreciating it
user responses should be managed
sometimes something goes wrong or just some recipient needs to communicate with you,
maybe just to tell you that he doesn’t want to receive any more messages, even if there is an unsubscribe link
The points listed above can be easily managed for small lists, with a few hundred recipients.
Often the sender knows them individually, because they are customers or members of an association.
Things get complicated when the list is larger, with thousands of recipients
and there are more people working on the mailings.
In this case it is mandatory to use professional tools.
On the internet there are many professional solutions for email marketing,
the best known internationally is MailChimp
many websites also list MailChimp alternatives.
EmailTrends’ mission is “to take back email control”,
for this reason we suggest an alternative way.
According to W3Techs, WordPress powers 40% of all the websites on the Internet
and it’s the most popular technology on the Entire Internet in Open Source category.


With over 200,000 active installations, Mailpoet
is one of the most used Wordpress plugin for newsletters.
MailPoet is open source software and from the end of 2020
is part of the companies connected to Automattic, the parent company of Wordpress.
Some screenshots may give you an idea of how the various points are met:
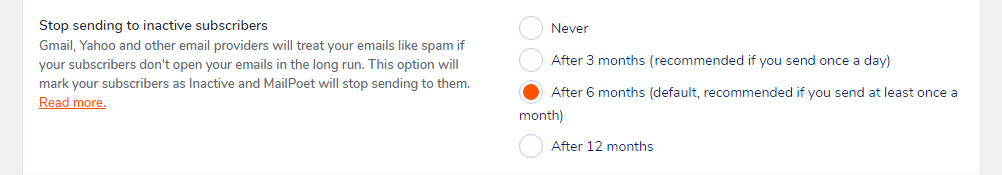
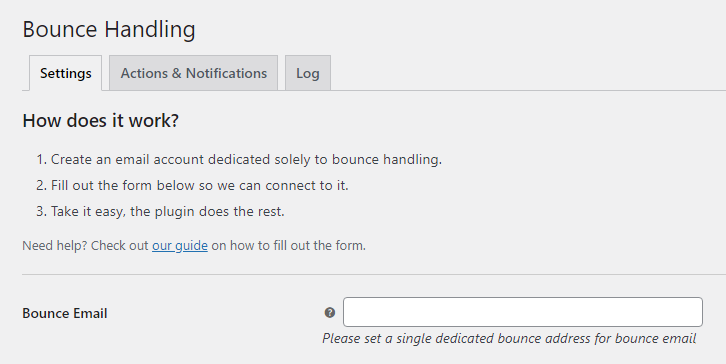
Mailpoet has a “freemium” profit model, which allows you to choose the option:
“I just want the Premium with no sending”.
RealSender dedicated smtp server can be configured via the “Send With… > Other” option.
The “Bounce Handler MailPoet” plugin together with the newsletter mailboxes provided by RealSender
will guarantee the correct authentication of the email messages sent.
The human side is harder to achieve,
it is also the point that makes the difference
when the technical management is not perfect.

“BE RELEVANT”
is a slogan used a few years ago in email marketing.
When you send valuable information to people
you know deeply after talking to them for a long time,
it doesn’t matter how bad the formatting is
or if the message goes to the spam folder.
They will always forgive technical imperfections,
they’ll be waiting for your emails, read them
and click the “not spam” button if necessary.
How to send private and encrypted emails ?
Email is not private or secure.
It wasn’t designed with privacy or security in mind.
Anyone who handles your email in transit can read it,
including your ISP, a hacker, or the NSA (U.S. National Security Agency).
Summary:
“The value of any piece of information is only known when you can connect it
with something else that arrives at a future point in time.
Since you can’t connect dots you don’t have, it drives us into a mode of,
we fundamentally try to collect everything and hang on to it forever.”
“They’ve said it’s just metadata, it’s just metadata, […]
who you’re talking to, when you’re talking to them, where you traveled.
These are all metadata events.
PRISM is about content. […] They can all see it because it’s unencrypted.”
There are dozens of psychological studies that prove
that when somebody knows that they might be watched,
the behavior they engage in is vastly more conformist and compliant.
[…] mass surveillance creates a prison in the mind […]
Scammers might also use malware to infiltrate a company’s computer network
and access email exchanges about financial matters.
Business email compromise (BEC)—also known as email account compromise (EAC)
is one of the most financially damaging online crimes.
In a BEC scam, criminals send an email message that appears to come from a known source
making a legitimate request […]
Anonymity is different from confidentiality
[…] we’re encrypting messages
so that even if people see that we’ve sent a message
they can’t read what it is
but sometimes we don’t even want people to see that we sent a message at all
Internet anonymity is difficult to achieve.
It requires a deep knowledge of the tools you decide to use.
This guide might give you an idea of its complexity:
Private Email Providers
Confidentiality is easier to get.
Even if you have nothing to hide, using encryption
helps protect the privacy of people you communicate with
and makes life difficult for bulk surveillance systems.
If you do have something important to hide, you’re in good company;
these are the same tools that whistleblowers use to protect their identities
while shining light on human rights abuses, corruption and other crimes.
The essential first step is to protect yourself
and make surveillance of your communication as difficult as possible.
End-to-end (e2ee) encryption for email can be used to ensure
that only the sender and the recipients of a message can read the contents.
Without this protection it is easy for network administrators,
email providers and government agencies to read your messages.
Achieving e2ee requires carefulness by both the sender and the recipients.
A single mistake by any of the involved parties can be sufficient to break the security of e2ee.
Email metadata, such as sender email, recipient email, date and time, cannot be protected using e2ee.
The subject of the mail may also remain unprotected and easily readable, even when e2ee is used.
PGP software follows the OpenPGP standard of encryption,
standard (RFC 4880) for encrypting and decrypting data.
PGP encrypts your email body into a code
that only the right person can read.
PGP runs on pretty much any computer or smartphone.
It’s freely licensed and costs no money.
Each user has a unique public key and private key,
which are random strings of numbers.
Your public key isn’t like a physical key, because it’s in an online directory, where people can download it.
People use your public key, along with PGP, to encrypt emails they send to you.
Your private key is more like a physical key, because you keep it to yourself (on your computer).
You use PGP and your private key to decode encrypted emails other people send to you.
If an email encrypted with PGP falls into the wrong hands, it’ll just look like nonsense.
Without the real recipient’s private key, it’s almost impossible to read it.
To protect ourselves form surveillance, we need to learn when to use PGP
and start sharing our public keys whenever we share email addresses.
To use PGP, you’ll need a public key and a private key (known together as a keypair).
Each is a long string of randomly generated numbers and letters that are unique to you.
Your public and private keys are linked together by a special mathematical function.
An application that manages the keys and the encryption/decryption of messages is required,
this is a selection of the most popular ones:
Mailvelope is a free, open source, browser-plugin, available for Mozilla Firefox and Google Chrome,
it’s probably the easiest way to approach PGP
“Mailvelope Demonstration” is a well done tutorial
Mozilla Thunderbird application integrates everything needed to send PGP signed messages
Introduction to End-to-end encryption in Thunderbird
GnuPG is a complete and free implementation of the OpenPGP standard
A Noobs PGP Guide using Gpg4Win [Easy 5 Min Setup] explains how to use it
PGP is the best solution for secure communications with a partner that is already using it.
Asking your counterpart to start using PGP could be hard.
The services that allow you to share a secret only once are an alternative.
When sending something a single time, there are open-source web apps
that allows you to enter information that can only be viewed once.
After the recipient has opened the page, the information is deleted,
and the only thing remaining in your chat logs or email is a bad link.
It’s not as robust as your entire team using PGP, but it’s much easier to set up or explain.
We’ve been able to use it to send login information to fairly non-technical people, and they find it easy to use.
Example (without adding a password):
Let's say you have a password. You want to give it to your coworker, Jane.
You could email it to her, but then it's in her email, which might be backed up,
and probably is in some storage device controlled by the NSA.
If Jane gets a link to the password and never looks at it, the password goes away.
If the NSA gets a hold of the link, and they look at the password... well they have the password.
Also, Jane can't get the password, but now Jane knows that not only is someone looking in her email,
they are clicking on links.Some of these services, all free and opensource, are listed below.
You could also decide to host an instance on your own webserver.
PrivateBin (like a secure version of PasteBin) is developed in PHP
PrivateBin code is published on Github - 3100 stars
PrivateBin instructions are available on a different website
OneTimeSecret is developed in Ruby
OneTimeSecret code and instructions are published on Github - 1200 stars
SnapPass is written in Python. It was originally developed by Pinterest
SnapPass code and instructions are published on Github - 600 stars
How to send and limit Bcc emails ?
“Cc” means “Carbon Copy” in the (old) sense of making a copy
on a typewriter using carbon paper.
The “Bcc:” field in emails (where the “Bcc” means “Blind Carbon Copy”)
contains addresses of recipients of the message
whose addresses are not to be revealed to other recipients of the message.
– IETF rfc 2822 “Internet Message Format”
The difference between Bcc and Cc lies in the privacy of the recipient.
Using the Cc feature, the email addresses in the Cc field
are visible to all the recipients of the email.
A Bcc recipient can see the direct recipient (To:),
he won’t be able to tell who else was Bcc’d in the email.
Bcc is often seen as an easy-to-use mass email distribution system.
Below is a brief analysis of the pros and cons of using Bcc.
At the end of the page, the conclusions with some suggestions.
It’s easy: anyone can use it.
Email is an outgoing gateway without prior checking.
Bcc increases its reach to hundreds or thousands of contacts.
Bcc should be considered a high risk,
potentially dangerous communication tool.
How to measure the performance of your email marketing campaigns?
The following information comes from our fifteen years of experience
with the Inxmail email marketing platform.
What are “email marketing campaigns”?
They are massive permission-based emails,
whose contents are generally customized according to the interests of the recipient,
where the sender can obtain feedback data based on the behavior of the recipients.
The answers or “feedback data” are the basis for the metrics
behind the reports on the performance of email marketing campaigns.
Let’s outline what they are and how they are measured:
The best technical tools are useless if the messages do not reach the recipient’s inbox.
This is where “email deliverability” comes into play:
Permission-based marketing, also called “dialogue marketing”,
is a concept introduced by Seth Godin in 1999 in his best-seller “Permission marketing”.
In the book, it is defined as the opposite of “Interruption marketing”
generally used in traditional mass media such as TV and newspapers.
Aims to create a personal and direct communication,
a relationship between the two parties and activate a “human” dialogue
whose experience is useful and enriching for both.
Depending on the privacy permissions collected, the sender can record:
Aggregated data
they provide global feedback and information on general trends
(e.g. how many opened the email, how many clicked)
Single user data
they allow to obtain individual information
by collecting personal data and then sending personalized messages,
based on previous interactions and user behavior
Link tracking is the activity to replacing the final URL of the website
with a fictitious address, which records the visit and redirects the user to the destination page.
Within email messages, only clicks on links can be tracked.
external images, those that the email client asks for confirmation before downloading,
are treated as links, so you just need to track an external image URL
to know the email opening rate.
Tracking usually only records the “mailid”,
a unique identifier of the mailing that has been sent.
Personalized tracking is achieved by adding to the visited pages
one or more parameters generated by the software,
such as: example.com/test.html?id=54725788327466628654
the “id” parameter refers to a specific user and a particular link in the message.
The information obtained can automatically
update the recipient’s data in the email marketing application
or pass the details on the origin of the click to the web analytics platform.
For example: a travel agency could measure
how many times the user clicks on sea or mountain news,
increasing a specific counter over time.
The data collected will indicate the recipient’s preferred destination.
Open rates are measured by combining data from clicks on tracked links
and “hidden clicks” generated by tracked images that have been downloaded.
If a message is opened in the email client preview,
without downloading the images or clicking on any links,
it is not possible to know that it has been opened.
Since 2003 initially Outlook, then most email clients,
to protect the privacy of their users
began to block the automatic download of images
which otherwise would have been tracked for each email read.
Since 2013, images in Gmail are displayed automatically by default.
The download is performed by a third server, called a “proxy”,
which masks the user’s terminal, but still allows the email marketing operators
to know that the image has been downloaded and the message opened.
Further information can be found here:
How the new Gmail image proxy works and what this means for you
Registration of opening rates is not accurate,
provides a lower value than actual openings.
It is a good idea to measure it anyway,
even just to compare the results of different campaigns.
First of all it is necessary to check if the emails arrive in the mailboxes
of the main freemail domains present in your list
and also in the inbox of the two main suppliers of corporate mailboxes:
Google Apps and Office 365.
Content-activated spam filters are generally triggered by domains present in URLs (http …)
a good tip is to use only one domain in the links of your messages.
The domain should be the same one used in the sender address;
it is called “domain alignment” and reduces the risk related to phishing filters.
For the same reason, if links are tracked, they should use a subdomain
of the domain used in the sender address.
Real tests can be done simply by activating a “seed” mailbox for each email provider,
and then activate the forwarding of messages to your email address.
Send each mailbox a message with the subject “Test Message”
and the content “Test Message” plus the link to your domain.
If the message passes the spam filters, you should receive it in your inbox.
It is normal to receive bounced emails.
The reason may be the presence of abandoned addresses,
full mailboxes or other technical issues.
Depending on the “cleanliness” of your list,
the bounce rate can vary between 5% and 20%.
As the numbers grow, it becomes impossible to manually manage the bounced emails.
Email marketing applications integrate a feature called “bounce handler”
which automatically downloads rejected messages,
it analyzes and classifies them according to their content.
The destination email address is automatically disabled
after a number of “hard bounces”, persistent errors such as user unknown and host unreachable
or after a greater number of “soft bounces”, transient errors such as mailbox full.
It is important to monitor the “bounce rates” (rejected messages)
or the complementary “delivery rates” (messages accepted). Their sum will give 100%.
A change in their value is a symptom that should be investigated.
The biggest email marketing platforms publish benchmark numbers
that are based on the data collected by all their customers.
Technical terms used in the reports:
Here is a short list, most of them refer to the U.S.:
Mailchimp customers range from 1-person startups,
small businesses to “Fortune 500” companies,
the whole spectrum is represented in this data
Campaign Monitor analyzed over 100 billion emails sent globally
between January and December 2020
Return Path eighth annual deliverability benchmark report
to see how many emails were delivered to the inbox, spam, or blocked.
the 2020 Deliverability Benchmark Report (PDF) contents:
What is deliverability and how it’s measured?
What can happen to an email after you hit send?
Globally, how many emails land in the inbox and the spam filter on average
Deliverability statistics for 30 individual countries
What users and mail servers qualify as spam emails ?
Starting from our experience with RealSender,
we have tried to summarize the main points that could affect inbox delivery.
It is useless to evaluate the other points
if the messages are not expected/desired by their recipients.
The sender should put himself in the recipient’s shoes, trying to figure out how an email message will be treated.
User complaints can lead to the blacklisting of the entire smtp server or of the domain name, affecting the delivery of all future messages.
Basic technical settings are required to get email messages accepted.
Use email authentication methods, such as SPF and DKIM, to prove that your emails and your domain name belong together.
The nice side-effect is you help in preventing that your email domain is spoofed.
The only surefire way to see if an email is classified as spam is to…
send it, and see how it shows up on the other side.
How to regain email control using ready-to-run open source email clients ?
Over the past decade, we’ve seen an almost complete change in corporate mailboxes
from on-premises mail servers to cloud services like Exchange Online (Office 365) or Gmail for business (Google Apps).
The main reasons for it are:
In this way, the life of IT professionals has been simplified by offloading
the responsibility to manage the email infrastructure on the “big tech players”.
The risk of abandoning basic email skills, can lead us to think about email
as something that works magically, just because Microsoft and Google handle it.
We can regain email control by breaking down the messaging components and managing them individually:
This creates service isolation and segmentation and tremendously benefits security.
Thus, decreasing the attack surface through isolation/segmentation is considered best practice.
Furthermore, it increases the scalability and stability.
Email clients are the primary interface of mailboxes. They’re a complex piece of software that interacts with users.
There are many solutions available on the market, we have selected them based on two requirements:
We came up with two choices:
 Mozilla Thunderbird is an open-source, cross-platform email client for personal computers. Developed by the Mozilla Foundation.
Mozilla Thunderbird is an open-source, cross-platform email client for personal computers. Developed by the Mozilla Foundation.
It supports both IMAP and POP (storing mail locally on your hard drive so that it can be accessed without an internet connection).
It features excellent mail filter capabilities and management.
Thunderbird has strong support for using multiple accounts and identities, including automated signature features.
It comes with ready-to-install versions for: Windows, Mac OS and Linux. To gain access remotely, users must first connect to their computer.
 The new Rainloop fork, is a simple, modern, lightweight & fast web-based email client.
The new Rainloop fork, is a simple, modern, lightweight & fast web-based email client.
It can handle large number of email accounts without the need of any database connectivity.
It holds both SMTP and IMAP protocols to easily send/receive emails without any trouble.
In 2020, the SnappyMail Github project has been published.
It is the drastically upgraded & secured fork of RainLoop Webmail Community edition.
Here is the SnappyMail email client demo. If you want to try the Admin interface, contact us.
Warning: this is a topic with strong legal implications.
Contact qualified consultants to verify the regulations and their application.The work email is a business work tool
which contains an impressive amount of business-related information.
The companies can do whatever they want with the email,
which is a business work tool, but is it written and read by employees?
Can they read it? Can they backup it? Can they archive it?
Summary:
The work mailbox has an ambivalent nature,
it is a tool owned by the employer, but is used by the employee.
We must distinguish between two different types of business email addresses:
The generic company mailboxes are not problematic at all,
the company checks them, reads all the messages, has no constraints.
The personal mailboxes, such as name.surname@companyname.com,
may contain personal data of the employee that the employer must protect.
If we choose to use this kind of mailbox,
as an employer we need to know which technical standards to adopt
and which tools to use to be able to process the data adequately.
The mailbox can be compared to the company car,
it is made available to the employee for use within the business tasks.
The employer for example can check the mileage, to verify that the employee
has not abused this work tool, using it for personal purposes.
The employer can not, however, monitor systematically and without specific reasons
what the employee does inside the company car.
The mailbox is the equivalent of the company car, a work tool that is owned by the company,
given to the employee to use it use it for work, just to carry out its tasks.
What the employee sends and receives, even during working hours, is like what happens
inside the cockpit of the company car and is equated to private correspondence.
The company cannot read what is written in the email messages,
it cannot be done systematically and without a specific reason.
Even if there is a specific motivation, it can be done only under certain conditions.
Three different interests are at stake, which must be balanced:
The employee must be informed, with adequate written communication, that the email messages
can only be used for all purposes related to the employment relationship, for example by prohibiting personal use.
The document must contain how to use the company tools,
including the email box, and inform that, in compliance with the privacy regulations:
The so-called “massive controls” are prohibited,
such as the systematic reading of the contents of an employee’s mailbox.
Limits in employer control are based on three cardinal principles:
one is good faith, which is the possibility for the employer to carry out a check
on the employee’s company mailbox only if there is a well-founded reason
for example, for the protection of company assets that could be compromised or put at risk by a virus;
or in the case of suspected infidelity of the employee, to carry out defensive checks
the others are proportionality in the control and limitation in time and in the object of the research
The rules require that the employer must prove
to have adopted adequate and effective security measures
to protect company data, such as corporate email archiving.
Access to data by the employer
if carried out in the absence of detailed company information:
represents a very serious violation
sensitive data may be found in the employee’s personal space,
for example information about political, religious, sexual or trade union trends,
which must be guaranteed at the highest level of confidentiality
it is a criminal offense
there is also the risk for all illegally acquired data
to be unusable in any legal process
Business correspondence should generally be kept for a maximum of ten years.
To preserve the company’s assets and to be able to defend itself in any litigation situations.
The storage and processing of personal data is permitted only for a specific purpose.
If this purpose ceases to exist after a certain period of time, for example after ten years, this data must be deleted.
In the event of employee dismissal or resignation,
the name.surname mailbox must be deactivated within a short period of time.
The company can activate an automatic reply informing the sender that the account has been deactivated,
inviting him to write to another internal email address.
The historical archive of company messages of terminated employees
can be kept only if the employee had been informed that his messages were stored.
How to protect business emails from spam ?
It is almost impossible to think about email without considering the issue of spam.
We tried to summarize the current situation and the strategies that can be followed:
A reputable source is SenderBase, now called Talos,
showing about 85% spam email and 15% legitimate email
compared to the email traffic recorded in September 2020.
This percentage has been stable, with little changes in the last twelve months.
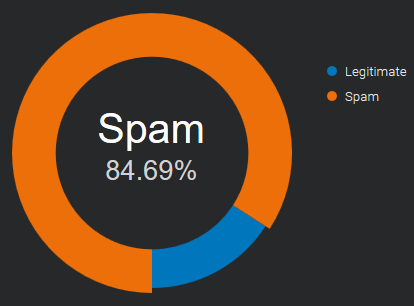
Source: Email & Spam Data - Total global email & spam volume.
Sometimes spam is just for promotional purposes, and the sender
is merely trying to generate more customers for his business,
causing distractions and loss of time. It can fill your inbox
so that it’s difficult to find emails that are important.
Not all spam are friendly promotional emails.
There are many cases where the intentions are malicious, aiming to damage or hijack user systems.
The most common variants of malicious spam worldwide include trojans, spyware, and ransomware.
Imagine your company’s inboxes as your house door:
you have to decide who can come in and who you leave out.
No technique is a complete solution to the spam problem.
Each has trade-offs between incorrectly rejecting legitimate email (false positives)
as opposed to not rejecting of spam (false negatives)
and the associated costs in time, effort, and cost of wrongfully blocking good mail.
Anti-spam techniques can be broken into two areas: prevention and cure.
Restrict the availability of your email addresses, with the goal of reducing the chance of receiving spam.
Discretion
don’t give your email address to everybody
the less known it is, the less spam you will receive
whenever it is possible, use a different email for online registrations
Contact forms
don’t publish your email address online
anybody can see it, “spambots” catch them all the time
to get contacted online, use secure* web forms / contact forms
* = protected by robots that fill them automatically
Once the spammers have your email address, the fight moves to your mail server and inbox.
SpamAssassin-like score systems
They use several spam-detection techniques including DNS based email blacklists
(commonly called Realtime blacklist, DNSBL or RBL), text analysis and Bayesian filtering.
Each test has a score value. The scores can be positive or negative, with positive values indicating “spam” and negative “ham” (non-spam).
The default score threshold for the recipient is “5.0”. If an email score lands higher than the threshold, is marked as spam.
There are a lot of “SpamAssassin Tests” available on the net,
that let the spammers check their messages before sending them.
Powered by users
Users of these systems can flag incoming emails as legitimate or spam and these notations are recorded into a central database.
After a certain number of users mark a particular email as junk, the filter automatically blocks it from reaching the rest of the community’s inboxes.
Sometimes users feedback is integrated with automated controls like the number of interactions with message contents,
as the amount of click on links and the images downloaded, or the count of the occurrences of the same message in multiple mailboxes.
When a collaborative content filtering system involves a large, active user base,
it can quickly block a spam outbreak, sometimes within a matter of minutes.
This kind of filter can hardly be overcome by spammers.
Email Authentication
SPF, DKIM and DMARC are authentication techniques that let you recognize if the from address is really who it claims to be.
In 2020 they’re widely used and they are a good source to identify the trusted senders.
It is important to know in advance the exact domain the emails are coming from,
otherwise it is easy to be misled by the simple change of a letter.
It’s possible for spammers to comply with email authentication
so that their messages look to come from “legitimate senders”.
Authorized senders, whitelist
In a whitelist one can specify a series of trusted addresses or domains.
In the beginning the personal address book and the past received emails will be of great help.
If a sender is in this list, all controls are skipped and the message is received without delays.
This method is easy to implement and very effective when associated with Email Authentication, to avoid email address spoofing*.
* = use of a fake sender to make the message appear from someone other than the actual source
Once your list of trusted contacts is filled, no unknown sender will reach your mailbox.
All unwanted messages can be redirected to a different mailbox to be checked once a day or more rarely.
Spammers will hardly find which are the trusted senders of each recipient.
Even when they do it, email authentication checks will alert you of the fraudulent use.
How dmarc works with Google Mail and Office 365 ? (updated)
We’ve tested again how email authentication affects the delivery
to Google Mail and Office 365 mailboxes, the most popular business emails providers.
The results can be divided into two groups:
(how spf, dkim and dmarc affect the delivery of sent messages)
# Google mail: the emails are always accepted, the spf authentication seems not to be considered at all
Dkim signature is evaluated only if it’s aligned with the From email address and dmarc is set with policy “quarantine” or “reject”.
# Office 365: is fully responsive to spf, when a message passes the spf check, it reaches the Inbox.
Dkim signature is considered only if it’s aligned with the From email address, otherwise it doesn’t matter.
Notes: in the last week of August Office 365 had a strange behavior:
only the messages signed with dkim (signing domain aligned with the From address)
and dmarc record set (with any policy), were delivered to the Inbox
(how spf, dkim and dmarc protect the sender’s email address from being spoofed*)
* = make the message appear from someone other than the actual source
# Google mail: activating dmarc, the spoofed senders get filtered to the Spam folder (with p=quarantine) or rejected (with p=reject).
Nothing happens if the policy is set to “none” (p=none), in this case all the messages reach the Inbox.
# Office 365: “spf fail” or “spf softfail” results, are enough to send the fake senders to the Junk email folder.
the suggested email authentication requirements, are summarized as follows:
| emails delivery | spoofing protection | |
|---|---|---|
| Google Mail | dkim pass (domain aligned) | dmarc set with p=quarantine or p=reject |
| Office 365 | spf pass and dkim pass (domain aligned) | spf set and dmarc set (for added security) |
below there is the full range of tests that have been made
| Google Mail | Google Mail (dmarc set) |
Office 365 | Office 365 (dmarc set) |
||
|---|---|---|---|---|---|
| spf Pass | dkim none | inbox | inbox | inbox | inbox |
| spf Fail | dkim none | inbox | spam | junk | junk |
| spf SoftFail | dkim none | inbox | spam | junk | junk |
| spf none | dkim none | inbox | spam | junk | junk |
| spf Pass | dkim diff | inbox | inbox | inbox | inbox |
| spf Fail | dkim diff | inbox | spam | junk | junk |
| spf SoftFail | dkim diff | inbox | spam | junk | junk |
| spf none | dkim diff | inbox | spam | junk | junk |
| spf Pass | dkim pass | inbox | inbox | inbox | inbox |
| spf Fail | dkim pass | inbox | inbox | inbox | inbox |
| spf SoftFail | dkim pass | inbox | inbox | inbox | inbox |
| spf none | dkim pass | inbox | inbox | inbox | inbox |
| spf Pass | dkim invalid | inbox | inbox | inbox | inbox |
| spf Fail | dkim invalid | inbox | spam | junk | junk |
| spf SoftFail | dkim invalid | inbox | spam | junk | junk |
| spf none | dkim invalid | inbox | spam | junk | junk |
Notes:
How DKIM domain alignment affects DMARC authentication ?
DMARC (Domain-based Message Authentication, Reporting and Conformance),
is an email authentication standard, developed to combat spoofed domain mail.
In the chapter “3.1. Identifier Alignment” it says:
Email authentication technologies authenticate various (and
disparate) aspects of an individual message. For example, [DKIM]
authenticates the domain that affixed a signature to the message,
while [SPF] can authenticate either the domain that appears in the
RFC5321.MailFrom (Mail-From) portion of [SMTP] or the RFC5321.EHLO/
HELO domain, or both. These may be different domains, and they are
typically not visible to the end user.
DMARC authenticates use of the RFC5322.From domain by requiring that
it match (be aligned with) an Authenticated Identifier.
-- https://tools.ietf.org/html/rfc7489#section-3.1It simply means:
when a sender authenticates their email using SPF and/or DKIM,
at least one of the domains must align with the sending From domainIt was not clear to us if a message could fail SPF or DKIM check
and still pass the DMARC authentication.
We tested it using a tool available to everyone: a Gmail mailbox.
To see the outcome, open the message and select “Show original”:
Test 1 - forwarded message: spf-fail, dkim-pass (aligned)
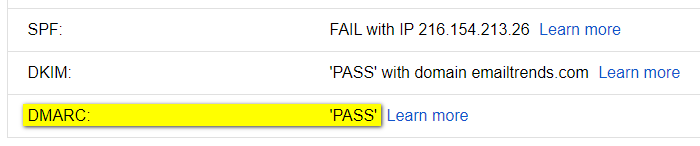
Test 2 - broken dkim key: dkim-fail, spf-pass (aligned)
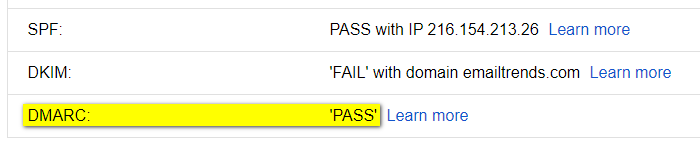
The result is evident, the message passes DMARC authentication if it occurs:
SPF and domain alignment <OR> DKIM and domain alignment
To pass the DMARC check, in some cases it is therefore important to validate the DKIM signature:
the signing domain (d=example.com) must be aligned with the From domain.
Examples of “DMARC-PASS” results that otherwise would not have worked:
Case 1 - forwarding breaks the SPF authentication
SPF-FAIL: SPF Authentication checks will mostly fail,
because a new entity, not included in the original sender’s SPF Record, sends the forwarded email
DKIM-PASS (aligned): Email forwarding does not affect the DKIM signature
Result: DKIM alignment allows the message to pass the DMARC check.
Case 2 - the SPF domain provided by the ESP (Email Service Provider)
CANNOT be aligned with the From domain
SPF~PASS (NOT aligned): SPF Authentication fails domain alignment,
since the domain used by the ESP within the Mail-From address is different by the one in the From sender
DKIM-PASS (aligned): DKIM signature uses the same domain of the From sender
Result: DKIM alignment allows the message to pass the DMARC check.
Which are the most popular email providers in 2020 ?
To monitor email deliverability, it is important to know which email providers your recipients are using.
For B2B world we don’t have precise numbers. The most part of business mailboxes are moving to “Cloud Office Suites”, where the market is divided among “G Suite” and “Office 365”.
Together they cover more than 90% of global business email market share, according to datanyze.com data.
Gathering this information for a single business is quite easy.
From the mx record of the company domain, we can see the email provider being used:
aspmx.l.google.com for “G Suite”
mail.protection.outlook.com for “Office 365”
If your company works in B2B, it is recommended that you regularly monitor a mailbox for each of these two providers.
A third player is Zoho (mx.zoho.com), its market share is around 2% (source: ciodive.com).
With B2C the analysis is more complex. There are no public “email open data” based on the internet traffic.
The only way to get information on email recipients is to extract them from our contact list or to get them by big email service providers. Some of them produce yearly reports to share them with the internet community.
The data below show the top three email providers in twenty-five countries, the information comes from the “2019 Email Benchmark and Engagement Study” published by Sendgrid.
Argentina, Australia, Belgium, Brazil, Canada, Chile, China, Colombia, Denmark, France, Germany, India, Indonesia, Italy, Japan, Mexico, New Zealand, Russia, Saudi Arabia, Spain, South Africa, Sweden, Switzerland, United Kingdom, United States
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| AR | gmail.com | 45.8% | hotmail.com | 33.7% | yahoo.com.ar | 8.2% | 87.7% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| AU | gmail.com | 38.0% | hotmail.com | 18.7% | bigpond.com | 5.4% | 62.1% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| BE | gmail.com | 30.6% | hotmail.com | 23.0% | telenet.be | 9.8% | 63.4% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| BR | gmail.com | 52.9% | hotmail.com | 22.5% | yahoo.com.br | 6.1% | 81.5% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| CA | gmail.com | 38.6% | hotmail.com | 18.8% | yahoo.com | 4.5% | 61.9% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| CL | gmail.com | 67.3% | hotmail.com | 18.2% | yahoo.es | 1.7% | 87.2% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| CN | NetEase (126.com 163.com) | n.a. | Tencent (qq.com) | n.a. | Sina (sina.com) | n.a. | n.a. |
Note: information taken from “Country overview: China” by ReturnPath
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| CO | gmail.com | 41.3% | hotmail.com | 38.7% | yahoo.com | 4.3% | 84.3% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| DK | gmail.com | 35.8% | hotmail.com | 14.0% | live.dk | 3.7% | 53.5% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| FR | gmail.com | 36.0% | hotmail.fr | 9.8% | orange.fr | 8.2% | 54.0% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| DE | gmail.com | 20.8% | gmx.de | 10.0% | web.de | 9.5% | 40.3% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| IN | gmail.com | 82.4% | yahoo.com | 3.4% | yahoo.co.in | 1.6% | 87.4% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| ID | gmail.com | 82.6% | yahoo.com | 7.1% | yahoo.co.id | 1.0% | 90.7% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| IT | gmail.com | 46.8% | libero.it | 9.9% | hotmail.it | 7.2% | 63.9% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| JP | gmail.com | 33.8% | yahoo.co.jp | 12.7% | docomo.ne.jp | 8.6% | 55.1% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| MX | gmail.com | 42.6% | hotmail.com | 31.5% | yahoo.com.mx | 4.0% | 78.1% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| NL | gmail.com | 35.4% | hotmail.com | 19.5% | live.nl | 2.5% | 57.4% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| NZ | gmail.com | 46.3% | hotmail.com | 10.9% | xtra.co.nz | 9.0% | 66.2% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| RU | mail.ru | 34.8% | gmail.com | 22.7% | yandex.ru | 19.6% | 77.1% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| SA | gmail.com | 47.0% | hotmail.com | 31.0% | yahoo.com | 7.8% | 85.8% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| ES | gmail.com | 50.2% | hotmail.com | 25.8% | yahoo.es | 3.8% | 79.8% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| ZA | gmail.com | 65.5% | yahoo.com | 4.1% | hotmail.com | 2.9% | 72.5% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| SE | gmail.com | 33.2% | hotmail.com | 21.0% | live.se | 3.0% | 57.2% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| CH | gmail.com | 25.5% | bluewin.ch | 14.6% | hotmail.com | 10.5% | 50.6% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| UK | gmail.com | 30.8% | hotmail.com | 10.4% | hotmail.co.uk | 9.2% | 50.4% |
| ISO | Provider #1 | % | Provider #2 | % | Provider #3 | % | Total | |
|---|---|---|---|---|---|---|---|---|
| US | gmail.com | 41.9% | yahoo.com | 15.1% | hotmail.com | 5.3% | 62.3% |
How dmarc works with Google Mail and Office 365 in 2020 ?
We’ve tested how email authentication affects the delivery
to Google Mail and Office 365, the most popular business emails providers.
The results can be divided into two groups:
emails delivery
(how spf, dkim and dmarc affect the delivery of sent messages)
Google mail: the emails are always accepted, authentication seems not to be considered at all
Office 365: is generally responsive to spf and dkim. The only way to get consistent results, reaching the inbox, is to associate them with dmarc
spoofing protection
(how spf, dkim and dmarc protect the sender’s email address from being spoofed*)
* = make the message appear from someone other than the actual source
Google mail: combining dmarc and spf (fail or softfail qualifiers), the spoofed senders get filtered to the Spam folder or rejected (depending on your dmarc settings)
Office 365: spf (fail or softfail qualifiers) is enough to send fake senders to the Junk email folder
They are summarized as follows:
| emails delivery | spoofing protection | |
|---|---|---|
| Google Mail | always accepted, authentication is not considered at all | dmarc + spf (fail or softfail) |
| Office 365 | dmarc + spf pass or dmarc + dkim pass | spf (fail or softfail) |
Below there is the full range of tests that have been made.
| Google Mail | Office 365 | |
|---|---|---|
| spf Pass - dkim none | inbox | inbox |
| spf Fail - dkim none | inbox | junk |
| spf SoftFail - dkim none | inbox | junk |
| spf Neutral - dkim none | inbox | inbox |
| spf none - dkim none | inbox | junk |
| spf Pass - dkim pass | inbox | junk* |
| spf Fail - dkim pass | inbox | junk |
| spf SoftFail - dkim pass | inbox | junk* |
| spf Neutral - dkim pass | inbox | junk* |
| spf none - dkim pass | inbox | junk* |
| spf Pass - dkim invalid | inbox | junk |
| spf Fail - dkim invalid | inbox | junk |
| spf SoftFail - dkim invalid | inbox | junk |
| spf Neutral - dkim invalid | inbox | junk |
| spf none - dkim invalid | inbox | junk |
| spf Pass - dkim invalid - dmarc reject | inbox | inbox |
| spf Fail - dkim invalid - dmarc reject | dsn=5.0.0, stat=Service unavailable | junk |
| spf SoftFail - dkim invalid - dmarc reject | dsn=5.0.0, stat=Service unavailable | junk |
| spf Neutral - dkim invalid - dmarc reject | inbox | inbox |
| spf none - dkim invalid - dmarc reject | dsn=5.0.0, stat=Service unavailable | junk |
| spf Pass - dkim pass - dmarc reject | inbox | inbox |
| spf Fail - dkim pass - dmarc reject | inbox | inbox |
| spf SoftFail - dkim pass - dmarc reject | inbox | inbox |
| spf Neutral - dkim pass - dmarc reject | inbox | inbox |
| spf none - dkim pass - dmarc reject | inbox | inbox |
| spf Pass - dkim diff - dmarc reject | inbox | inbox |
| spf Fail - dkim diff - dmarc reject | dsn=5.0.0, stat=Service unavailable | junk |
| spf SoftFail - dkim diff - dmarc reject | dsn=5.0.0, stat=Service unavailable | junk |
| spf Neutral - dkim diff - dmarc reject | inbox | inbox |
| spf none - dkim diff - dmarc reject | dsn=5.0.0, stat=Service unavailable | junk |
Notes: